Implementation of class interaction under aggregation conditions
DOI:
https://doi.org/10.15587/1729-4061.2024.301011Keywords:
aggregation relationship, class-client, class-resource, mathematical model, queue of class objects, class conversion, softwareAbstract
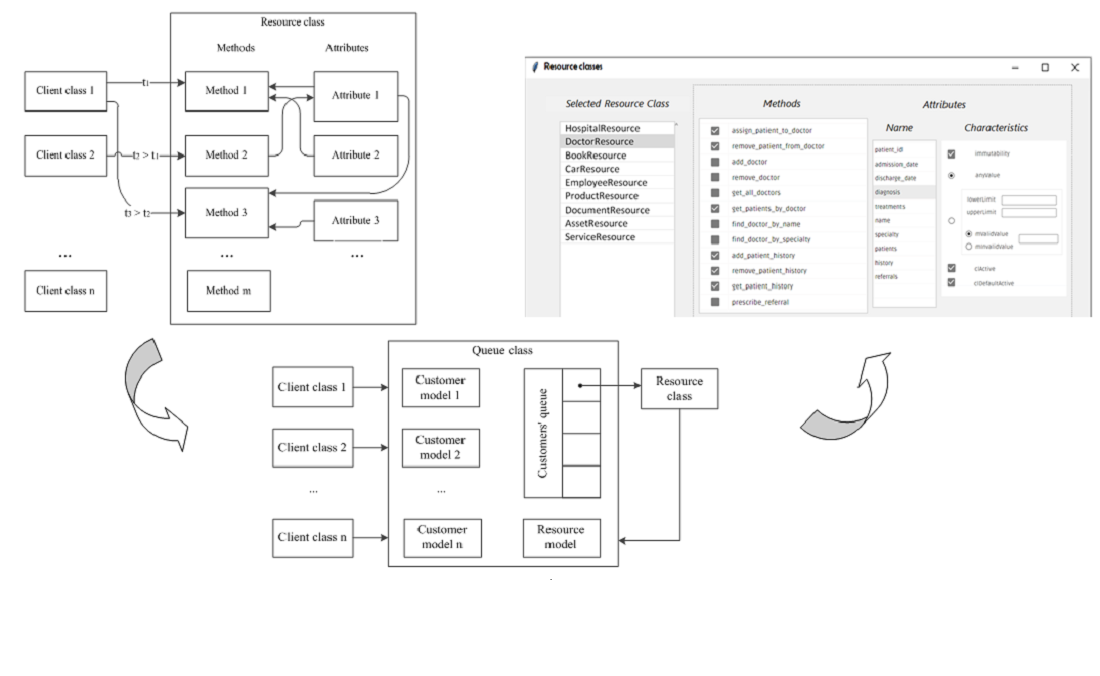
The object of research is the implementation of relations between software classes. It is shown that when implementing the aggregation relationship between classes, errors may occur if more than one client class is found. Class interaction errors can be caused by management of resource class attributes by one of the client classes in a way that is unacceptable to another client class due to invalid attribute values, state changes, method blocking, etc. To solve the problem, a special organization of the queue for client classes is proposed. A feature of the queue is the use of models of client classes and resource class. The model of a resource class provides an idea about its resources (attributes and methods) and how they are used. The client class model shows how much of these resources will be used by the client and how this will be done. This organization of the queue makes it possible to provide resources to the next client class only after checking its compatibility with active client classes. In general, client classes have different types, and this complicates the organization of the queue. Therefore, it is proposed to make them derived from the base class, which defines the interface for the queue. Similarly, the problem of the interaction of the class-resource with the queue is solved. The proposed base class for the resource class also provides the necessary queue interface.
Software was developed that automates the process of converting classes: analysis of a resource class, determination of resource needs from client classes, construction of base classes. After the conversion is completed, the queue functions are supported. The study results verification showed a reduction in the time for converting classes by about three times, and the waiting time for access to resources during the work of the queue – at least two times
References
- Bontchev, B., Milanova, E. (2020). On the Usability of Object-Oriented Design Patterns for a Better Software Quality. Cybernetics and Information Technologies, 20 (4), 36–54. https://doi.org/10.2478/cait-2020-0046
- Kungurtsev, O., Novikova, N., Reshetnyak, M., Cherepinina, Y., Gromaszek, K., Jarykbassov, D. (2019). Method for defining conceptual classes in the description of use cases. Photonics Applications in Astronomy, Communications, Industry, and High-Energy Physics Experiments 2019. https://doi.org/10.1117/12.2537070
- Kungurtsev, O. B., Novikova, N. O. (2020). Identification of class models imperfection. Herald of Advanced Information Technology, 3 (2), 13–22. https://doi.org/10.15276/hait.02.2020.1
- Rashidi, H., Parand, F. A. (2019). On Attributes of Objects in Object-Oriented Software Analysis. International Journal of Industrial Engineering & Production Research, 30 (3), 341–352. https://doi.org/10.22068/ijiepr.30.3.341
- Ürler, Ü., Berk, E. (2016). Queueing Theory. Decision Sciences, 287–348. https://doi.org/10.1201/9781315183176-7
- Komleva, N., Liubchenko, V., Zinovatna, S. (2020). Improvement of teaching quality in the view of a resource-based approach. CEUR Workshop Proceedings, 2740, 262–277. Available at: http://ceur-ws.org/Vol-2740/20200262.pdf
- Pang, X., Wang, Z., He, Z., Sun, P., Luo, M., Ren, J., Ren, K. (2023). Towards Class-Balanced Privacy Preserving Heterogeneous Model Aggregation. IEEE Transactions on Dependable and Secure Computing, 20 (3), 2421–2432. https://doi.org/10.1109/tdsc.2022.3183170
- Otu, G. A., Usman, S. A., Ugbe, R. U., Iheagwara, S. E., Okafor, A. C., Okonkwo, F. I. et al. (2023). Comparative analysis of aggregation and inheritance strategies in incremental program development. Fudma Journal Of Sciences, 7 (2), 57–64. https://doi.org/10.33003/fjs-2023-0702-1710
- Zhang, S. G. (2021). An In-Depth Understanding of Aggregation in Domain-Driven Design. Available at: https://www.alibabacloud.com/blog/an-in-depth-understanding-of-aggregation-in-domain-driven-design_598034
- Afolalu, S. A., Babaremu, K. O., Ongbali, S. O., Abioye, A. A., Abdulkareem, A., Adejuyigbe, S. B. (2019). Overview Impact Of Application Of Queuing Theory Model On Productivity Performance In A Banking Sector. Journal of Physics: Conference Series, 1378 (3), 032033. https://doi.org/10.1088/1742-6596/1378/3/032033
- Lakshmi, C., Appa Iyer, S. (2013). Application of queueing theory in health care: A literature review. Operations Research for Health Care, 2 (1-2), 25–39. https://doi.org/10.1016/j.orhc.2013.03.002
- Wang, N., Roongnat, C., Rosenberger, J. M., Menon, P. K., Subbarao, K., Sengupta, P., Tandale, M. D. (2018). Study of time-dependent queuing models of the national airspace system. Computers & Industrial Engineering, 117, 108–120. https://doi.org/10.1016/j.cie.2018.01.014
- Adeniran, Dr. A., Sani Burodo, M., Suleiman, Dr. S. (2022). Application of Queuing Theory and Management of Waiting Time Using Multiple Server Model: Empirical Evidence From Ahmadu Bello University Teaching Hospital, Zaria, Kaduna State, Nigeria. International Journal of Scientific and Management Research, 05 (04), 159–174. https://doi.org/10.37502/ijsmr.2022.5412
- Nor, A. H. A., Binti, N. S. H. (2018). Application of Queuing Theory Model and Simulation to Patient Flow at the Outpatient Department. Proceedings of the International Conference on Industrial Engineering and Operations Management Bandung, 3016–3028. Available at: https://ieomsociety.org/ieom2018/papers/694.pdf
- Kumar, R. (2020). Queueing system. Chap. 4. Modeling and Simulation Concepts. Available at: https://www.researchgate.net/publication/346721926_Book_Chapter_-_queueing_system
- De Clercq, S., Walraevens, J. (2020). Delay analysis of a two-class priority queue with external arrivals and correlated arrivals from another node. Annals of Operations Research, 293 (1), 57–72. https://doi.org/10.1007/s10479-020-03548-1
- Walulya, I., Chatterjee, B., Datta, A. K., Niyolia, R., Tsigas, P. (2018). Concurrent Lock-Free Unbounded Priority Queue with Mutable Priorities. Stabilization, Safety, and Security of Distributed Systems, 365–380. https://doi.org/10.1007/978-3-030-03232-6_24
- Hou, J., Zhao, X. (2019). Using a priority queuing approach to improve emergency department performance. Journal of Management Analytics, 7 (1), 28–43. https://doi.org/10.1080/23270012.2019.1691945
- Ferrari, P., Sisinni, E., Saifullah, A., Machado, R. C. S., De Sa, A. O., Felser, M. (2020). Work-in-Progress: Compromising Security of Real-time Ethernet Devices by means of Selective Queue Saturation Attack. 2020 16th IEEE International Conference on Factory Communication Systems (WFCS). https://doi.org/10.1109/wfcs47810.2020.9114505
- Hernandez-Gonzalez, S., Hernandez Ripalda, M. (2018). Systems With Limited Capacity. IGI Global, 172–211. https://doi.org/10.4018/978-1-5225-5264-2.ch006
- Larrain, H., Muñoz, J. C. (2020). The danger zone of express services: When increasing frequencies can deteriorate the level of service. Transportation Research Part C: Emerging Technologies, 113, 213–227. https://doi.org/10.1016/j.trc.2019.05.013
- Chakravarthy, S. R., Shruti, Kulshrestha, R. (2020). A queueing model with server breakdowns, repairs, vacations, and backup server. Operations Research Perspectives, 7, 100131. https://doi.org/10.1016/j.orp.2019.100131
- Ahmadi-Javid, A., Hoseinpour, P. (2019). Service system design for managing interruption risks: A backup-service risk-mitigation strategy. European Journal of Operational Research, 274 (2), 417–431. https://doi.org/10.1016/j.ejor.2018.03.028
- He, F., Oki, E. (2021). Unavailability-Aware Shared Virtual Backup Allocation for Middleboxes: A Queueing Approach. IEEE Transactions on Network and Service Management, 18 (2), 2388–2404. https://doi.org/10.1109/tnsm.2020.3026218
- Sunar, N., Tu, Y., Ziya, S. (2021). Pooled vs. Dedicated Queues when Customers Are Delay-Sensitive. Management Science, 67 (6), 3785–3802. https://doi.org/10.1287/mnsc.2020.3663
- He, B., Li, T. Z. (2021). An Offloading Scheduling Strategy with Minimized Power Overhead for Internet of Vehicles Based on Mobile Edge Computing. Journal of Information Processing Systems, 17 (3), 489–504. https://doi.org/10.3745/JIPS.01.0077
Downloads
Published
How to Cite
Issue
Section
License
Copyright (c) 2024 Oleksii Kungurtsev, Nataliia Komleva

This work is licensed under a Creative Commons Attribution 4.0 International License.
The consolidation and conditions for the transfer of copyright (identification of authorship) is carried out in the License Agreement. In particular, the authors reserve the right to the authorship of their manuscript and transfer the first publication of this work to the journal under the terms of the Creative Commons CC BY license. At the same time, they have the right to conclude on their own additional agreements concerning the non-exclusive distribution of the work in the form in which it was published by this journal, but provided that the link to the first publication of the article in this journal is preserved.
A license agreement is a document in which the author warrants that he/she owns all copyright for the work (manuscript, article, etc.).
The authors, signing the License Agreement with TECHNOLOGY CENTER PC, have all rights to the further use of their work, provided that they link to our edition in which the work was published.
According to the terms of the License Agreement, the Publisher TECHNOLOGY CENTER PC does not take away your copyrights and receives permission from the authors to use and dissemination of the publication through the world's scientific resources (own electronic resources, scientometric databases, repositories, libraries, etc.).
In the absence of a signed License Agreement or in the absence of this agreement of identifiers allowing to identify the identity of the author, the editors have no right to work with the manuscript.
It is important to remember that there is another type of agreement between authors and publishers – when copyright is transferred from the authors to the publisher. In this case, the authors lose ownership of their work and may not use it in any way.








