Decision-making on Command Query Responsibility Segregation with Event Sourcing architectural variations
DOI:
https://doi.org/10.15587/2706-5448.2025.337168Keywords:
software architectures, software metrics, formal methods, support decision-making, CQRS, Event SourcingAbstract
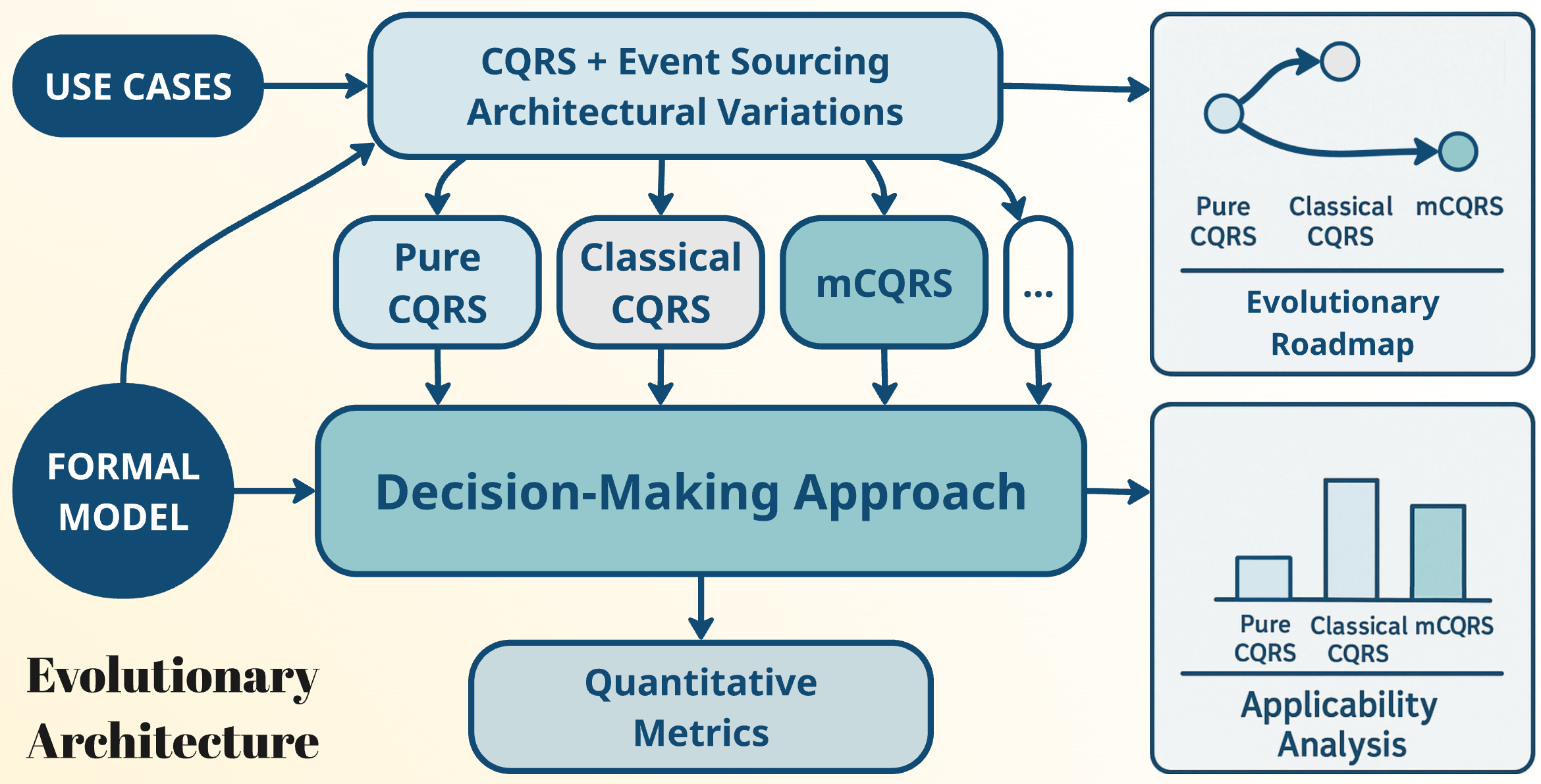
The object of the research is the process of selecting and evaluating architectural solutions, both at the design stage and during the migration of a software application’s architecture, within the context of evolutionary architecture. The paper is focused on variations of the Command Query Responsibility Segregation (CQRS) with Event Sourcing (ES) architecture, which, in fact, is a family of architectural variations that differ in complexity, performance, development time, and the required expertise from developers. These differences have a significant impact on the development cost and maintainability of the software application. Moreover, changes in business requirements or technical context often necessitate migration among architectural variations, which may drastically increase costs if not planned properly.
In the absence of objective evaluation criteria, decisions are often based on expert judgment, which may be unavailable or insufficient. This work proposes a decision-making support approach for CQRS with ES architectural variation selection and migration planning. The approach is based on classification of processes and breaking them down into smaller activities. This enables objective comparisons of architectural variations based on complexity and performance metrics.
The application of the approach is shown on two basic variations. Metrics were obtained, and a bitmap chart was built to visualize architectural applicability, depending on the project priorities. The applicability score of mCQRS ranges from 39% to 53%, while that of Classical CQRS – 47–61%.
The proposed approach is applicable in projects where architecture evolution is expected. It is especially useful in organizations operating at Capability Maturity Models Integration (CMMI) Level 4 (Quantitatively Managed Organization) which is focused on predictability of quantitative performance improvement objectives.
References
- Fowler, M., Rice, D., Foemmel, M., Hieatt, E., Mee, R., Stafford, R. (2002). Patterns of Enterprise Application Architecture. Boston: Addison-Wesley, 560. Available at: https://dl.ebooksworld.ir/motoman/Patterns%20of%20Enterprise%20Application%20Architecture.pdf
- Hohpe, G., Woolf, B. (2011). Enterprise Integration Patterns: Designing, Building, and Deploying Messaging Solutions. Boston: Addison-Wesley. Available at: https://ptgmedia.pearsoncmg.com/images/9780321200686/samplepages/0321200683.pdf
- Evans, E. (2003). Domain-Driven Design: Tackling Complexity in the Heart of Software. Boston: Addison-Wesley. Available at: https://fabiofumarola.github.io/nosql/readingMaterial/Evans03.pdf
- Zhong, Y., Li, W., Wang, J. (2019). Using Event Sourcing and CQRS to Build a High Performance Point Trading System. Proceedings of the 2019 5th International Conference on E-Business and Applications. Bangkok, New York, 16–19. https://doi.org/10.1145/3317614.3317632
- Betts, D., Dominguez, J., Melnik, G., Simonazzi, F., Subramanian, M. (2012). Exploring CQRS and Event Sourcing: A Journey into High Scalability, Availability, and Maintainability with Windows Azure. Microsoft patterns & practices. Available at: https://download.microsoft.com/download/e/a/8/ea8c6e1f-01d8-43ba-992b-35cfcaa4fae3/cqrs_journey_guide.pdf
- Fowler, M. (2011). CQRS. Available at: https://martinfowler.com/bliki/CQRS.html
- Young, G. (2010). CQRS Documents by Greg Young. Available at: https://cqrs.files.wordpress.com/2010/11/cqrs_documents.pdf
- Young, G. (2017). Event Centric: Finding Simplicity in Complex Systems. Boston: Addison-Wesley Professional, 560.
- Taylor, H., Yochem, A., Phillips, L., Martinez, F. (2009). Event-Driven Architecture: How SOA Enables the RealTime Enterprise. Boston: Addison-Wesley, 272.
- Vernon, V. (2013). Implementing Domain-Driven Design. Boston: Addison Wesley, 656.
- Ford, N., Parsons, R., Kua, P., Sadalage, P. (2022). Building evolutionary architectures. Sebastopol: O'Reilly Media, 262.
- Event Sourcing pattern. Microsoft. Available at: https://learn.microsoft.com/en-us/azure/architecture/patterns/event-sourcing
- Comartin, D. (2021). Snapshots in Event Sourcing for Rehydrating Aggregates. CodeOpinion. Available at: https://codeopinion.com/snapshots-in-event-sourcing-for-rehydrating-aggregates/
- Evsyukov, O. (2020). Bermudskyi Ahrehat. I spasenye utopaiushchykh. Domain-Driven Design Injection. Available at: https://youtu.be/Br4TL-486ZM?t=1500
- Young, G. (2017). Versioning in an Event Sourced System. Available at: https://leanpub.com/esversioning/read
- Kleanthous, S. (2021). Event immutability and dealing with change. Kurrent. Available at: https://www.eventstore.com/blog/event-immutability-and-dealing-with-change
- Zheng, Z., Xie, S., Dai, H., Chen, X., Wang, H. (2017). An Overview of Blockchain Technology: Architecture, Consensus, and Future Trends. 2017 IEEE International Congress on Big Data (BigData Congress). Honolulu, 557–564. https://doi.org/10.1109/bigdatacongress.2017.85
- Regulation (EU) 2016/679 of the European Parliament and of the Council of 27 April 2016 on the protection of natural persons with regard to the processing of personal data and on the free movement of such data, and repealing Directive 95/46/EC (General Data Protection Regulation) (Text with EEA relevance). Official Journal of the European Union, 119, 4.5.2016, 1–88. Available at: https://eur-lex.europa.eu/eli/reg/2016/679/oj/eng
- Vasconcellos, P. R. G., Bezerra, V. M., Bianchini, C. P. (2018). Applying Event Sourcing in a ERP System: A Case Study. 2018 XLIV Latin American Computer Conference (CLEI). São Paulo, 80–89. https://doi.org/10.1109/clei.2018.00019
- Korkmaz, N., Nilsson, M. (2014). Practitioners’ view on command query responsibility segregation. [Master's thesis; Lund University]. Available at: https://lup.lub.lu.se/luur/download?func=downloadFile&recordOId=4864802&fileOId=4864803
- Lytvynov, O., Hruzin, D., Frolov, M. (2024). On the migration of domain driven design to CQRS with event sourcing software architecture. Information Technology: Computer Science, Software Engineering and Cyber Security, 1, 50–60. https://doi.org/10.32782/it/2024-1-7
- Pandiya, D. K., Charankar, N. G. (2024). Optimizing Performance and Scalability in Micro Services with CQRS Design. International Journal of Engineering Research & Technology, 13 (4). Available at: https://www.ijert.org/optimizing-performance-and-scalability-in-micro-services-with-cqrs-design
- DBB Software's. Available at: https://dbbsoftware.com/
- ISO/IEC/IEEE 24748-1:2024(en) Systems and software engineering – Life cycle management – Part 1: Guidelines for life cycle management (2024). ISO. Available at: https://www.iso.org/obp/ui/en/#iso:std:iso-iec-ieee:24748:-1:ed-2:v1:en
- Sobhy, D., Bahsoon, R., Minku, L., Kazman, R. (2021). Evaluation of Software Architectures under Uncertainty. ACM Transactions on Software Engineering and Methodology, 30 (4), 1–50. https://doi.org/10.1145/3464305
- Bahsoon, R., Emmerich, W. (2003). Evaluating software architectures: development, stability, and evolution. ACS/IEEE International Conference on Computer Systems and Applications. Tunis, 47. https://doi.org/10.1109/aiccsa.2003.1227480
- Kazman, R., Bass, L., Abowd, G., Webb, M. (1994). SAAM: a method for analyzing the properties of software architectures. Proceedings of 16th International Conference on Software Engineering. Sorrento, 81–90. https://doi.org/10.1109/icse.1994.296768
- Kazman, R., Klein, M., Clements, P. (2000). ATAM: Method for Architecture Evaluation. Technical report CMU/SEI-2000-TR-004. Carnegie Mellon Software Engineering Institute. Pittsburgh. Available at: https://www.sei.cmu.edu/documents/629/2000_005_001_13706.pdf
- Kazman, R., Jai Asundi, Klein, M. (2001). Quantifying the costs and benefits of architectural decisions. Proceedings of the 23rd International Conference on Software Engineering. ICSE 2001. Toronto, 297–306. https://doi.org/10.1109/icse.2001.919103
- Faniyi, F., Bahsoon, R., Evans, A., Kazman, R. (2011). Evaluating Security Properties of Architectures in Unpredictable Environments: A Case for Cloud. 2011 Ninth Working IEEE/IFIP Conference on Software Architecture. Washington, 127–136. https://doi.org/10.1109/wicsa.2011.25
- Zarghami, M., Szidarovszky, F. (2011). Introduction to Multicriteria Decision Analysis. Multicriteria Analysis. Berlin, Heidelberg: Springer, 1–12. https://doi.org/10.1007/978-3-642-17937-2_1
- Brunelli, M. (2015). Introduction to the Analytic Hierarchy Process. SpringerBriefs in Operations Research. Cham: Springer International Publishing. https://doi.org/10.1007/978-3-319-12502-2
- Al-Naeem, T., Gorton, I., Babar, M. A., Rabhi, F., Benatallah, B. (2005). A quality-driven systematic approach for architecting distributed software applications. Proceedings of the 27th International Conference on Software Engineering – ICSE ’05. St. Louis, 244–253. https://doi.org/10.1145/1062455.1062508
- Kim, C.-K., Lee, D.-H., Ko, I.-Y., Baik, J. (2007). A Lightweight Value-based Software Architecture Evaluation. Eighth ACIS International Conference on Software Engineering, Artificial Intelligence, Networking, and Parallel/Distributed Computing (SNPD 2007). Washington, 646–649. https://doi.org/10.1109/snpd.2007.507
- Bourque, P., Fairley, R. E. (2014). Guide to the Software Engineering Body of Knowledge – SWEBOK V3.0. Piscataway: IEEE and IEEE Computer Society Press. Available at: https://www.researchgate.net/publication/342452008_Guide_to_the_Software_Engineering_Body_of_Knowledge_-_SWEBOK_V30
- Nivedhaa, N. (2024). Software architecture evolution: Patterns, trends, and best practices. International Journal of Computer Sciences and Engineering, 1, 1–14. Available at: https://www.researchgate.net/publication/384019495_SOFTWARE_ARCHITECTURE_EVOLUTION_PATTERNS_TRENDS_AND_BEST_PRACTICES
- Milić, M., Makajić-Nikolić, D. (2022). Development of a Quality-Based Model for Software Architecture Optimization: A Case Study of Monolith and Microservice Architectures. Symmetry, 14 (9), 1824. https://doi.org/10.3390/sym14091824
- ISO/IEC/IEEE 24765:2017 Systems and software engineering – Vocabulary (2017). ISO. Available at: https://www.iso.org/standard/71952.html
- Mohapatra, S. K., Prasad, S. (2015). Finding Representative Test Case for Test Case Reduction in Regression Testing. International Journal of Intelligent Systems and Applications, 7 (11), 60–65. https://doi.org/10.5815/ijisa.2015.11.08
- Mens, T. (2016). Research trends in structural software complexity. arXiv:1608.01533v1. https://doi.org/10.48550/arXiv.1608.01533
- Sarala, S., Abdul Jabbar, P. (2010). Information flow metrics and complexity measurement. 2010 3rd International Conference on Computer Science and Information Technology. Chengdu, 575–578. https://doi.org/10.1109/iccsit.2010.5563667
- Beyer, D., Häring, P. (2014). A formal evaluation of DepDegree based on weyuker’s properties. Proceedings of the 22nd International Conference on Program Comprehension. Hyderabad, 258–261. https://doi.org/10.1145/2597008.2597794
- McCabe, T. J. (1976). A Complexity Measure. IEEE Transactions on Software Engineering, SE-2 (4), 308–320. https://doi.org/10.1109/tse.1976.233837
- Halstead, M. H. (1977). Elements of Software Science. New York: Elsevier Science Inc., 128.
- Stepien, B. (2003). Software development cost estimation methods and research trends. Computer Science, 5 (1), 67–86. Available at: https://www.researchgate.net/publication/50365764_Software_Development_Cost_Estimation_Methods
- Wang, Y., Shao, J. (2003). Measurement of the cognitive functional complexity of software. Proceedings of the 2nd IEEE International Conference on Cognitive Informatics (ICCI '03). Washington, 67–74. https://doi.org/10.1109/COGINF.2003.1225955
- Zlaugotne, B., Zihare, L., Balode, L., Kalnbalkite, A., Khabdullin, A., Blumberga, D. (2020). Multi-Criteria Decision Analysis Methods Comparison. Environmental and Climate Technologies, 24 (1), 454–471. https://doi.org/10.2478/rtuect-2020-0028
- Jahanshahi, H., Alijani, Z., Mihalache, S. F. (2023). Towards Sustainable Transportation: A Review of Fuzzy Decision Systems and Supply Chain Serviceability. Mathematics, 11 (8), 1934. https://doi.org/10.3390/math11081934
- Vafaei, N., Ribeiro, R. A., Camarinha-Matos, L. M. (2016). Normalization Techniques for Multi-Criteria Decision Making: Analytical Hierarchy Process Case Study. Technological Innovation for Cyber-Physical Systems. Costa de Caparica, 261–269. https://doi.org/10.1007/978-3-319-31165-4_26
- Young, G. (2023). GitHub: EventStore repository. Available at: https://github.com/gregoryyoung/EventStore
- Driscoll, M. (2017). The Publish-Subscribe Pattern. WxPython Recipes. Berkeley: Apress, 43–50. https://doi.org/10.1007/978-1-4842-3237-8_4
- CQRS. Practical and focused guide for survival in post-CQRS world: Projections. Available at: http://cqrs.wikidot.com/doc:projection
- Hierons, R. M., Türker, U. C. (2017). Parallel Algorithms for Generating Distinguishing Sequences for Observable Non-deterministic FSMs. ACM Transactions on Software Engineering and Methodology, 26 (1), 1–34. https://doi.org/10.1145/3051121
- Wang, J., Tepfenhart, W. (2019). Petri Nets. Formal Methods in Computer Science. Chapman and Hall, CRC, 201–243. https://doi.org/10.1201/9780429184185-8
- Bollig, B., Katoen, J.-P., Kern, C., Leucker, M. (2010). Learning Communicating Automata from MSCs. IEEE Transactions on Software Engineering, 36 (3), 390–408. https://doi.org/10.1109/tse.2009.89
- Brand, D., Zafiropulo, P. (1983). On Communicating Finite-State Machines. Journal of the ACM, 30 (2), 323–342. https://doi.org/10.1145/322374.322380
- Harel, D. (1987). Statecharts: a visual formalism for complex systems. Science of Computer Programming, 8 (3), 231–274. https://doi.org/10.1016/0167-6423(87)90035-9
- Booch, G., Rumbaugh, J., Jacobson, I. (1999). The Unified Modeling Language User Guide. Addison Wesley Longman Publishing Co., Inc., 512. Available at: https://patologia.com.mx/informatica/uug.pdf
- Alur, R., Etessami, K., Yannakakis, M. (2001). Analysis of Recursive State Machines. Computer Aided Verification. Berlin, Heidelberg: Springer-Verlag, 207–220. https://doi.org/10.1007/3-540-44585-4_18
- Alur, R., Benedikt, M., Etessami, K., Godefroid, P., Reps, T., Yannakakis, M. (2005). Analysis of recursive state machines. ACM Transactions on Programming Languages and Systems, 27 (4), 786–818. https://doi.org/10.1145/1075382.1075387
- Chatterjee, K., Kragl, B., Mishra, S., Pavlogiannis, A. (2017). Faster algorithms for weighted recursive state machines. Proceedings of the 26th European Symposium on Programming, ESOP 2017 held as Part of the European Joint Conferences on Theory and Practice of Software. Uppsala: Springer, 287–313. https://doi.org/10.48550/arXiv.1701.04914
- Dubslaff, C., Wienhöft, P., Fehnker, A. (2024). Lazy model checking for recursive state machines. Software and Systems Modeling, 23 (2), 369–401. https://doi.org/10.1007/s10270-024-01159-z
- Simon, E., Stoffel, K. (2009). State machines and petri nets as a formal representation for systems life cycle management. Proceedings of the International Conference Information Systems. Barcelona, 275–282. Available at: https://www.researchgate.net/publication/228721890_State_machines_and_petri_nets_as_a_formal_representation_for_systems_life_cycle_management
- Van Der Aalst, W. M. P. (1998). The Application of Petri Nets to Workflow Management. Journal of Circuits, Systems and Computers, 8 (1), 21–66. https://doi.org/10.1142/s0218126698000043
- Jensen, K. (1996). Coloured Petri Nets. Monographs in Theoretical Computer Science. An EATCS Series. Berlin, Heidelberg: Springer. https://doi.org/10.1007/978-3-662-03241-1
- Ullman, J. D. (1998). Elements of ML Programming. New Jersey: Prentice-Hall. Available at: https://www.scribd.com/doc/221508984/Elements-of-Ml-Programming
- Fehling, R. (1993). A concept of hierarchical Petri nets with building blocks. Advances in Petri Nets 1993, 148–168. https://doi.org/10.1007/3-540-56689-9_43
- Farwer, B., Misra, K. (2002). Modelling with hierarchical object Petri nets. Fundamenta Informaticae, 55 (2), 129–147. Available at: https://www.researchgate.net/publication/220445187_Modelling_with_Hierarchical_Object_Petri_Nets
- Chistikov, D., Czerwinski, W., Hofman, P., Mazowiecki, F., Sinclair-Banks, H. (2023). Acyclic Petri and Workflow Nets with Resets. Proceedings of the 43rd IARCS Annual Conference on Foundations of Software Technology and Theoretical Computer Science. Dagstuhl Castle, Leibniz Center for Informatics, 284, 1–18. https://doi.org/10.4230/LIPIcs.FSTTCS.2023.16
- Lomazova, I. A., Mitsyuk, A. A., Rivkin, A. (2021). Soundness in Object-centric Workflow Petri Nets. arXiv:2112.14994v1. https://doi.org/10.48550/arXiv.2112.14994
- Blondin, M., Mazowiecki, F., Offtermatt, P. (2022). The complexity of soundness in workflow nets. Proceedings of the 37th Annual ACM/IEEE Symposium on Logic in Computer Science. New York, 1–13. https://doi.org/10.1145/3531130.3533341
- Meyer, T. (2023). A Symmetric Petri Net Model of Generic Publish-Subscribe Systems for Verification and Business Process Conformance Checking. Proceedings of the International Workshop on Petri Nets and Software Engineering (PNSE '23). Lisbon: CEUR, Aachen, 88–109. Available at: https://ceur-ws.org/Vol-3430/paper6.pdf
- Ding, J., Zhang, D. (2015). Modeling and Analyzing Publish Subscribe Architcture using Petri Nets. Proceedings of the 27th International Conference on Software Engineering and Knowledge Engineering, 2015. Pittsburgh: KSI Research Inc., 589–594. https://doi.org/10.18293/seke2015-232
- Genrich, H. J. (1991). Predicate / Transition Nets. High-Level Petri Nets. Berlin, Heidelberg: Springer-Verlag, 3–43. https://doi.org/10.1007/978-3-642-84524-6_1
- Lytvynov, O. A., Hruzin, D. L. (2024). Critical causal events in systems based on cqrs with event sourcing architecture. Radio Electronics, Computer Science, Control, 3, 119–143. https://doi.org/10.15588/1607-3274-2024-3-11
- Minsky, M. (1974). A Framework for Representing Knowledge. MIT Research Lab Technical Report. Cambridge: Massachusetts Institute of Technology. Available at: https://courses.media.mit.edu/2004spring/mas966/Minsky%201974%20Framework%20for%20knowledge.pdf
- Harel, D., Peleg, D. (1985). Process logic with regular formulas. Theoretical Computer Science, 38, 307–322. https://doi.org/10.1016/0304-3975(85)90225-7
- Levenshtein, V. (1965). Binary Codes Capable of Correcting Deletions, Insertions, and Reversals. Doklady Akademii nauk SSSR, 10, 707–710. Available at: https://nymity.ch/sybilhunting/pdf/Levenshtein1966a.pdf
- Cockburn, A. (2000). Writing Effective Use Cases. Boston: Addison-Wesley Professional, 304. Available at: https://kurzy.kpi.fei.tuke.sk/zsi/resources/CockburnBookDraft.pdf
- Hruzin, D. (2025). GitHub: CQRS-variations-test repository. Available at: https://github.com/dmitryhruzin/CQRS-variations-test
- Braz, M., Vergilio, S. (2006). Software Effort Estimation Based on Use Cases. 30th Annual International Computer Software and Applications Conference (COMPSAC’06). Chicago, 221–228. https://doi.org/10.1109/compsac.2006.77
- Zadeh, L. A. (1965). Fuzzy sets. Information and Control, 8 (3), 338–353. https://doi.org/10.1016/s0019-9958(65)90241-x
Downloads
Published
How to Cite
Issue
Section
License
Copyright (c) 2025 Oleksandr Lytvynov, Dmytro Hruzin

This work is licensed under a Creative Commons Attribution 4.0 International License.
The consolidation and conditions for the transfer of copyright (identification of authorship) is carried out in the License Agreement. In particular, the authors reserve the right to the authorship of their manuscript and transfer the first publication of this work to the journal under the terms of the Creative Commons CC BY license. At the same time, they have the right to conclude on their own additional agreements concerning the non-exclusive distribution of the work in the form in which it was published by this journal, but provided that the link to the first publication of the article in this journal is preserved.







