Development of a fuzzy risk assessment model for information security management
DOI:
https://doi.org/10.15587/2706-5448.2025.334954Keywords:
information activity, risk, intellectual system, fuzzy logic, artificial neural networkAbstract
The object of research is the process of assessing information security risks of information resources during the functioning of information activity objects, which is the basis of effective security management.
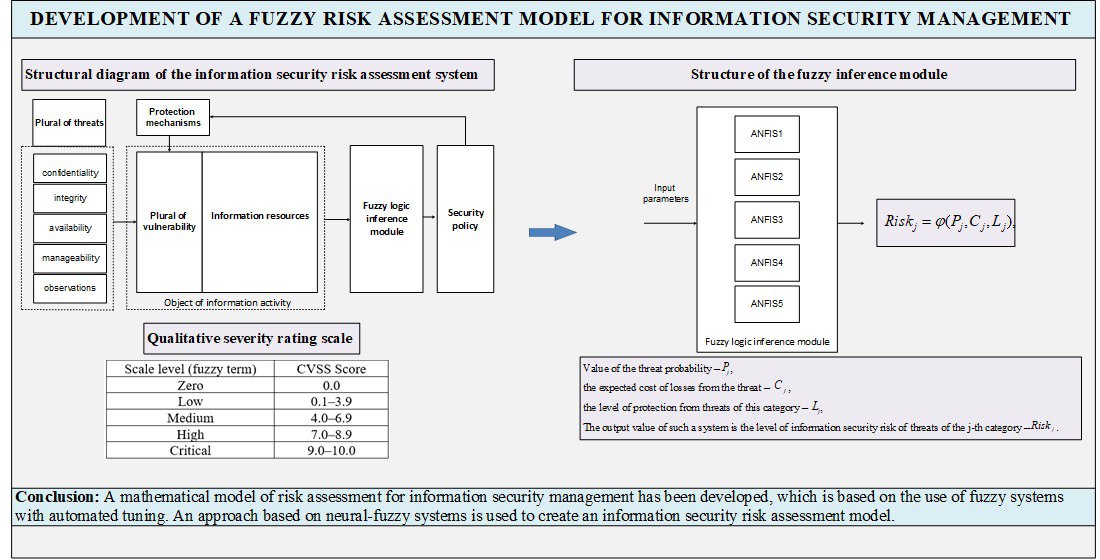
One of the most problematic areas of classical probabilistic risk assessment models is high subjectivity in determining quantitative values of indicators. To eliminate these shortcomings, it is proposed to create universal, scalable and trainable risk assessment models based on qualitative characteristics. The study used an adaptive neuro-fuzzy logical inference system (ANFIS).
A mathematical model of information security risk assessment was obtained, which expands existing solutions by scaling. The approach used in the model allows to automatically adapt to dynamic changes in the functioning of the information activity object. The proposed model has the following features: automated generation of the rule base and retraining of the fuzzy system. The use of artificial neural networks to automate the adjustment of the parameters of the fuzzy system allows to avoid the subjectivity characteristic of expert assessments. This provides the ability to obtain current values of the information security risk level.
The conducted experimental studies quantitatively confirmed the effectiveness of the model, which demonstrated classification accuracy of up to 95% and a significant reduction in the mean square error to 0.01 compared to classical probabilistic models and traditional fuzzy expert systems. This is due to the fact that the proposed model has a number of features, in particular, automated generation of the rule base and the possibility of retraining the fuzzy system, which is provided by the use of artificial neural networks. Due to this, automatic adaptation to dynamic changes in the object and accurate obtaining of current values of the risk level are ensured. Compared to similar known models, this provides automated adjustment of parameters based on the results of retraining (with an error of > 1–2%) and reliable information security management by prioritizing protective measures and responding promptly to threats.
References
- Onyshchenko, V., Onyshchenko, S., Maslii, O., Maksymenko, A.; Onyshchenko, V., Mammadova, G., Sivitska, S., Gasimov, A. (Eds.) (2023). Systematization of Threats to Financial Security of Individual, Society, Business and the State in Terms of the Pandemic. Proceedings of the 4th International Conference on Building Innovations. ICBI 2022.Lecture Notes in Civil Engineering. Cham: Springer, 749–760. https://doi.org/10.1007/978-3-031-17385-1_63
- Onyshchenko, S., Hlushko, A., Laktionov, O., Bilko, S. (2025). Technology for determining weight coefficients of components of information security. Naukovyi Visnyk Natsionalnoho Hirnychoho Universytetu, 1, 96–103. https://doi.org/10.33271/nvngu/2025-1/096
- ISO/IEC 27005:2022 Information security, cybersecurity and privacy protection – Guidance on managing information security risks (2022). International Organization for Standardization. Available at: https://www.iso.org/standard/80585.html
- ISO/IEC TS 27008:2019 Information technology – Security techniques – Guidelines for the assessment of information security controls (2019). International Organization for Standardization. Available at: https://www.iso.org/standard/67397.html
- Risk Management Framework for Information Systems and Organizations: A System Life Cycle Approach for Security and Privacy (2018). NIST Special Publication 800-37, Revision 2. National Institute of Standards and Technology. https://doi.org/10.6028/nist.sp.800-37r2
- Onyshchenko, S., Bilko, S., Yanko, A., Sivitska, S.; Onyshchenko, V., Mammadova, G., Sivitska, S., Gasimov, A. (Eds.) (2023). Business Information Security. Proceedings of the 4th International Conference on Building Innovations. ICBI 2022. Lecture Notes in Civil Engineering. Cham: Springer, 769–778. https://doi.org/10.1007/978-3-031-17385-1_65
- Live Threat Map (2025). Radware. Available at: https://livethreatmap.radware.com/
- Svistun, L., Glushko, А., Shtepenko, K. (2018). Organizational Aspects of Development Projects Implementation at the Real Estate Market in Ukraine. International Journal of Engineering & Technology, 7 (3.2), 447–452. https://doi.org/10.14419/ijet.v7i3.2.14569
- Qi, R., Tao, G., Jiang, B. (2019). Fuzzy System Identification and Adaptive Control. Communications and Control Engineering. Cham: Springer. https://doi.org/10.1007/978-3-030-19882-4
- Onyshchenko, S., Haitan, O., Yanko, A., Zdorenko, Y., Rudenko, O. (2024). Method for detection of the modified DDoS cyber attacks on a web resource of an Information and Telecommunication Network based on the use of intelligent systems. Proceedings of the Modern Data Science Technologies Workshop (MoDaST 2024). Lviv-Shatsk, 219–235. Available at: https://ceur-ws.org/Vol-3723/paper12.pdf
- Sinha, S., Paul, A. (2020). Neuro-Fuzzy Based Intrusion Detection System for Wireless Sensor Network. Wireless Personal Communications, 114 (1), 835–851. https://doi.org/10.1007/s11277-020-07395-y
- Zdorenko, Y., Lavrut, O., Lavrut, T., Lytvyn, V., Burov, Y., Vysotska, V. (2021). Route selection method in military information and telecommunication networks based on ANFIS. Proceedings of the 3rd International Workshop on Modern Machine Learning Technologies and Data Science (MoMLeT+DS). Lviv-Shatsk, 514–524. Available at: https://ceur-ws.org/Vol-2917/paper36.pdf
- Onyshchenko, S., Hlushko, A., Kivshyk, O., Sokolov, A. (2021). The shadow economy as a threat to the economic security of the state. Economics of Development, 20 (4), 24–30. https://doi.org/10.57111/econ.20(4).2021.24-30
- Afravi, M., Kreinovich, V.; Ceberio, M., Kreinovich, V. (Eds.) (2020). Fuzzy Systems Are Universal Approximators for Random Dependencies: A Simplified Proof. Decision Making under Constraints. Cham: Springer, 276, 1–5. https://doi.org/10.1007/978-3-030-40814-5_1
- Hashimov, E., Khaligov, G. (2024). The issue of training of the neural network for drone detection. Advanced Information Systems, 8 (3), 53–58. https://doi.org/10.20998/2522-9052.2024.3.06
- Abdymanapov, S. A., Muratbekov, M., Altynbek, S., Barlybayev, A. (2021). Fuzzy Expert System of Information Security Risk Assessment on the Example of Analysis Learning Management Systems. IEEE Access, 9, 156556–156565. https://doi.org/10.1109/access.2021.3129488
- Kozhukhivskyi, A. D., Kozhukhivska, O. A. (2022). Developing a fuzzy risk assessment model for erpsystems. Radio Electronics, Computer Science, Control, 1, 106–119. https://doi.org/10.15588/1607-3274-2022-1-12
- Krasnobayev, V., Kuznetsov, A., Yanko, A., Kuznetsova, T. (2020). The analysis of the methods of data diagnostic in a residue number system. Computer Modeling and Intelligent Systems. Zaporizhzhia, 2608, 594–609. https://doi.org/10.32782/cmis/2608-46
- Krasnobayev, V., Yanko, A., Kovalchuk, D. (2023). Control, Diagnostics and Error Correction in the Modular Number System. Computer Modeling and Intelligent Systems. Zaporizhzhia, 3392, 199–213. https://doi.org/10.32782/cmis/3392-17
- Yevseiev, S., Shmatko, O., Romashchenko, N. (2019). Algorithm of information security risk assessment based on fuzzy-multiple approach. Advanced Information Systems, 3 (2), 73–79. https://doi.org/10.20998/2522-9052.2019.2.13
- Kozlenko, O. (2024). Example of fuzzy ontology usage for risk assessment and attack impact. Theoretical and Applied Cybersecurity, 6 (1), 91–98. https://doi.org/10.20535/tacs.2664-29132024.1.312677
- Laktionov, A. (2021). Improving the methods for determining the index of quality of subsystem element interaction. Eastern-European Journal of Enterprise Technologies, 6 (3 (114)), 72–82. https://doi.org/10.15587/1729-4061.2021.244929
- Alali, M., Almogren, A., Hassan, M. M., Rassan, I. A. L., Bhuiyan, M. Z. A. (2018). Improving risk assessment model of cyber security using fuzzy logic inference system. Computers & Security, 74, 323–339. https://doi.org/10.1016/j.cose.2017.09.011
- Calvo, M., Beltrán, M. (2022). A Model For risk-Based adaptive security controls. Computers & Security, 115, 102612. https://doi.org/10.1016/j.cose.2022.102612
- Religia, A. A., Utama, D. N. (2023). A Fuzzy-based Simple Smart Decision Model for Assessing Information Security Risk in Public Sector Organization. 2023 10th International Conference on ICT for Smart Society (ICISS). Bandung: IEEE, 1–5. https://doi.org/10.1109/iciss59129.2023.10291864
- Ponochovniy, Y., Bulba, E., Yanko, A., Hozbenko, E. (2018). Influence of diagnostics errors on safety: Indicators and requirements. 2018 IEEE 9th International Conference on Dependable Systems, Services and Technologies (DESSERT). Kyiv: IEEE, 53–57. https://doi.org/10.1109/dessert.2018.8409098
- Taskin, A., Kumbasar, T. (2015). An Open Source Matlab/Simulink Toolbox for Interval Type-2 Fuzzy Logic Systems. 2015 IEEE Symposium Series on Computational Intelligence. Cape Town: IEEE, 1561–1568. https://doi.org/10.1109/ssci.2015.220
- Fuzzy Logic Toolbox: Design and simulate fuzzy logic systems. MathWorks. Available at: https://www.mathworks.com/help/fuzzy/index.html
- Golosovskiy, M. S., Bogomolov, A. V., Evtushenko, E. V. (2021). An Algorithm for Setting Sugeno-Type Fuzzy Inference Systems. Automatic Documentation and Mathematical Linguistics, 55 (3), 79–88. https://doi.org/10.3103/s000510552103002x
- Vulnerability Metrics (2024). National Institute of Standards and Technology. Available at: https://nvd.nist.gov/vuln-metrics/cvss
- Live Cyber Threat Map. Check Point Software Technologies. Available at: https://threatmap.checkpoint.com/
Downloads
Published
How to Cite
Issue
Section
License
Copyright (c) 2025 Yurii Zdorenko, Alina Yanko, Mykhailo Myziura, Nadiia Fesokha

This work is licensed under a Creative Commons Attribution 4.0 International License.
The consolidation and conditions for the transfer of copyright (identification of authorship) is carried out in the License Agreement. In particular, the authors reserve the right to the authorship of their manuscript and transfer the first publication of this work to the journal under the terms of the Creative Commons CC BY license. At the same time, they have the right to conclude on their own additional agreements concerning the non-exclusive distribution of the work in the form in which it was published by this journal, but provided that the link to the first publication of the article in this journal is preserved.







