Development of a secure storage architecture for digital evidence
DOI:
https://doi.org/10.15587/2706-5448.2025.329386Keywords:
digital forensics, memory dumps, cryptographic protection, cross-platform Python script, file system containers, “read-only” modeAbstract
The object of the study is the process of generating, transmitting, and storing memory dumps within digital forensics. The problem being addressed is the insufficient level of security of existing methods of transmitting and storing digital evidence, which can lead to their compromise, loss of authenticity, and inadmissibility in court proceedings.
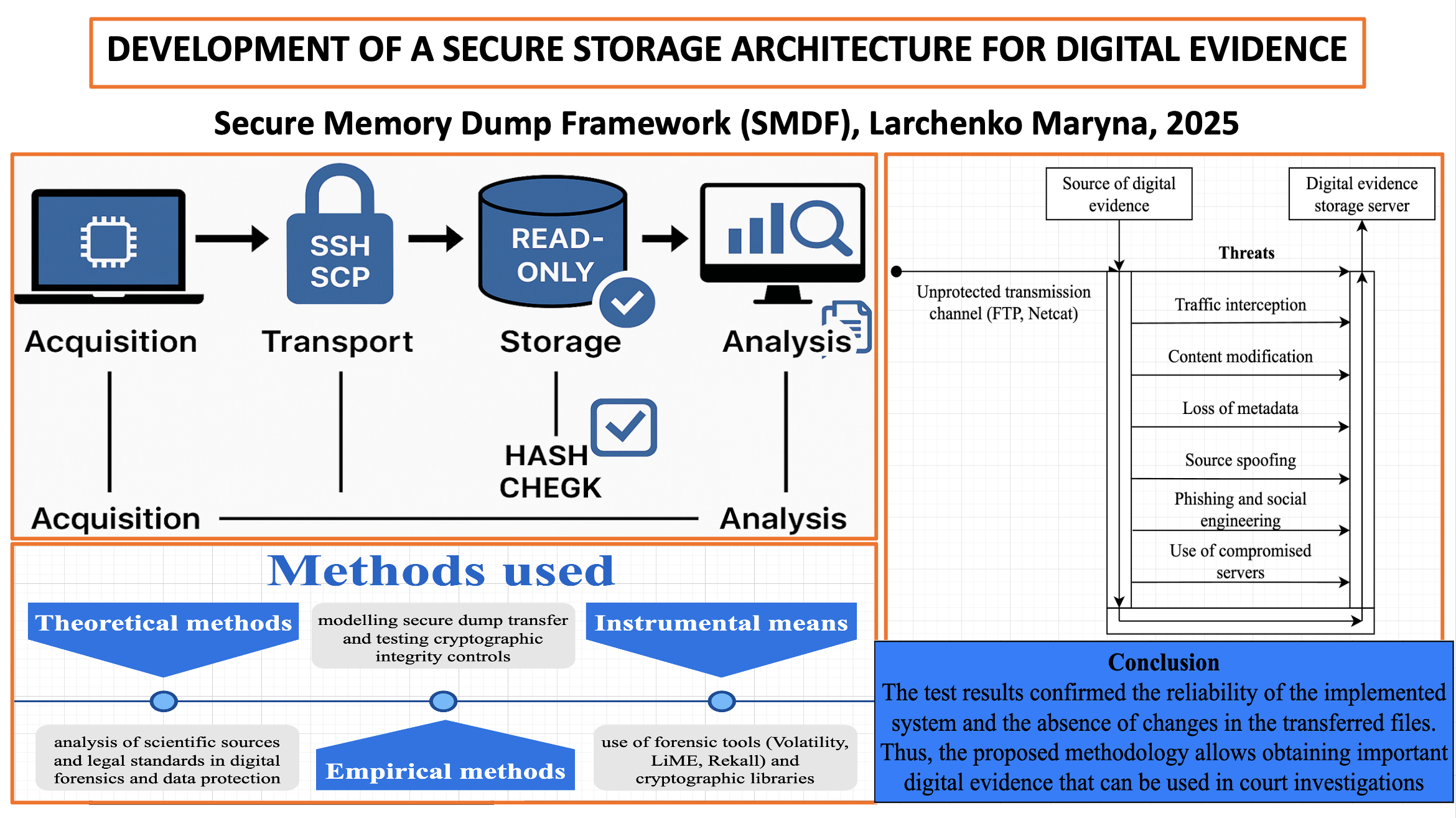
As a result of the conducted research, an architecture for secure storage of digital evidence was developed, providing protection at the stages of acquisition, transportation, storage, and further analysis of memory dumps. A cross-platform Python script for automated memory dump acquisition was proposed, as well as a mechanism for secure transportation of evidence using cryptographic protection through the SCP protocol and authentication. The effectiveness of the combined use of SSH encryption, creation of file system containers in “read-only” mode, mandatory logging of all actions with digital evidence, and an integrated hash-checking mechanism for data integrity verification was demonstrated.
The effectiveness of the proposed approach was assessed based on process modeling in a test environment. In particular, the collected memory dumps were transferred using a custom Python script using a "safe corridor" from the Kali Linux virtual machine to the Caine virtual machine to the created container in "read-only" mode. The integrity of the files after transportation and storage was checked using a hash sum comparison.
A distinctive feature of the proposed model is a comprehensive approach to digital evidence protection, combining technical and organizational measures to ensure the authenticity and integrity of data. This allows solving the problem of compromising digital evidence and guarantees its judicial admissibility. The results obtained are explained by the implementation of cryptographic methods and compliance with digital forensics standards.
The proposed methodology can be used in the practice of law enforcement agencies, forensic experts, as well as in the development of national standards for the preservation of digital evidence. The storage model complies with international security standards and can be adapted to the specific requirements of judicial proceedings in Ukraine.
References
- Avdeeva, G., Żywucka-Kozlowska, E. (2023). Problems of Using Digital Evidence in Criminal Justice of Ukraine and the USA. Theory and Practice of Forensic Science and Criminalistics, 30 (1), 126–143. https://doi.org/10.32353/khrife.1.2023.07
- Romaniuk, V. V., Ablamskyi, S. Ye. (2024). Criteria for the admissibility of digital (electronic) evidence in criminal proceedings. Law and Safety, 93 (2), 140–150. https://doi.org/10.32631/pb.2024.2.13
- Garasymiv, O., Marko, S., Ryashko, O. (2023). Digital evidence: some problematic issues regarding its concept and use in criminal justice. Uzhhorod National University Herald. Series: Law, 2 (75), 158–162. https://doi.org/10.24144/2307-3322.2022.75.2.25
- Sezonov, V. S., Piddybna, A. V. (2021). Problematic issues of collection and use of documents as sources of evidence in criminal proceedings. Scientific Notes of Taurida National V. I. Vernadsky University. Series: Juridical Sciences, 1, 111–119. https://doi.org/10.32838/tnu-2707-0581/2021.1/20
- Slipeniuk, T., Yankovyi, M., Nikitenko, V., Manzhai, O., Tiuria, Y. (2024). Problematic Issues of Using Electronic Evidence in Criminal Proceedings (SDG’s). Journal of Lifestyle and SDGs Review, 4 (1), e01867. https://doi.org/10.47172/2965-730x.sdgsreview.v4.n00.pe01867
- Dodge, A. (2017). The digital witness: The role of digital evidence in criminal justice responses to sexual violence. Feminist Theory, 19 (3), 303–321. https://doi.org/10.1177/1464700117743049
- Watney, M. (2009). Admissibility of Electronic Evidence in Criminal Proceedings: An Outline of the South African Legal Position. Journal of Information, Law & Technology, 1. Available at: http://go.warwick.ac.uk/jilt/2009_1/watney
- Bharati, R., Khodke, P. G., Khadilkar, C. P., Bawiskar, Dr. S. (2024). Forensic Bytes: Admissibility and Challenges of Digital Evidence in Legal Proceedings. International Journal of Scientific Research in Science and Technology, 11 (16), 24–35. https://doi.org/10.2139/ssrn.4896874
- Casey, E. (2011). Digital Evidence and Computer Crime Forensic Science: Computers and the Internet. Academic Press, 837. Available at: https://rishikeshpansare.wordpress.com/wp-content/uploads/2016/02/digital-evidence-and-computer-crime-third-edition.pdf
- Hewling, M., Sant, P. (2012). Digital Forensics: An integrated approach. Conference: CFET At: Canterbury. Available at: https://www.researchgate.net/publication/259055528_Digital_Forensics_An_integrated_approach
- Abulaish, M., Haldar, N. A. H. (2018). Advances in Digital Forensics Frameworks and Tools. International Journal of Digital Crime and Forensics, 10 (2), 95–119. https://doi.org/10.4018/ijdcf.2018040106
- Abulaish, M., Haldar, N. A. H., Jahiruddin, J. (2021). P2DF. International Journal of Digital Crime and Forensics, 13 (6), 1–15. https://doi.org/10.4018/ijdcf.288547
- Hyder, M. F., Arshad, S., Arfeen, A., Fatima, T. (2022). Privacy preserving mobile forensic framework using role‐based access control and cryptography. Concurrency and Computation: Practice and Experience, 34 (23). https://doi.org/10.1002/cpe.7178
- Vaddi, K. S., Kamble, D., Vaingankar, R., Khatri, T., Bhalerao, P. (2024). Enhancements in the world of digital forensics. IAES International Journal of Artificial Intelligence (IJ-AI), 13 (1), 680. https://doi.org/10.11591/ijai.v13.i1.pp680-686
- Kozak, Ye. В. (2021). Organization of a secure data transmission interface based on the M-ary algorithm “tree-based oram”. Scientific Notes of Taurida National V. I. Vernadsky University. Series: Technical Sciences, 4, 84–89. https://doi.org/10.32838/2663-5941/2021.4/13
- Abbas, T., Altaher, A. (2021). Identifying Digital Forensic Frameworks Based on Processes Models. Iraqi Journal of Science, Special Issue, 249–258. https://doi.org/10.24996/ijs.2021.SI.1.35
- Kasper, A. (2015). Multi-level analytical frameworks for supporting cyber security legal decision making. [Doctoral Thesis; Estonian Business School]. Available at: http://ebs.ee/en/research-and-doctoral-studies/publications/phd-theses
- Joseph, D. P., Viswanathan, P. (2022). A Comprehensive Survey and Analysis on Multi-Domain Digital Forensic Tools, Techniques and Issues. https://doi.org/10.21203/rs.3.rs-1988841/v1
- Saharan, S., Yadav, B. (2022). Digital and Cyber Forensics: A Contemporary Evolution in Forensic Sciences. Crime Scene Management within Forensic Science. Crime Scene Management within Forensic Science, Forensic Techniques for Criminal Investigations, 267–294. https://doi.org/10.1007/978-981-16-6683-4_11
- Kapade, P., Pandey, A. K. (2018). Technical issues & challenges in memory forensics. International Journal of Creative Research Thoughts (IJCRT), 6 (2), 1617–1621. Available at: https://ijcrt.org/papers/IJCRT1812859.pdf
- Nyholm, H., Monteith, K., Lyles, S., Gallegos, M., DeSantis, M., Donaldson, J., Taylor, C. (2022). The Evolution of Volatile Memory Forensics. Journal of Cybersecurity and Privacy, 2 (3), 556–572. https://doi.org/10.3390/jcp2030028
Downloads
Published
How to Cite
Issue
Section
License
Copyright (c) 2025 Maryna Larchenko

This work is licensed under a Creative Commons Attribution 4.0 International License.
The consolidation and conditions for the transfer of copyright (identification of authorship) is carried out in the License Agreement. In particular, the authors reserve the right to the authorship of their manuscript and transfer the first publication of this work to the journal under the terms of the Creative Commons CC BY license. At the same time, they have the right to conclude on their own additional agreements concerning the non-exclusive distribution of the work in the form in which it was published by this journal, but provided that the link to the first publication of the article in this journal is preserved.







