Determining the patterns of using information protection systems at financial institutions in order to improve the level of financial security
DOI:
https://doi.org/10.15587/1729-4061.2023.288175Keywords:
information security, information protection, financial market entities, financial security, digitalizationAbstract
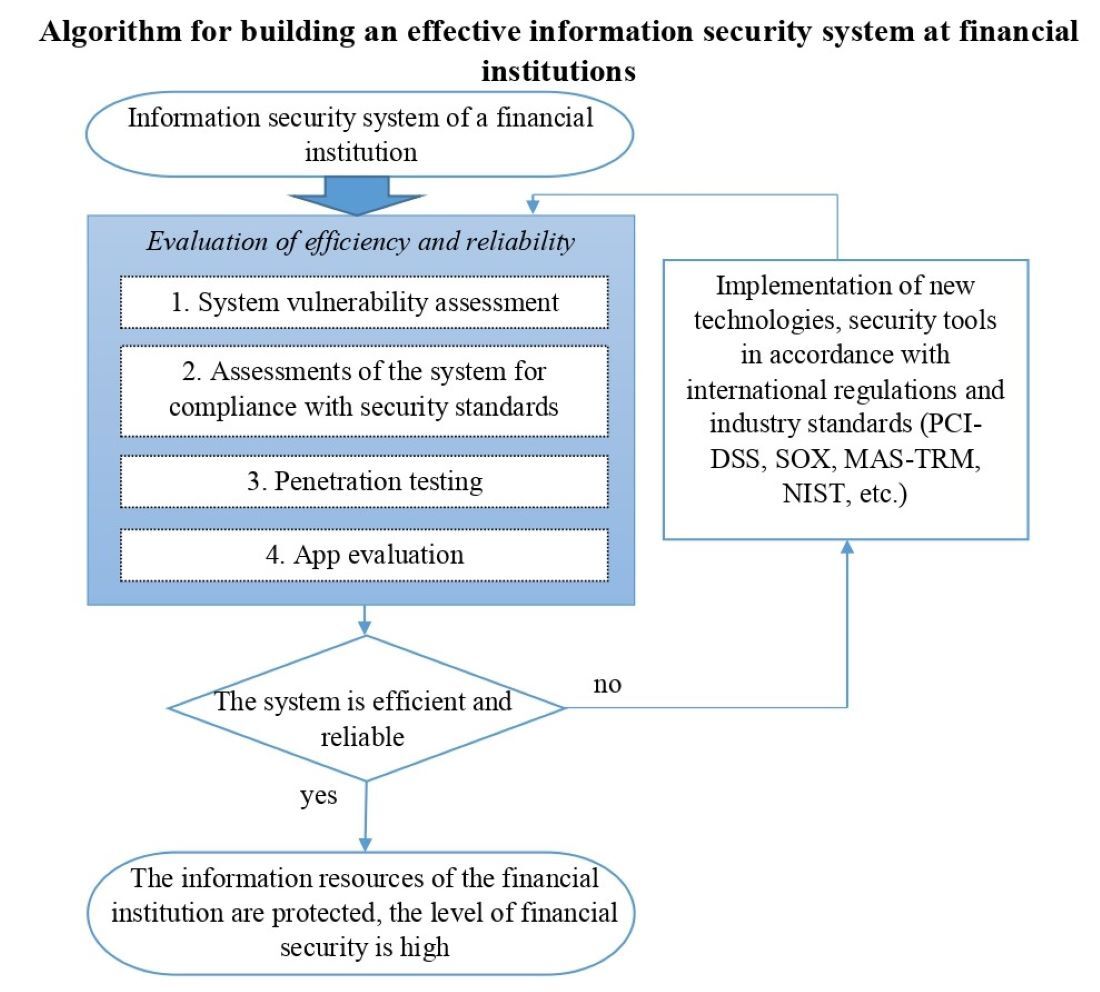
This paper reports a study aimed at determining the features of using information protection systems at financial institutions in order to improve the level of financial security. It has been proven that under the conditions of digitization of the business environment, information provision is the basis of financial security at both the macro and micro levels. Information has become a strategic resource that needs protection due to the spread of cybercrime. The level of efficiency of information provision and the level of financial security of Ukraine was determined, and the relationship between them was confirmed. Attention is focused on the need to improve these indicators. It has been proven that an effective information protection system enables economic entities to resist dangers and threats. It was substantiated that the intensification of the processes of digitalization of economic activity had created prerequisites for the growth of risks and threats to the integral, uninterrupted, protected circulation of information resources of financial institutions, which leads to huge financial losses. This requires improvement of existing information protection systems. A topology of information protection systems has been presented. An algorithm for building effective information protection systems of financial institutions was proposed, which includes system vulnerability assessment, system assessment for compliance with security standards, penetration testing, and application assessment. Its application would allow financial market entities to promptly respond to real and potential threats, increase the level of information security, and ensure financial stability. The results of the study could also be used by state and local authorities to devise the principles of financial security management at the macro level under the conditions of the digital economy
References
- Onyshchenko, S., Brychko, М., Litovtseva, V., Yevsieieva, A. (2022). Trust in the financial sector: a new approach to conceptualizing and measuring. Financial and Credit Activity Problems of Theory and Practice, 1 (42), 206–217. doi: https://doi.org/10.55643/fcaptp.1.42.2022.3735
- Varnalii, Z., Bondarenko, S. (2023). Financial security of Ukrainian enterprises during the war and post-war period. University Economic Bulletin, 56, 106–113. doi: https://doi.org/10.31470/2306-546x-2023-56-106-113
- Onyshchenko, V., Yehorycheva, S., Maslii, O., Yurkiv, N. (2021). Impact of Innovation and Digital Technologies on the Financial Security of the State. Proceedings of the 3rd International Conference on Building Innovations, 749–759. doi: https://doi.org/10.1007/978-3-030-85043-2_69
- Varnalii, Z., Mekhed, A. (2022). Business entities` financial security under digital economy. Financial and Credit Activity Problems of Theory and Practice, 4 (45), 267–275. doi: https://doi.org/10.55643/fcaptp.4.45.2022.3813
- Yusif, S., Hafeez-Baig, A. (2021). A Conceptual Model for Cybersecurity Governance. Journal of Applied Security Research, 16 (4), 490–513. doi: https://doi.org/10.1080/19361610.2021.1918995
- Hidouri, A., Hajlaoui, N., Touati, H., Hadded, M., Muhlethaler, P. (2022). A Survey on Security Attacks and Intrusion Detection Mechanisms in Named Data Networking. Computers, 11 (12), 186. doi: https://doi.org/10.3390/computers11120186
- Slayton, R. (2020). Governing Uncertainty or Uncertain Governance? Information Security and the Challenge of Cutting Ties. Science, Technology, & Human Values, 46 (1), 81–111. doi: https://doi.org/10.1177/0162243919901159
- Verhelst, A., Wouters, J. (2020). Filling Global Governance Gaps in Cybersecurity: International and European Legal Perspectives. International Organisations Research Journal, 15 (2), 141–172. doi: https://doi.org/10.17323/1996-7845-2020-02-07
- Amankwa, E., Loock, M., Kritzinger, E. (2018). Establishing information security policy compliance culture in organizations. Information & Computer Security, 26 (4), 420–436. doi: https://doi.org/10.1108/ics-09-2017-0063
- Zubko, T., Hanechko, I., Trubei, O., Afanasyev, K. (2021). Determining the impact of digitalization on the economic security of trade. Eastern-European Journal of Enterprise Technologies, 6 (13 (114)), 60–71. doi: https://doi.org/10.15587/1729-4061.2021.248230
- Kondratenko, N. O., Doroshenko, H. O., Ternova, I. A., Babych, S. N., Dorosheko, O. G. (2021). Organizational and methodical provision of the financial and economic security management of the enterprise. Financial and Credit Activity Problems of Theory and Practice, 1 (32), 129–137. doi: https://doi.org/10.18371/fcaptp.v1i32.200301
- Onyshchenko, S., Yanko, A., Hlushko, A., Maslii, O., Skryl, V. (2023). The Mechanism of Information Security of the National Economy in Cyberspace. Proceedings of the 4th International Conference on Building Innovations, 791–803. doi: https://doi.org/10.1007/978-3-031-17385-1_67
- Pro zatverdzhennia Metodychnykh rekomendatsiy shchodo rozrakhunku rivnia ekonomichnoi bezpeky Ukrainy: Nakaz Ministerstva ekonomichnoho rozvytku i torhivli Ukrainy vid 29.10.2013 No. 1277. Available at: http://search.ligazakon.ua/l_doc2.nsf/link1/ME131588.html
- Pronoza, P., Kuzenko, T., Sablina, N. (2022). Implementation of strategic tools in the process of financial security management of industrial enterprises in Ukraine. Eastern-European Journal of Enterprise Technologies, 2 (13 (116)), 15–23. doi: https://doi.org/10.15587/1729-4061.2022.254234
- Onyshchenko, S., Shchurov, I., Cherviak, A., Kivshyk, O. (2023). Methodical approach to assessing financial and credit institutions’ economic security level. Financial and Credit Activity Problems of Theory and Practice, 2 (49), 65–78. doi: https://doi.org/10.55643/fcaptp.2.49.2023.4037
- Stechyshyn, Y. (2023). The role and place of information and analytical support determination in the economic security system. Scientific Notes of «KROK» University, 1, 110–119. doi: https://doi.org/10.31732/2663-2209-2022-69-110-119
- Khvalchyk, I. (2020). Summary of information-analytical safety management of enterprise. Economics: Time Realities, 1 (47), 84–90. doi: https://doi.org/10.15276/etr.01.2020.10
- Onyshchenko, S., Bilko, S., Yanko, A., Sivitska, S. (2023). Business Information Security. Proceedings of the 4th International Conference on Building Innovations, 769–778. doi: https://doi.org/10.1007/978-3-031-17385-1_65
- World Press Freedom Index 2021. Available at: https://rsf.org/en/index?year=2021
- Social Progress Index. Executive Summary. Available at: https://www.socialprogress.org/static/9e62d6c031f30344f34683259839760d/2021%20Social%20Progress%20Index%20Executive%20Summary-compressed_0.pdf
- Onyshchenko, S., Skryl, V., Hlushko, A., Maslii, O. (2023). Inclusive Development Index. Proceedings of the 4th International Conference on Building Innovations, 779–790. doi: https://doi.org/10.1007/978-3-031-17385-1_66
- UN E-Government Survey 2020. Available at: https://publicadministration.un.org/egovkb/en-us/Reports/UN-E-Government-Survey-2020
- Global Innovation Index 2021. Available at: https://www.wipo.int/global_innovation_index/en/2021/
- Glushko, А. D. (2013). Directions of Efficiency Increase of State Regulatory Policy in Ukraine. World Applied Sciences Journal, 27 (4), 448–453. Available at: https://idosi.org/wasj/wasj27(4)13/6.pdf
- Onyshchenko, S., Maslii, O., Kivshyk, O., Cherviak, A. (2023). the impact of the insurance market on the financial security of Ukraine. Financial and Credit Activity Problems of Theory and Practice, 1 (48), 268–281. doi: https://doi.org/10.55643/fcaptp.1.48.2023.3976
- Onyshchenko, V., Onyshchenko, S., Verhal, K., Buriak, A. (2023). The Energy Efficiency of the Digital Economy. Proceedings of the 4th International Conference on Building Innovations, 761–767. doi: https://doi.org/10.1007/978-3-031-17385-1_64
- Onyshchenko, V., Onyshchenko, S., Maslii, O., Maksymenko, A. (2023). Systematization of Threats to Financial Security of Individual, Society, Business and the State in Terms of the Pandemic. Proceedings of the 4th International Conference on Building Innovations, 749–760. doi: https://doi.org/10.1007/978-3-031-17385-1_63
- Zhyvylo, Y., Shevchenko, D., Chernonog, O. (2021). Typology of cyber security systems in information and telecommunication systems of military (special) purpose. Modern Information Technologies in the Sphere of Security and Defence, 42 (3), 37–44. doi: https://doi.org/10.33099/2311-7249/2021-42-3-37-44
- Glushko, A., Marchyshynets, O. (2018). Institutional provision of the state regulatory policy in Ukraine. Journal of Advanced Research in Law and Economics, 9 (3 (33)), 941–948. Available at: https://journals.aserspublishing.eu/jarle/article/view/2536
- PCI DSS (Payment Card Industry Data Security Standard). Available at: https://platon.ua/faq/pci-dss
- Information security, Cybersecurity and the IEC 62443 series of standards (2022). Available at: https://ikmj.com/en/information-security-cybersecurity-and-the-iec-62443-series-of-standards/
- CIS Controls Implementation Guide for SMEs. Available at: https://www.cisecurity.org/wp-content/uploads/2017/09/CIS-Controls-Guide-for-SMEs.pdf
- International Organization for Standardization. Available at: https://www.iso.org/home.html
- Svistun, L., Glushko, А., Shtepenko, K. (2018). Organizational Aspects of Development Projects Implementation at the Real Estate Market in Ukraine. International Journal of Engineering & Technology, 7 (3.2), 447. doi: https://doi.org/10.14419/ijet.v7i3.2.14569
- CVE. Available at: https://cve.mitre.org/
- CVSS. Available at: https://www.first.org/cvss/
- Burp Suite. Available at: https://portswigger.net/burp/
- Moral-García, S., Moral-Rubio, S., Fernández, E. B., Fernández-Medina, E. (2014). Enterprise security pattern: A model-driven architecture instance. Computer Standards & Interfaces, 36 (4), 748–758. doi: https://doi.org/10.1016/j.csi.2013.12.009
- Wu, X., Zheng, W., Chen, X., Wang, F., Mu, D. (2020). CVE-assisted large-scale security bug report dataset construction method. Journal of Systems and Software, 160, 110456. doi: https://doi.org/10.1016/j.jss.2019.110456
Downloads
Published
How to Cite
Issue
Section
License
Copyright (c) 2023 Svitlana Onyshchenko, Yevhen Zhyvylo, Anna Cherviak, Stanislav Bilko

This work is licensed under a Creative Commons Attribution 4.0 International License.
The consolidation and conditions for the transfer of copyright (identification of authorship) is carried out in the License Agreement. In particular, the authors reserve the right to the authorship of their manuscript and transfer the first publication of this work to the journal under the terms of the Creative Commons CC BY license. At the same time, they have the right to conclude on their own additional agreements concerning the non-exclusive distribution of the work in the form in which it was published by this journal, but provided that the link to the first publication of the article in this journal is preserved.
A license agreement is a document in which the author warrants that he/she owns all copyright for the work (manuscript, article, etc.).
The authors, signing the License Agreement with TECHNOLOGY CENTER PC, have all rights to the further use of their work, provided that they link to our edition in which the work was published.
According to the terms of the License Agreement, the Publisher TECHNOLOGY CENTER PC does not take away your copyrights and receives permission from the authors to use and dissemination of the publication through the world's scientific resources (own electronic resources, scientometric databases, repositories, libraries, etc.).
In the absence of a signed License Agreement or in the absence of this agreement of identifiers allowing to identify the identity of the author, the editors have no right to work with the manuscript.
It is important to remember that there is another type of agreement between authors and publishers – when copyright is transferred from the authors to the publisher. In this case, the authors lose ownership of their work and may not use it in any way.








