Determination of signal level for protection of information in case of its interception by technical means of intelligence
DOI:
https://doi.org/10.15587/2706-5448.2023.286193Keywords:
telecommunication, radio engineering, technical protection of information, signal reduction, signal interception, radio intelligenceAbstract
The object of the current paper is the protection of information in the conditions of its interception by technical means of intelligence. According to this goal, considered the existing mathematical model of signal interception using radio-technical intelligence. In course of investigation, for getting final results based existing mathematical model analyzed the optimal scheme of signal detection with the help of intelligence receiver. As a result of this activity occurs four potential cases of signal detection which compared with established threshold H and accompanied by one of two error types: incorrect decision about the signal absence or incorrect indication of its presence. On the basis of the given cases suggested one of the possible variant for protecting of signal that goes beyond the controlled zone.
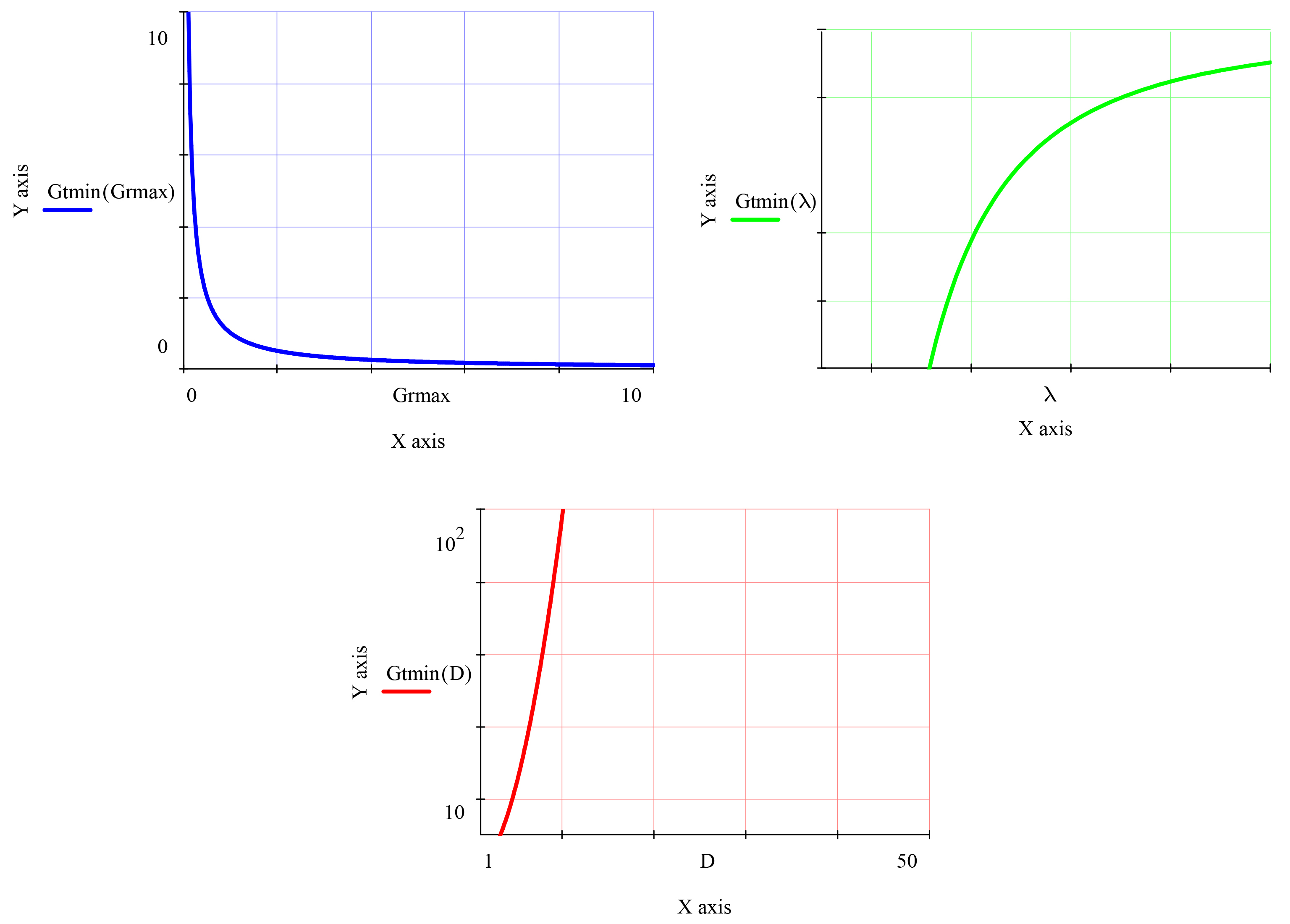
Using such dependencies as: an expression of the power flux density of radio electronic device antenna on its distance to the receiver in the direction of maximum radiation, the formula of signal power at the input of the receiving antenna, the ratio of the antennas coefficient of amplification and its effective scattering area was obtained: the dependence for calculating the power of output signal sufficient for reception within the controlled zone, but insufficient for its interception by technical means beyond its borders. Also, obtained graphical dependencies of minimal coefficient of amplification of transmitter antenna from maximal coefficient of amplification of transmitter antenna, from wavelength of radiation and from distance between transmitter and receiver.
Based on research results formed the conclusion regarding proposed method of information protection based on the mathematical model of the information leakage channel applying for radio intelligence.
References
- Korjik, V., Yakovlev, V., Babkov, I. (1997). The wire-tap channel concept against eavesdropping of indoor radio telephone. Proceedings of 8th International Symposium on Personal, Indoor and Mobile Radio Communications – PIMRC '97. Helsinki, 2, 477–479. doi: https://doi.org/10.1109/pimrc.1997.631047
- Zhao, J., Han, Z., Zhang, H., Liu, R. (2014). The design and implementation of invisible eavesdropping protection application. 2014 12th International Conference on Signal Processing (ICSP). Hangzhou, 2394–2397. doi: https://doi.org/10.1109/icosp.2014.7015423
- Jiang, J., Li, Y., Ma, X., Zhang, P., Fan, Y., Hao, Q. (2017). Research on noise quality in anti-eavesdropping system based on acoustic masking. 2017 International Conference on Wireless Communications, Signal Processing and Networking (WiSPNET). Chennai, 823–827. doi: https://doi.org/10.1109/wispnet.2017.8299876
- Lopez-Risueno, G., Grajal, J., Yeste-Jeda, O. A., Sanz-Osorio, A., Moreno, J. A. (2003). Two digital receivers based on time-frequency analysis for signal interception. 2003 Proceedings of the International Conference on Radar (IEEE Cat. No.03EX695). Adelaide, 394–399. doi: https://doi.org/10.1109/radar.2003.1278774
- Yavorskyy, B. (2004). Detection of low probability of interception signals in bases of almost periodical functions. Proceedings of the International Conference Modern Problems of Radio Engineering, Telecommunications and Computer Science. Lviv-Slavsko, 487–490.
- Xu, X., Jing, T. (2019). Design of Strong Signal Masking Covert Communication Transmission Scheme Based on OFDM System. 2019 IEEE 19th International Conference on Communication Technology (ICCT). Xi'an, 169–173. doi: https://doi.org/10.1109/icct46805.2019.8947096
- Yoon, S., Jeong, J., Jeong, H., Won, Y. (2008). Lawful Interception Scheme for Secure VoIP Communications Using TTP. International Symposium on Computer Science and its Applications. Hobart: TAS, 149–152. doi: https://doi.org/10.1109/CSA.2008.31
- Serkov, A., Tkachenko, V., Kharchenko, V., Pevnev, V., Trubchaninova, K. (2020). A Method to Enhance the Bandwidth and Noise Immunity of IIoT When Exposed to Natural and Intentional Electromagnetic Interference. 2020 IEEE International Conference on Problems of Infocommunications. Science and Technology (PIC S&T). Kharkiv, 527–532. doi: https://doi.org/10.1109/picst51311.2020.9467929
- Siahaeva, O. O. (2012). Doslidzhennia ta rozrobka matematychnoi modeli dzherela nebezpechnoho syhnalu vtraty informatsii v bankivskykh systemakh. Kharkiv, 24.
- Stepanov, M., Boiko, J., Pavlenko, Y. (2023). Determining the required signal level and masking noise to protect information in the conditions of its interception by technical means. Measuring and computing devices in technological processes, 2, 21–27. doi: https://doi.org/10.31891/2219-9365-2023-74-3
Downloads
Published
How to Cite
Issue
Section
License
Copyright (c) 2023 Yevhen Pavlenko

This work is licensed under a Creative Commons Attribution 4.0 International License.
The consolidation and conditions for the transfer of copyright (identification of authorship) is carried out in the License Agreement. In particular, the authors reserve the right to the authorship of their manuscript and transfer the first publication of this work to the journal under the terms of the Creative Commons CC BY license. At the same time, they have the right to conclude on their own additional agreements concerning the non-exclusive distribution of the work in the form in which it was published by this journal, but provided that the link to the first publication of the article in this journal is preserved.







