A model of decoy system based on dynamic attributes for cybercrime investigation
DOI:
https://doi.org/10.15587/1729-4061.2023.273363Keywords:
decoys, cybercrime, security, analysis, deception, blockchain, Honeypot, Deception, network, cybersecurityAbstract
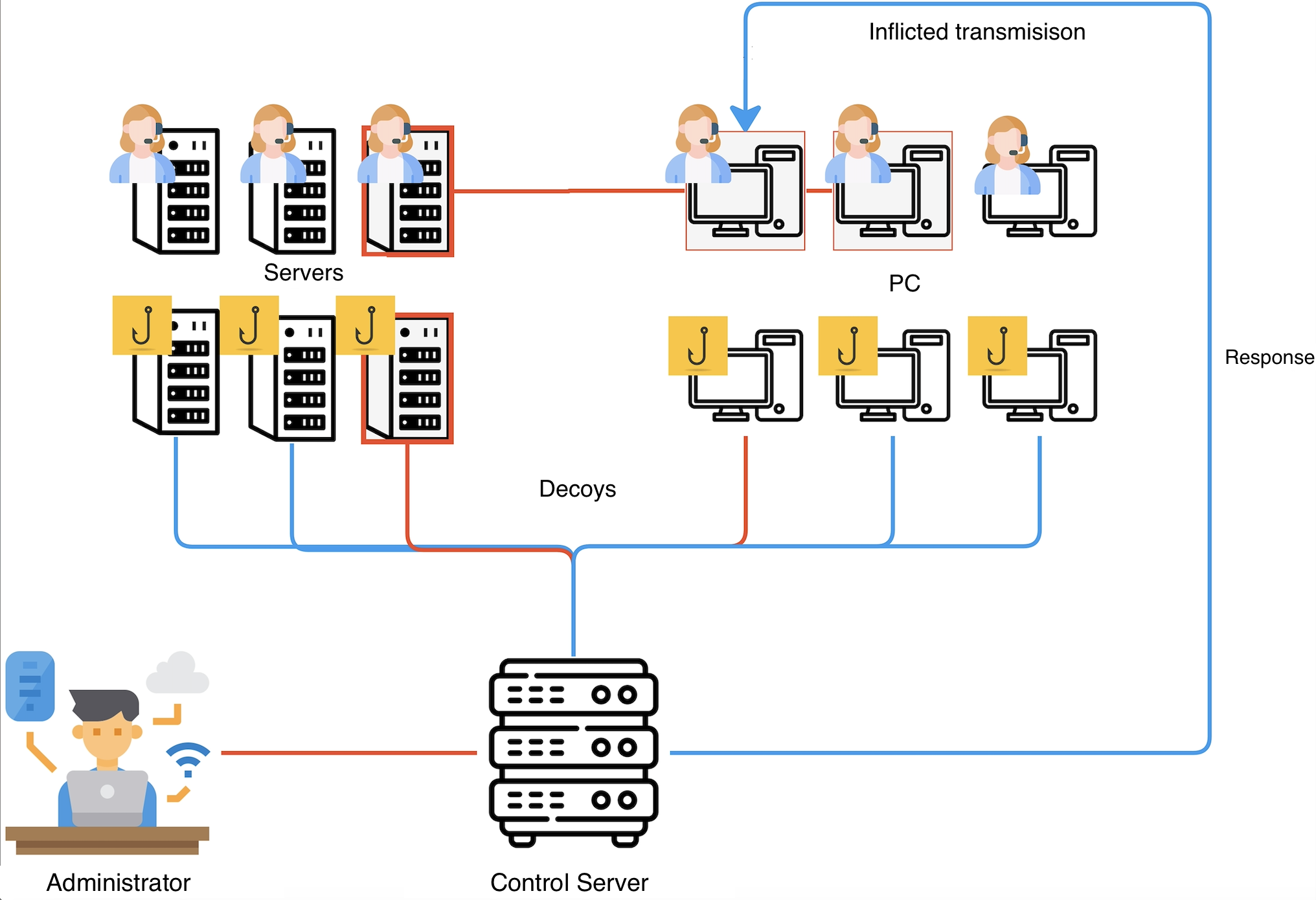
The object of research are decoys with dynamic attributes. This paper discusses the impact of decoys involving blockchain technologies on the state of information security of the organization and the process of researching cybercrime. This is important because most cybercrimes are detected after the attacker gains access to sensitive data. Through systematic analysis of the literature focused on assessing the capabilities of decoy and blockchain technologies, this work identifies the main advantages of decoys that utilize blockchain technology. To assess the effectiveness of attacker detection and cybercrime analysis, controlled experiments were conducted using a blockchain-based decoy system that we developed aimed at determining network performance.
As part of the study reported here, a technique is proposed to detect cybercrime using decoys based on blockchain technology. This technique is based on the fact that the attributes of the system change dynamically. Such a technique has made it possible to obtain a system model that solves the task of detecting decoys by intruders. In addition, the developed scheme reduces the load in contrast to the conventional fixed solution.
The results indicate that the response time of services is significantly reduced in the environment of decoys with dynamic attributes. For example, Nginx's response time in a static host is twice as high as dynamic, and an Apache dynamic server can still respond to an intruder's attack even if a static server fails. Therefore, the results reported in the article give grounds to assert the possibility of using the solution in the infrastructure of information systems at the public and private levels
References
- Anirudh, M., Thileeban, S. A., Nallathambi, D. J. (2017). Use of honeypots for mitigating DoS attacks targeted on IoT networks. 2017 International Conference on Computer, Communication and Signal Processing (ICCCSP). doi: https://doi.org/10.1109/icccsp.2017.7944057
- Sardana, A., Joshi, R. (2009). An auto-responsive honeypot architecture for dynamic resource allocation and QoS adaptation in DDoS attacked networks. Computer Communications, 32 (12), 1384–1399. doi: https://doi.org/10.1016/j.comcom.2009.03.005
- Kuwatly, L., Sraj, M., Al Masri, Z., Artail, H. (2004). A dynamic honeypot design for intrusion detection. The IEEE/ACS International Conference OnPervasive Services, 2004. ICPS 2004. Proceedings. doi: https://doi.org/10.1109/perser.2004.1356776
- Artail, H., Safa, H., Sraj, M., Kuwatly, I., Al-Masri, Z. (2006). A hybrid honeypot framework for improving intrusion detection systems in protecting organizational networks. Computers & Security, 25 (4), 274–288. doi: https://doi.org/10.1016/j.cose.2006.02.009
- Saeedi, A., Nassiri, M., Khotanlou, H. (2012). A dynamic approach for honeypot management. International Journal of Information, Security and Systems Management, 1 (2), 104–109.
- Fan, W., Fernández, D., Du, Z. (2015). Adaptive and Flexible Virtual Honeynet. Mobile, Secure, and Programmable Networking, 1–17. doi: https://doi.org/10.1007/978-3-319-25744-0_1
- Hecker, C., Hay, B. (2013). Automated Honeynet Deployment for Dynamic Network Environment. 2013 46th Hawaii International Conference on System Sciences. doi: https://doi.org/10.1109/hicss.2013.110
- Fraunholz, D., Zimmermann, M., Schotten, H. D. (2017). An adaptive honeypot configuration, deployment and maintenance strategy. 2017 19th International Conference on Advanced Communication Technology (ICACT). doi: https://doi.org/10.23919/icact.2017.7890056
- Fan, W., Fernández, D., Du, Z. (2017). Versatile virtual honeynet management framework. IET Information Security, 11 (1), 38–45. doi: https://doi.org/10.1049/iet-ifs.2015.0256
- Casino, F., Dasaklis, T. K., Patsakis, C. (2019). A systematic literature review of blockchain-based applications: Current status, classification and open issues. Telematics and Informatics, 36, 55–81. doi: https://doi.org/10.1016/j.tele.2018.11.006
- Hepp, T., Wortner, P., Schönhals, A., Gipp, B. (2018). Securing Physical Assets on the Blockchain. Proceedings of the 1st Workshop on Cryptocurrencies and Blockchains for Distributed Systems. doi: https://doi.org/10.1145/3211933.3211944
- Cruz, J. P., Kaji, Y., Yanai, N. (2018). RBAC-SC: Role-Based Access Control Using Smart Contract. IEEE Access, 6, 12240–12251. doi: https://doi.org/10.1109/access.2018.2812844
- Swan, M. (2015). Blockchain Thinking: The Brain as a Decentralized Autonomous Corporation [Commentary]. IEEE Technology and Society Magazine, 34 (4), 41–52. doi: https://doi.org/10.1109/mts.2015.2494358
- Schütte, J., Fridgen, G., Prinz, W., Rose, T., Urbach, N., Hoeren, T. et al. (2018). Blockchain and Smart Contracts. Technologies, Research Issues and Applications. Fraunhofer. Available at: https://www.iuk.fraunhofer.de/content/dam/iuk/en/docs/Fraunhofer-Paper_Blockchain-and-Smart-Contracts_EN.pdf
- Susukailo, V., Vasylyshyn, S., Opirskyy, I., Buriachok, V. (2021). Cybercrimes investigation via honeypots in cloud environments. CEUR Workshop, 2923, 91–96. Available at: https://ceur-ws.org/Vol-2923/paper10.pdf
- Opirskyy, I., Vasylyshyn, S., Piskozub, A. (2020). Analysis of the use of software baits (honeypots) as a means of ensuring information security. Cybersecurity: Education, Science, Technique, 2 (10), 88–97. doi: https://doi.org/10.28925/2663-4023.2020.10.8897
- Dudykevych, V., Prokopyshyn, I., Chekurin, V., Opirskyy, I., Lakh, Y., Kret, T. et al. (2019). A multicriterial analysis of the efficiency of conservative information security systems. Eastern-European Journal of Enterprise Technologies, 3 (9 (99)), 6–13. doi: https://doi.org/10.15587/1729-4061.2019.166349
- Banafa, A. (2016). How to Secure the Internet of Things (IoT) with Blockchain. Datafloq. Available at: https://datafloq.com/read/securing-internet-of-things-iot-with-blockchain/
- Pulling fraud out of the shadows. Global Economic Crime and Fraud Survey 2018. PwC. Available at: https://www.pwc.com/gx/en/news-room/docs/pwc-global-economic-crime-survey-report.pdf
- McLaughlin, M.-D., Gogan, J. (2018). Challenges and best practices in information security management. MIS Quarterly Executive, 17 (3), 237–262.
- Joshi, R. C., Sardana, A. (2011). Honeypots. CRC Press, 340. doi: https://doi.org/10.1201/b10738
- Zhuravchak, D. (2021). Ransomware spread prevention system using python, auditd and linux. Cybersecurity: Education, Science, Technique, 4 (12), 108–116. doi: https://doi.org/10.28925/2663-4023.2021.12.108116
- Gandotra, V., Singhal, A., Bedi, P. (2012). Threat-Oriented Security Framework: A Proactive Approach in Threat Management. Procedia Technology, 4, 487–494. doi: https://doi.org/10.1016/j.protcy.2012.05.078
- Onaolapo, J., Mariconti, E., Stringhini, G. (2016). What Happens After You Are Pwnd. Proceedings of the 2016 Internet Measurement Conference. doi: https://doi.org/10.1145/2987443.2987475
- Bamert, T., Decker, C., Elsen, L., Wattenhofer, R., Welten, S. (2013). Have a snack, pay with Bitcoins. IEEE P2P 2013 Proceedings. doi: https://doi.org/10.1109/p2p.2013.6688717
- How blockchain can transform defence assets and give armed forces an advantage on the battlefield (2020). PwC. Available at: https://www.pwc.com/gx/en/aerospace-defence/pdf/blockchain-defence.pdf
- Beecroft, N. (2015). Emerging Risk Report – 2015. Bitcoin. Lloyds. Available at: https://assets.lloyds.com/assets/pdf-bitcoin-bitcoin-final/1/pdf-bitcoin-bitcoin-final.pdf
- Bentov, I., Lee, C., Mizrahi, A., Rosenfeld, M. (2014). Paper 2014/452. Proof of Activity: Extending Bitcoin’s Proof of Work via Proof of Stake. Cryptology ePrint Archive. Available at: https://eprint.iacr.org/2014/452
- BGP hijacking. Wikipedia. Available at: https://en.wikipedia.org/w/index.php?title=BGP_hijacking&oldid=820773357
- Bissias, G., Ozisik, A. P., Levine, B. N., Liberatore, M. (2014). Sybil-Resistant Mixing for Bitcoin. Proceedings of the 13th Workshop on Privacy in the Electronic Society. doi: https://doi.org/10.1145/2665943.2665955
- Bitcoin Block Reward Halving Countdown. Available at: https://www.bitcoinblockhalf.com/
- Grafiki blokcheyna. Available at: https://www.blockchain.com/explorer/charts
- Bitcoin Energy Consumption Index. Available at: https://digiconomist.net/bitcoin-energy-consumption
- Cryptocurrency statistics. Available at: https://bitinfocharts.com/
- How much of BIP 62 ("Dealing with malleability") has been implemented? Available at: https://bitcoin.stackexchange.com/questions/35904/how-much-of-bip-62-dealing-with-malleability-has-been-implemented
- Blockchain and Distributed Ledger Technology (DLT). Available at: https://www.geeksforgeeks.org/blockchain-and-distributed-ledger-technology-dlt/
- Bonneau, J. Why buy when you can rent? Bribery attacks on Bitcoin-style consensus. Available at: https://jbonneau.com/doc/BFGKN14-bitcoin_bribery.pdf
- Bos, J. W., Halderman, J. A., Heninger, N., Moore, J., Naehrig, M., Wustrow, E. (2013). Paper 2013/734. Elliptic Curve Cryptography in Practice. Cryptology ePrint Archive. Available at: https://eprint.iacr.org/2013/734
- Boverman, A. (2011). Timejacking & Bitcoin. Culubas. Available at: http://culubas.blogspot.com/2011/05/timejacking-bitcoin_802.html
- Bruce, J. D. (2014). The Mini-Blockchain Scheme. Available at: https://www.weusecoins.com/assets/pdf/library/The%20Mini-Blockchain%20Scheme.pdf
- Buldas, A., Kroonmaa, A., Laanoja, R. (2013). Paper 2013/834. Keyless Signatures' Infrastructure: How to Build Global Distributed Hash-Trees. Cryptology ePrint Archive. Available at: https://eprint.iacr.org/2013/834
- Buterin, V. (2014). A next-generation smart contract and decentralized application platform. White Paper, 3 (37).
- Blockchain's Once-Feared 51% Attack Is Now Becoming Regular. Available at: https://www.coindesk.com/markets/2018/06/08/blockchains-once-feared-51-attack-is-now-becoming-regular/
- Castro, M., Liskov, B. (1999). Practical Byzantine Fault Tolerance. Proceedings of the Third Symposium on Operating Systems Design and Implementation. New Orleans. Available at: https://pmg.csail.mit.edu/papers/osdi99.pdf
- Chen, T., Li, X., Luo, X., Zhang, X. (2017). Under-optimized smart contracts devour your money. 2017 IEEE 24th International Conference on Software Analysis, Evolution and Reengineering (SANER). doi: https://doi.org/10.1109/saner.2017.7884650
Downloads
Published
How to Cite
Issue
Section
License
Copyright (c) 2023 Sviatoslav Vasylyshyn, Vitalii Susukailo, Ivan Opirskyy, Yevhenii Kurii, Ivan Tyshyk

This work is licensed under a Creative Commons Attribution 4.0 International License.
The consolidation and conditions for the transfer of copyright (identification of authorship) is carried out in the License Agreement. In particular, the authors reserve the right to the authorship of their manuscript and transfer the first publication of this work to the journal under the terms of the Creative Commons CC BY license. At the same time, they have the right to conclude on their own additional agreements concerning the non-exclusive distribution of the work in the form in which it was published by this journal, but provided that the link to the first publication of the article in this journal is preserved.
A license agreement is a document in which the author warrants that he/she owns all copyright for the work (manuscript, article, etc.).
The authors, signing the License Agreement with TECHNOLOGY CENTER PC, have all rights to the further use of their work, provided that they link to our edition in which the work was published.
According to the terms of the License Agreement, the Publisher TECHNOLOGY CENTER PC does not take away your copyrights and receives permission from the authors to use and dissemination of the publication through the world's scientific resources (own electronic resources, scientometric databases, repositories, libraries, etc.).
In the absence of a signed License Agreement or in the absence of this agreement of identifiers allowing to identify the identity of the author, the editors have no right to work with the manuscript.
It is important to remember that there is another type of agreement between authors and publishers – when copyright is transferred from the authors to the publisher. In this case, the authors lose ownership of their work and may not use it in any way.








