Development of strategies for enhancing cybersecurity and digital trust in Azerbaijan’s digital landscape
DOI:
https://doi.org/10.15587/2706-5448.2025.342927Keywords:
cybersecurity, digital trust, phishing attacks, data breach, fraudulent activitiesAbstract
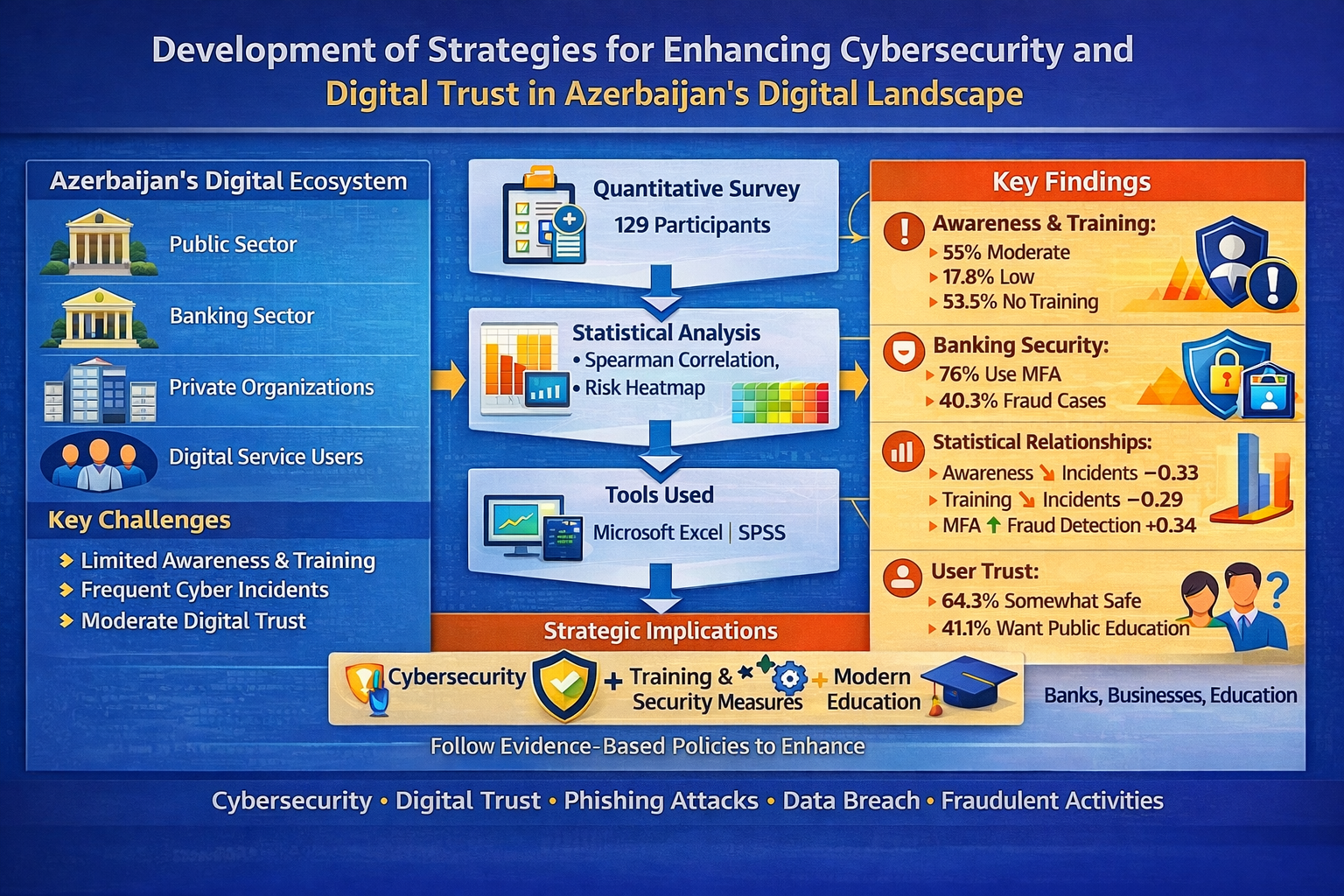
This research focuses on assessing cybersecurity practices and the level of digital trust in Azerbaijan and identifying key weaknesses using real-world data.
The object of the research is cybersecurity practices and digital trust among organizations and users in Azerbaijan.
The research solves the problem of insufficient empirical data on cybersecurity practices and digital trust in Azerbaijan, which contributes to low awareness, weak security implementation, frequent cyber incidents, and limited trust in digital services and legislation.
The research methodology included a quantitative survey of 129 participants, Spearman correlation analysis, and risk heatmap modeling. Data analysis was conducted using a personal computer with Microsoft Excel and (Statistical Package for the Social Sciences) SPSS software.
The results show that 55% of organizations have moderate cybersecurity awareness, 17.8% have low awareness, and 53.5% do not provide cybersecurity training to employees. Although 76% of banks use multifactor authentication (MFA), 40.3% have experienced fraud incidents. Spearman correlation analysis indicates a negative relationship between awareness and cyber incidents (–0.33) and between training and incidents (–0.29), while MFA usage shows a positive correlation with fraud detection (+0.3446). In addition, 64.3% of users feel somewhat safe, and 41.1% identify public education as the most important area requiring improvement.
The findings demonstrate that insufficient training, incomplete adoption of modern protective measures, and weak public education increase cybersecurity risks even in organizations with moderate awareness. The results can support the State Service for Special Communication and Information Security (SSSCIS) in improving the National Cybersecurity Strategy and assist banks, businesses, and educational institutions in strengthening cybersecurity practices for the period 2025–2030.
References
- Maurer, T., Morgus, R. (2014). Compilation of existing cybersecurity and information security related definitions. New America. Available at: https://static.newamerica.org/attachments/175-compilation-of-existing-cybersecurity-and-information-security-related-definitions/OTI_Compilation_of_Existing_Cybersecurity_and_Information_Security_Related_Definitions_Updated122015.pdf
- Hao, X., Li, Y., Ren, S., Wu, H., Hao, Y. (2023). The role of digitalization on green economic growth: Does industrial structure optimization and green innovation matter? Journal of Environmental Management, 325, 116504. https://doi.org/10.1016/j.jenvman.2022.116504
- Kluiters, L., Srivastava, M., Tyll, L. (2022). The impact of digital trust on firm value and governance: an empirical investigation of US firms. Society and Business Review, 18 (1), 71–103. https://doi.org/10.1108/sbr-07-2021-0119
- Uchendu, B., Nurse, J. R. C., Bada, M., Furnell, S. (2021). Developing a cyber security culture: Current practices and future needs. Computers & Security, 109, 102387. https://doi.org/10.1016/j.cose.2021.102387
- Shikhaliyev, R. (2023). Cybersecurity analysis of industrial control systems. Problems of Information Society, 14 (2), 47–54. https://doi.org/10.25045/jpis.v14.i2.06
- Manjikian, M. (2017). Cybersecurity Ethics. Routledge, 246. https://doi.org/10.4324/9781315196275
- Kostopoulos, G. K. (2017). Cyberspace and cybersecurity. Auerbach Publications. https://doi.org/10.1201/9781315116488
- Veríssimo, P., Rodrigues, L. (2001). Fundamental Security Concepts. Distributed Systems for System Architects. Boston: Springer, 377–393. https://doi.org/10.1007/978-1-4615-1663-7_16
- Kim, L.; Hübner, U. H., Mustata Wilson, G., Morawski, T. S., Ball, M. J. (Eds.) (2022). Cybersecurity: Ensuring Confidentiality, Integrity, and Availability of Information. Nursing Informatics. Cham: Springer, 391–410. https://doi.org/10.1007/978-3-030-91237-6_26
- Shah, S. S., Shah, S. A. H. (2024). Trust as a determinant of social welfare in the digital economy. Social Network Analysis and Mining, 14 (1). https://doi.org/10.1007/s13278-024-01238-5
- Herath, S. K., Herath, L. M., Yoo, J. K. (2024). Opportunities and Challenges of Digital Audits and Compliance. Impact of Digitalization on Reporting, Tax Avoidance, Accounting, and Green Finance, 1–35. https://doi.org/10.4018/979-8-3693-1678-8.ch001
- Ablyazov, T., Asaturova, J., Koscheyev, V. (2018). Digital technologies: new forms and tools of business activity. SHS Web of Conferences, 44, 00004. https://doi.org/10.1051/shsconf/20184400004
- Osburg, T. (2019). Changing Relevance of Trust in Digital Worlds. Media Trust in a Digital World, 15–33. https://doi.org/10.1007/978-3-030-30774-5_2
- Huda, M. (2023). Trust as a key element for quality communication and information management: insights into developing safe cyber-organisational sustainability. International Journal of Organizational Analysis, 32 (8), 1539–1558. https://doi.org/10.1108/ijoa-12-2022-3532
- Guo, Y. (2022). Digital Trust and the Reconstruction of Trust in the Digital Society: An Integrated Model based on Trust Theory and Expectation Confirmation Theory. Digital Government: Research and Practice, 3 (4), 1–19. https://doi.org/10.1145/3543860
- PwC UK. Available at: https://www.pwc.co.uk Last accessed: 09.01.2025.
- Tariq, N. (2018). Impact of cyberattacks on financial institutions. Journal of Internet Banking and Commerce, 23 (2), 1–11. Available at: https://www.icommercecentral.com/open-access/impact-of-cyberattacks-on-financial-institutions.pdf
- Rezaei, F. (2019). Iran’s Military Capability: The Structure and Strength of Forces. Insight Turkey, 21 (4), 183–216. Available at: https://www.insightturkey.com/articles/irans-military-capability-the-structure-and-strength-of-forces
- Berglyd, K. J. T. (2022). Strategic Culture and State Behaviour in Cyberspace: How Iran’s Strategic Culture Influences its Behaviour in Cyberspace. [Master's Thesis]. Available at: https://www.duo.uio.no/bitstream/handle/10852/96599/1/STV4992-Master-s-Thesis-Knut-Joachim-Tander–Berglyd-Spring-2022.pdf
- Perwej, Dr. Y., Qamar Abbas, S., Pratap Dixit, J., Akhtar, Dr. N., Kumar Jaiswal, A. (2021). A Systematic Literature Review on the Cyber Security. International Journal of Scientific Research and Management, 9 (12), 669–710. https://doi.org/10.18535/ijsrm/v9i12.ec04
- Saleh, M. E., Aly, A. A., Omara, F. A. (2016). Data Security Using Cryptography and Steganography Techniques. International Journal of Advanced Computer Science and Applications, 7 (6). https://doi.org/10.14569/ijacsa.2016.070651
- Chio, C., Freeman, D. (2018). Machine learning and security: Protecting systems with data and algorithms. O’Reilly Media, 383. Available at: https://virtualmmx.ddns.net/gbooks/MachineLearningandSecurity.pdf
- Carr, M., Shahandashti, S. F.; Hölbl, M., Rannenberg, K., Welzer, T. (Eds.) (2020). Revisiting Security Vulnerabilities in Commercial Password Managers. ICT Systems Security and Privacy Protection. Cham: Springer, 265–279. https://doi.org/10.1007/978-3-030-58201-2_18
- Stobert, E., Biddle, R. (2018). The Password Life Cycle. ACM Transactions on Privacy and Security, 21 (3), 1–32. https://doi.org/10.1145/3183341
- Rizvi, S., Orr, R., Cox, A., Ashokkumar, P., Rizvi, M. R. (2020). Identifying the attack surface for IoT network. Internet of Things, 9, 100162. https://doi.org/10.1016/j.iot.2020.100162
- Borky, J. M., Bradley, T. H. (2019). Protecting Information with Cybersecurity. Effective Model-Based Systems Engineering. Cham: Springer, 345–404. https://doi.org/10.1007/978-3-319-95669-5_10
- Michael, K., Kobran, S., Abbas, R., Hamdoun, S. (2019). Privacy, Data Rights and Cybersecurity: Technology for Good in the Achievement of Sustainable Development Goals. 2019 IEEE International Symposium on Technology and Society (ISTAS). https://doi.org/10.1109/istas48451.2019.8937956
- Chitadze, N. (2023). Basic Principles of Information and Cyber Security. Analyzing New Forms of Social Disorders in Modern Virtual Environments, 193–223. https://doi.org/10.4018/978-1-6684-5760-3.ch009
- Lundgren, B., Möller, N. (2019). Defining Information Security. Science and Engineering Ethics, 25 (2), 419–441. https://doi.org/10.1007/s11948-017-9992-1
- Villalón-Fonseca, R. (2022). The nature of security: A conceptual framework for integral-comprehensive modeling of IT security and cybersecurity. Computers & Security, 120, 102805. https://doi.org/10.1016/j.cose.2022.102805
- Saber, J. A. (2016). Determining small business cybersecurity strategies to prevent data breaches. [Doctoral dissertation; Walden University]. Available at: https://scholarworks.waldenu.edu/dissertations/4991/
- Razikin, K., Soewito, B. (2022). Cybersecurity decision support model to designing information technology security system based on risk analysis and cybersecurity framework. Egyptian Informatics Journal, 23 (3), 383–404. https://doi.org/10.1016/j.eij.2022.03.001
- Abrahams, T. O., Ewuga, S. K., Dawodu, S. O., Adegbite, A. O., Hassan, A. O. (2024). А review of cybersecurity strategies in modern organizations: examining the evolution and effectiveness of cybersecurity measures for data protection. Computer Science & IT Research Journal, 5 (1), 1–25. https://doi.org/10.51594/csitrj.v5i1.699
- Priyadarshini, I.; Le, D., Kumar, R., Mishra, B. K., Khari, M., Chatterjee, J. M. (Eds.) (2019). Introduction on cybersecurity. Cyber security in parallel and distributed computing: Concepts, techniques, applications and case studies, 1–37. https://doi.org/10.1002/9781119488330
- Astani, M., Ready, K. J. (2016). Trends and preventive strategies for mitigating cybersecurity breaches in organizations. Issues in Information Systems, 17 (2). https://doi.org/10.48009/2_iis_2016_208-214
- Paleri, P. (2022). Revisiting National Security: Prospecting Governance for Human Well-Being. Singapore: Springer. https://doi.org/10.1007/978-981-16-8293-3
- Taherdoost, H. (2022). Cybersecurity vs. Information Security. Procedia Computer Science, 215, 483–487. https://doi.org/10.1016/j.procs.2022.12.050
- Mishra, A. (2022). Modern Cybersecurity Strategies for Enterprises: Protect and Secure Your Enterprise Networks, Digital Business Assets, and Endpoint Security with Tested and Proven Methods. BPB Publications, 564. Available at: https://bpbonline.com/products/modern-cybersecurity-strategies-for-enterprises
- Brundage, M., Avin, S., Clark, J., Toner, H., Eckersley, P., Garfinkel, B. et al. (2018). The malicious use of artificial intelligence: Forecasting, prevention, and mitigation. arXiv. https://doi.org/10.48550/arXiv.1802.07228
- Alexei, A., Alexei, A. (2023). The difference between cyber security vs information security. Journal of Engineering Science, 29 (4), 72–83. https://doi.org/10.52326/jes.utm.2022.29(4).08
- Safitra, M. F., Lubis, M., Fakhrurroja, H. (2023). Counterattacking Cyber Threats: A Framework for the Future of Cybersecurity. Sustainability, 15 (18), 13369. https://doi.org/10.3390/su151813369
- Ahmed, S., Khan, M. (2023). Securing the Internet of Things (IoT): A comprehensive study on the intersection of cybersecurity, privacy, and connectivity in the IoT ecosystem. AI, IoT and the Fourth Industrial Revolution Review, 13 (9), 1–17. Available at: https://ru.scribd.com/document/798142114/Securing-the-Internet-of-Things?utm_source
- Al Hayajneh, A., Thakur, H. N., Thakur, K. (2023). The Evolution of Information Security Strategies: A Comprehensive Investigation of INFOSEC Risk Assessment in the Contemporary Information Era. Computer and Information Science, 16 (4). https://doi.org/10.5539/cis.v16n4p1
- Manning, E. (2023). Optimizing Incident Management Processes for Effective Cybersecurity Incident Response. [Master’s thesis; National College of Ireland]. Available at: https://norma.ncirl.ie/7296/
- Manoharan, A., Sarker, M. (2022). Revolutionizing cybersecurity: unleashing the power of artificial intelligence and machine learning for nextgeneration threat detection. International Research Journal of Modernization in Engineering Technology & Science, 4 (12). https://doi.org/10.56726/irjmets32644
- Salem, A. H., Azzam, S. M., Emam, O. E., Abohany, A. A. (2024). Advancing cybersecurity: a comprehensive review of AI-driven detection techniques. Journal of Big Data, 11 (1). https://doi.org/10.1186/s40537-024-00957-y
- Tar, S. J. (2024). Factors That Influence Cybersecurity Risk Management Within the Department of Homeland Security. [Doctoral dissertation; Capitol Technology University].
- Stine, K., Quinn, S., Witte, G., Gardner, R. K. (2020). Integrating Cybersecurity and Enterprise Risk Management (ERM). National Institute of Standards and Technology. https://doi.org/10.6028/nist.ir.8286
- Loi, M., Christen, M. (2020). Ethical Frameworks for Cybersecurity. The Ethics of Cybersecurity, 73–95. https://doi.org/10.1007/978-3-030-29053-5_4
- Ganin, A. A., Quach, P., Panwar, M., Collier, Z. A., Keisler, J. M., Marchese, D. et al. (2017). Multicriteria Decision Framework for Cybersecurity Risk Assessment and Management. Risk Analysis, 40 (1), 183–199. https://doi.org/10.1111/risa.12891
- Cardona, L. A. L. (2021). Technological trends. Ingeniería Solidaria, 17 (1), 1–28. https://doi.org/10.16925/2357-6014.2021.01.02
- Gangwar, S., Narang, V. (2022). A Survey on Emerging Cyber Crimes and Their Impact Worldwide. Research Anthology on Combating Cyber-Aggression and Online Negativity. IGI Global Scientific Publishing, 1583–1595. https://doi.org/10.4018/978-1-6684-5594-4.ch080
- Allende López, M., Da Silva, M. M. (2019). Quantum Technologies: Digital Transformation, Social Impact, and Cross-sector Disruption. Inter-American Development Bank. https://doi.org/10.18235/0001613
- Fukushima, A. (2021). Promises and challenges of digital connectivity. European University Institute. Available at: https://cadmus.eui.eu/entities/publication/e9f6e26a-af6f-514f-8e9e-a36f99888c18
- Source: Statista 2023. ResearchGate. Available at: https://www.researchgate.net/figure/Source-Statista-2023_fig1_373775351
- Uma, M., Padmavathi, G. (2013). A survey on various cyber attacks and their classification. International Journal of Network Security, 15 (5), 390–396. Available at: http://ijns.jalaxy.com.tw/contents/ijns-v15-n5/ijns-2013-v15-n5-p390-396.pdf
Downloads
Published
How to Cite
Issue
Section
License
Copyright (c) 2025 Khayala Alasgarova, Sahib Ramazanov

This work is licensed under a Creative Commons Attribution 4.0 International License.
The consolidation and conditions for the transfer of copyright (identification of authorship) is carried out in the License Agreement. In particular, the authors reserve the right to the authorship of their manuscript and transfer the first publication of this work to the journal under the terms of the Creative Commons CC BY license. At the same time, they have the right to conclude on their own additional agreements concerning the non-exclusive distribution of the work in the form in which it was published by this journal, but provided that the link to the first publication of the article in this journal is preserved.







