Point coordination mechanism based mobile ad hoc network investigation against jammers
DOI:
https://doi.org/10.15587/1729-4061.2022.265779Keywords:
MANET, Riverbed, point coordination, routing protocols, jamming attacks, delay, throughputAbstract
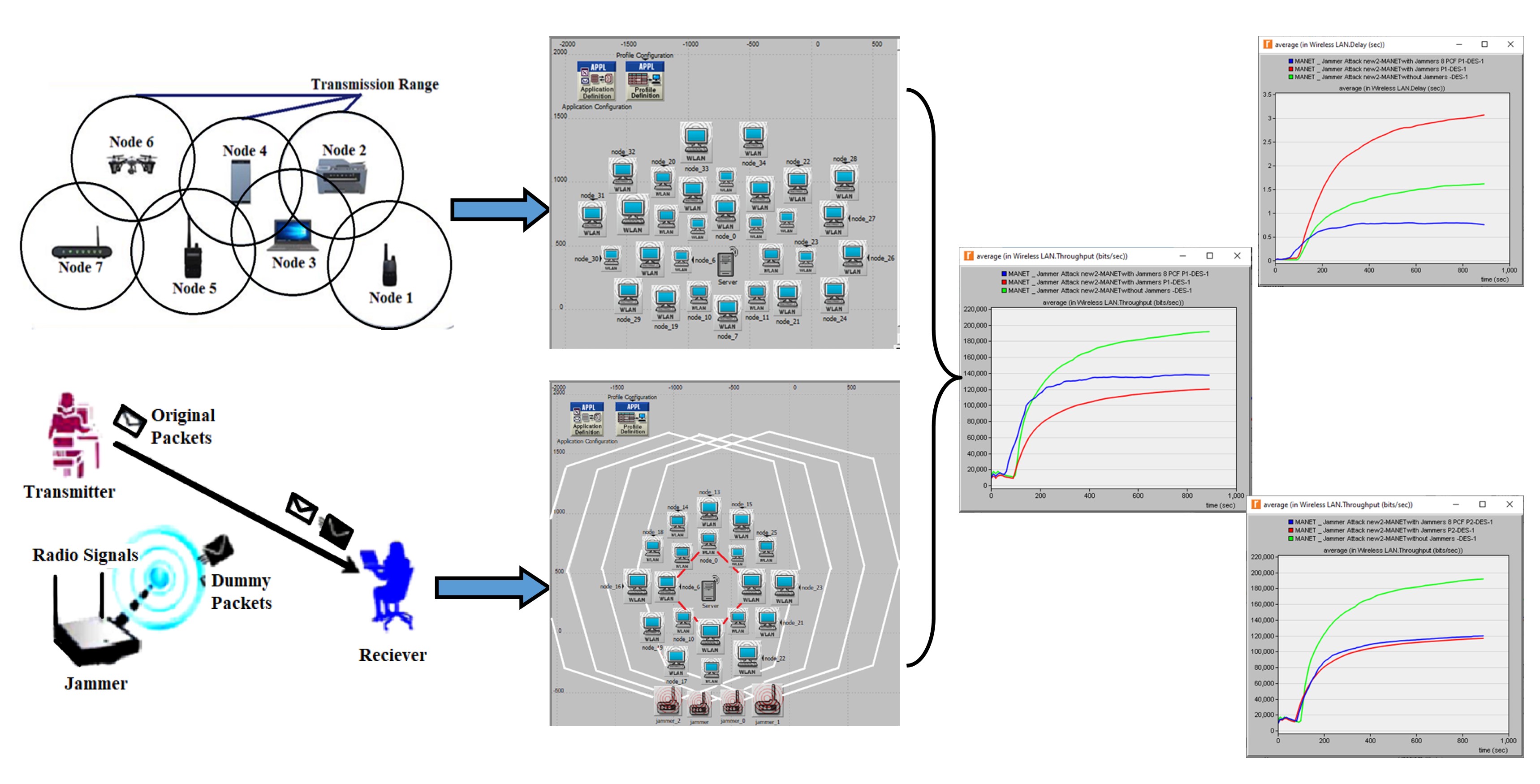
In this paper, a jamming attack (a kind of Denial-of-Service attack) was investigated, which interfered with the normal operation of a Mobile Ad Hoc network, which is more vulnerable to various attacks because of its self-configuration, dynamic characteristics, therefore, jammers would affect the network QoS parameters by reducing the throughput and increasing the delay. This problem is solved in this study by enabling the Point Coordination Function, which is a media access mechanism specified by the IEEE standard in some selected MANET nodes (guard nodes) to improve the deficiency of MANET’s performance. The Riverbed modeler was utilized as a simulation tool. In this study, six jammers with two different transmission power values had been applied. In a number of different simulation scenarios with and without jammers, the estimated results showed that the jammers affected the network performance by increasing the delay to 3.0658 sec and decreasing the throughput to 120200.59 bits/sec. After enabling the PCF mechanism in a number of selected nodes, the results allowed the user to solve the problem by improving the network deficiency so that the throughput had been increased to 137478.32 bits/sec and the delay had been decreased to 0.7556 sec. It can be concluded that PCF is a good improvement for different levels of jammer transmission power such as 0.01 W and 0.001 W, and PCF also improved the network’s delay and throughput when the number of PCF enabled nodes had been increased to 10 nodes and 12 nodes, respectively. The improvement is also increased. This study can be used in practice for any ad hoc network when attacked by jammers
References
- Alani, S., Zakaria, Z., Lago, H. (2019). A new energy consumption technique for mobile ad hoc networks. International Journal of Electrical and Computer Engineering (IJECE), 9 (5), 4147. doi: https://doi.org/10.11591/ijece.v9i5.pp4147-4153
- Meddeb, R., Triki, B., Jemili, F., Korbaa, O. (2017). A survey of attacks in mobile ad hoc networks. 2017 International Conference on Engineering & MIS (ICEMIS). doi: https://doi.org/10.1109/icemis.2017.8273007
- Vidhya Lakshmi, G., Vaishnavi, P. (2022). An Efficient Security Framework for Trusted and Secure Routing in MANET: A Comprehensive Solution. Wireless Personal Communications, 124 (1), 333–348. doi: https://doi.org/10.1007/s11277-021-09359-2
- Singh, J., Gupta, S. (2017). Impact of Jamming Attack in Performance of Mobile Ad hoc Networks. International Journal of Computer Science Trends and Technology (IJCST), 5 (3), 184–190. Available at: http://www.ijcstjournal.org/volume-5/issue-3/IJCST-V5I3P33.pdf
- Zhang, R., Sun, J., Zhang, Y., Huang, X. (2015). Jamming-Resilient Secure Neighbor Discovery in Mobile Ad Hoc Networks. IEEE Transactions on Wireless Communications, 14 (10), 5588–5601. doi: https://doi.org/10.1109/twc.2015.2439688
- Houssaini, M.-A. E., Aaroud, A., Hore, A. E., Ben-Othman, J. (2016). Detection of Jamming Attacks in Mobile Ad Hoc Networks Using Statistical Process Control. Procedia Computer Science, 83, 26–33. doi: https://doi.org/10.1016/j.procs.2016.04.095
- Albanese, M., De Benedictis, A., Jajodia, S., Torrieri, D. (2014). A probabilistic framework for jammer identification in MANETs. Ad Hoc Networks, 14, 84–94. doi: https://doi.org/10.1016/j.adhoc.2013.11.007
- Kim, J., Biswas, P. K., Bohacek, S., Mackey, S. J., Samoohi, S., Patel, M. P. (2021). Advanced protocols for the mitigation of friendly jamming in mobile ad-hoc networks. Journal of Network and Computer Applications, 181, 103037. doi: https://doi.org/10.1016/j.jnca.2021.103037
- Akila, R., Jenefer, M. P. (2016). Efficient Policy based Detection of Jamming Attacks in MANETS. International Journal of Advanced Research in Computer and Communication Engineering, 5 (3), 316–324. Available at: https://www.ijarcce.com/upload/2016/march-16/IJARCCE%2078.pdf
- Maheswari, R., Rajeswari, S. (2015). A Review on Types of Jamming Attack In Mobile Ad-Hoc Network. Proceedings of the UGC Sponsored National Conference on Advanced Networking and Applications, 84–86. Available at: https://www.ijana.in/Special%20Issue/file18.pdf
- Thapak, S., Chouksey, P. (2019). Protection From Jamming Attack And Service, Quality Improvement Of Network In Future MANET Communication Network. International Journal of Scientific & Technology Research, 8 (11), 3706–3714. Available at: http://www.ijstr.org/final-print/nov2019/Protection-From-Jamming-Attack-And-Service-quality-Improvement-Of-Network-In-Future-Manet-Communication-Network.pdf
- Jayanand, A. (2020). A cooperative combined defense technique for jamming attack in MANET. International Journal of Operational Research, 37 (4), 549. doi: https://doi.org/10.1504/ijor.2020.105767
- Aditi, Singh, J. K. (2017). Detection and isolation mechanism of jamming attack for aodv in manet. International Journal of Technical Research & Science, 2 (II), 76–83. Available at: https://www.ijtrs.com/uploaded_paper/DETECTION%20AND%20ISOLATION%20MECHANISM%20OF%20JAMMING%20ATTACK%20FOR%20AODV%20IN%20MANET%201.pdf
- Vijayalakshmi, K., Hema Rajini, N. (2021). Detection Of Jamming Attack In Manet Using Enhanced Artificial Bee Colony Algorithm. International Journal of Electrical Engineering and Technology (IJEET), 12 (4), 25–32. Available at: https://iaeme.com/MasterAdmin/Journal_uploads/IJEET/VOLUME_12_ISSUE_4/IJEET_12_04_004.pdf
- Sirmollo, C. Z., Bitew, M. A. (2021). Mobility-Aware Routing Algorithm for Mobile Ad Hoc Networks. Wireless Communications and Mobile Computing, 2021, 1–12. doi: https://doi.org/10.1155/2021/6672297
- Zaki, S. M., Ngadi, M. A., Kamat, M., Razak, S. A. (2020). A Review of Location Prediction Techniques in Mobile Ad Hoc Networks. Al-Qadisiyah Journal Of Pure Science, 25 (2), 17–28. doi: https://doi.org/10.29350/qjps.2020.25.2.974
- Haglan, H. M., Mostafa, S. A., Safar, N. Z. M., Mustapha, A., Saringatb, Mohd. Z., Alhakami, H., Alhakami, W. (2021). Analyzing the impact of the number of nodes on the performance of the routing protocols in manet environment. Bulletin of Electrical Engineering and Informatics, 10 (1), 434–440. doi: https://doi.org/10.11591/eei.v10i1.2516
- Joy, A., Singh, K. (2017). Detection Mechanism for Jamming Attack in MANET. Int. J. Sci. Res. Dev., 4 (11), 604–607.
- Fernendes, D., Rakesh Kumar, B. (2017). Survey on jamming attack in manet. International Journal of Latest Trends in Engineering and Technology, 410–414. Available at: https://www.ijltet.org/journal/151065846992.pdf
- Hamdi, M. M., Audah, L., Abood, M. S., Rashid, S. A., Mustafa, A. S., Mahdi, H., Al-Hiti, A. S. (2021). A review on various security attacks in vehicular ad hoc networks. Bulletin of Electrical Engineering and Informatics, 10 (5), 2627–2635. doi: https://doi.org/10.11591/eei.v10i5.3127
- Mahajan, A. S., Mahajan, S., Marwaha, M. (2017). Review of aodv & dsr protocols under jamming attack and recovery with pcf technique. Int. J. Softw. Hardw. Res. Eng., 5 (10), 14–17.
- Xiao, X. (2008). Technical, Commercial and Regulatory Challenges of QoS. An Internet Service Model Perspective. Elsevier. doi: https://doi.org/10.1016/B978-0-12-373693-2.X0001-8
- Kaler, V., Bairwa, A. K. et. al. (2017). Performance analysis of traffic oriented pcf in wireless local area network. International Conference On Communication & Computational Technologies, 312–318. Available at: https://ijcrt.org/papers/IJCRTICCC048.pdf
- Jie, L., Wang, L. (2019). Simulation tools for MANETs: a systematic survey. International Journal of Advanced Trends in Computer Science and Engineering, 2 (11), 1045–1053. Available at: https://www.researchgate.net/publication/337949935_Simulation_tools_for_MANETs_a_systematic_survey
- Nourildean, S. W., Mohammed, Y. A., Salih, A. M. (2022). Mobile Ad Hoc Network Improvement against Jammers for Video Applications Using Riverbed Modeler (v17.5). Webology, 19 (1), 1446–1459. doi: https://doi.org/10.14704/web/v19i1/web19096
- Rao, Y. C., Kishore, P., Prasad, S. R. (2019). Riverbed Modeler Simulation-Based Performance Analysis of Routing Protocols in Mobile Ad Hoc Networks. International Journal of Recent Technology and Engineering (IJRTE), 7 (6S), 350–354. Available at: https://www.ijrte.org/wp-content/uploads/papers/v7i6s/F02690376S19.pdf
Downloads
Published
How to Cite
Issue
Section
License
Copyright (c) 2022 Shayma Nourildean, Sabbar Jasim, May Abdulhadi, Mustafa Jaber

This work is licensed under a Creative Commons Attribution 4.0 International License.
The consolidation and conditions for the transfer of copyright (identification of authorship) is carried out in the License Agreement. In particular, the authors reserve the right to the authorship of their manuscript and transfer the first publication of this work to the journal under the terms of the Creative Commons CC BY license. At the same time, they have the right to conclude on their own additional agreements concerning the non-exclusive distribution of the work in the form in which it was published by this journal, but provided that the link to the first publication of the article in this journal is preserved.
A license agreement is a document in which the author warrants that he/she owns all copyright for the work (manuscript, article, etc.).
The authors, signing the License Agreement with TECHNOLOGY CENTER PC, have all rights to the further use of their work, provided that they link to our edition in which the work was published.
According to the terms of the License Agreement, the Publisher TECHNOLOGY CENTER PC does not take away your copyrights and receives permission from the authors to use and dissemination of the publication through the world's scientific resources (own electronic resources, scientometric databases, repositories, libraries, etc.).
In the absence of a signed License Agreement or in the absence of this agreement of identifiers allowing to identify the identity of the author, the editors have no right to work with the manuscript.
It is important to remember that there is another type of agreement between authors and publishers – when copyright is transferred from the authors to the publisher. In this case, the authors lose ownership of their work and may not use it in any way.








