Modeling relationships in non-commutative two-operand two-bit cet-operations of a double cycle when permuting the operands
DOI:
https://doi.org/10.15587/2706-5448.2024.306980Keywords:
cryptographic coding, low-resource cryptography, CET-operations, asymmetric operations, operands permutation, stream cipheringAbstract
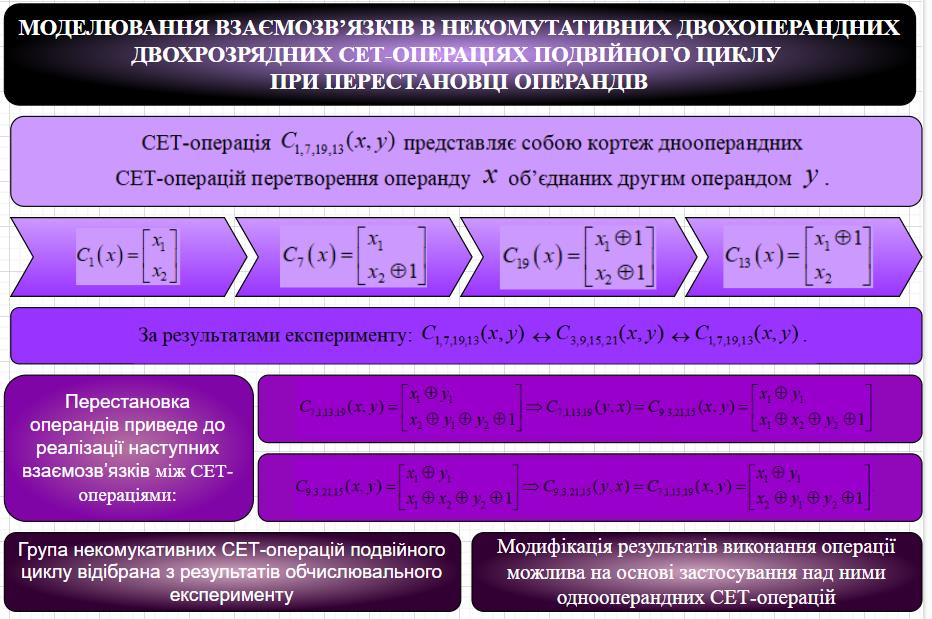
The object of the research is relationships in non-commutative two-operand two-bit CET-operations of a double cycle when operands are permuted. The article is devoted to studying the results of the computational experiment, which is in building a model of relationships in non-commutative two-operand two-bit CET-operations of a double cycle with the operands permutation in order to ensure the possibility of building cryptographic systems with XOR sequence encryption. The theoretical and practical results of the work are obtained on the basis of the computational experiment data. The results of researching the CET-operations data make it possible to build cryptographic systems with XOR sequence ciphering and to improve the quality of low-resource stream encryption systems. The mathematical description of the computational experiment results made it possible to establish relationships between pairs of non-commutative two-operand two-bit CET-operations of a double cycle when operands are permuted. The possibility of constructing a group of commutative two-operand two-bit CET-operations of a double cycle based on the modification of a known two-operand operation by one-operand operations to within the permutation of the crypto-transformation results has been studied. The correctness of constructing a group of CET-operations, both without operand permutation and such that allow operand permutation, has been verified. The model for building a group of asymmetric two-operand two-bit CET-operations of a double cycle, which allow the operands permutation is proposed. Applying the substitution model made it possible to obtain pairs of interrelated operations in this group. The obtained pairs of interconnected operations provide a description of modification for direct and inverse non-commutative CET operations when permuting the operands. The obtained results provide the possibility of building cryptographic systems that encrypt both the input open information under the control of the XOR sequence and the XOR sequence under the control of the input open information. Further research will be aimed at establishing relationships in non-commutative two-operand two-bit CET operations of the triple cycle when operands are permuted.
References
- Avoine, G., Hernandez-Castro, J. (Ed.) (2021). Security of Ubiquitous Computing Systems, Selected Topics. Springer, 265. doi: https://doi.org/10.1007/978-3-030-10591-4
- Zheng, Z., Tian, K., Liu, F. (2023). Modern Cryptography. Vol. 2. А Classical Introduction to Informational and Mathematical Principle. Springer: Singapore. doi: https://doi.org/10.1007/978-981-19-7644-5
- Sabani, M. E., Savvas, I. K., Poulakis, D., Garani, G., Makris, G. C. (2023). Evaluation and Comparison of Lattice-Based Cryptosystems for a Secure Quantum Computing Era. Electronics, 12 (12), 2643. doi: https://doi.org/10.3390/electronics12122643
- Popoola, O., Rodrigues, M., Marchang, J., Shenfield, A., Ikpehia, A., Popoola, J. (2023). A critical literature review of security and privacy in smart home healthcare schemes adopting IoT & blockchain: Problems, Challenges and Solutions. Blockchain: Research and Applications, 100178. doi: https://doi.org/10.1016/j.bcra.2023.100178
- Meng, Y., Zhu, H., Shen, X. (2023). Security in Smart Home Networks. Wireless Networks. Cham: Springer, 167. doi: https://doi.org/10.1007/978-3-031-24185-7
- Amraoui, N., Zouari, B. (2021). Securing the operation of Smart Home Systems: a literature review. Journal of Reliable Intelligent Environments, 8 (1), 67–74. doi: https://doi.org/10.1007/s40860-021-00160-3
- Alghayadh, F., Debnath, D. (2020). A Hybrid Intrusion Detection System for Smart Home Security. 2020 IEEE International Conference on Electro Information Technology (EIT), 319–323. doi: https://doi.org/10.1109/eit48999.2020.9208296
- Zeadally, S., Das, A. K., Sklavos, N. (2021). Cryptographic technologies and protocol standards for Internet of Things. Internet of Things, 14, 100075. doi: https://doi.org/10.1016/j.iot.2019.100075
- Yalamuri, G., Honnavalli, P., Eswaran, S. (2022). A Review of the Present Cryptographic Arsenal to Deal with Post-Quantum Threats. Procedia Computer Science, 215, 834–845. doi: https://doi.org/10.1016/j.procs.2022.12.086
- Aboshosha, B. W., Dessouky, M. M., Elsayed, A. (2019). Energy Efficient Encryption Algorithm for Low Resources Devices. The Academic Research Community Publication, 3 (3), 26–37. doi: https://doi.org/10.21625/archive.v3i3.520
- Zakaria, A. A., Azni, A. H., Ridzuan, F., Zakaria, N. H., Daud, M. (2023). Systematic literature review: Trend analysis on the design of lightweight block cipher. Journal of King Saud University – Computer and Information Sciences, 35 (5), 101550. doi: https://doi.org/10.1016/j.jksuci.2023.04.003
- Thakor, V. A., Razzaque, M. A., Khandaker, M. R. A. (2021). Lightweight Cryptography Algorithms for Resource-Constrained IoT Devices: A Review, Comparison and Research Opportunities. IEEE Access, 9, 28177–28193. doi: https://doi.org/10.1109/access.2021.3052867
- Kumar, C., Prajapati, S. S., Verma, R. K. (2022). A Survey of Various Lightweight Cryptography Block ciphers for IoT devices. 2022 IEEE International Conference on Current Development in Engineering and Technology (CCET). doi: https://doi.org/10.1109/ccet56606.2022.10080556
- Suomalainen, J., Kotelba, A., Kreku, J., Lehtonen, S. (2018). Evaluating the Efficiency of Physical and Cryptographic Security Solutions for Quantum Immune IoT. Cryptography, 2 (1), 5. doi: https://doi.org/10.3390/cryptography2010005
- Manifavas, C., Hatzivasilis, G., Fysarakis, K., Rantos, K. (2014). Lightweight Cryptography for Embedded Systems – A Comparative Analysis. Lecture Notes in Computer Science. Springer, 333–349. doi: https://doi.org/10.1007/978-3-642-54568-9_21
- Yasmin, N., Gupta, R. (2023). Modified lightweight cryptography scheme and its applications in IoT environment. International Journal of Information Technology, 15 (8), 4403–4414. doi: https://doi.org/10.1007/s41870-023-01486-2
- Khudoykulov, Z. (2024). A Comparison of Lightweight Cryptographic Algorithms. Lecture Notes in Networks and Systems. Cham: Springer, 295–304. doi: https://doi.org/10.1007/978-3-031-53488-1_36
- Thabit, F., Can, O., Aljahdali, A. O., Al-Gaphari, G. H., Alkhzaimi, H. A. (2023). Cryptography Algorithms for Enhancing IoT Security. Internet of Things, 22, 100759. doi: https://doi.org/10.1016/j.iot.2023.100759
- Holub, S., Babenko, V., Rudnytskyi, S. (2012). The method of synthesis of the operations of cryptographic transformations on the basis of addition modulo two. Systemy obrobky informatsii, 3 (1), 119–122.
- Babenko, V., Lada, N. (2016). Analiz rezultativ vykonannia modyfikovanykh operatsii dodavannia za modulem dva z tochnistiu do perestanovky. The scientific potential of the present. Vinnytsia: PE Rogalska I.O., 108–111.
- Rudnytskyi, V., Lada, N., Kuchuk, H., Pidlasyi, D. (2024). Architecture of CET-operations and stream encryption technologies. Cherkasy: vydavets Ponomarenko R. V., 374. Available at: https://dndivsovt.com/index.php/monograph/issue/view/22/22
- Rudnytskyi, V., Lada, N., Kozlovska, S. (2018). Technology of two operand operations construction of information cryptographic transformation by modeling results. Advanced Information Systems, 2 (4), 26–30. doi: https://doi.org/10.20998/2522-9052.2018.4.04
- Rudnytskyi, V., Babenko, V., Zhyliaiev, D. (2011). Alhebraichna struktura mnozhyny lohichnykh operatsii koduvannia. Nauka i tekhnika Povitrianykh Syl Zbroinykh Syl Ukrainy, 2 (6), 112–114.
- Babenko, V., Lada, N., Lada, S. (2016). Analiz mnozhyny operatsii syntezovanykh na osnovi dodavannia za modulem dva. Visnyk Cherkaskoho derzhavnoho tekhnolohichnoho universytetu. Seriia: Tekhnichni nauky, 1, 5–11.
- Lada, N., Dzyuba, V., Breus, R., Lada, S. (2020). Synthesis of sets of non-symmetric two-operand two-bit crypto operations within the permutation accuracy. Technology Audit and Production Reserves, 2 (2 (52)), 28–31. doi: https://doi.org/10.15587/2706-5448.2020.202099
- Rudnytskyi, V., Babenko, V., Lada, N., Tarasenko, Ya., Rudnytska, Yu. (2022). Constructing symmetric operations of cryptographic information encoding. Workshop on Cybersecurity Providing in Information and Telecommunication Systems (CPITS II 2021). Kyiv: CEUR Workshop Proceedings, 182–194.
- Rudnytskyi, V. M., Opirskyi, I. R., Melnyk, O. H., Pustovit, M. O. (2018). Synthesis of group operations strong stable cryptographic encode for construction stream cipher. Ukrainian Scientific Journal of Information Security, 24 (3), 195–200. doi: https://doi.org/10.18372/2225-5036.24.13430
Downloads
Published
How to Cite
Issue
Section
License
Copyright (c) 2024 Volodymyr Rudnytskyi, Nataliia Lada, Maksym Herashchenko, Tymofii Korotkyi, Tetiana Stabetska

This work is licensed under a Creative Commons Attribution 4.0 International License.
The consolidation and conditions for the transfer of copyright (identification of authorship) is carried out in the License Agreement. In particular, the authors reserve the right to the authorship of their manuscript and transfer the first publication of this work to the journal under the terms of the Creative Commons CC BY license. At the same time, they have the right to conclude on their own additional agreements concerning the non-exclusive distribution of the work in the form in which it was published by this journal, but provided that the link to the first publication of the article in this journal is preserved.







