Construction of a model of steganographic embedding of the UAV identifier into ADS-B data
DOI:
https://doi.org/10.15587/1729-4061.2023.288178Keywords:
unmanned aerial vehicles, ADS-B system, information security, steganographic data protection, GERT networkAbstract
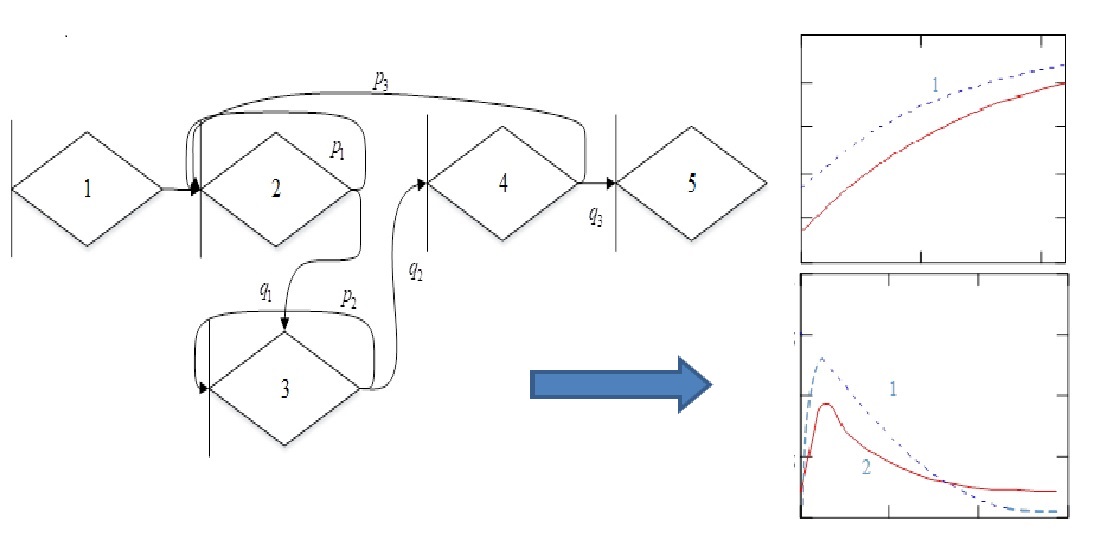
Secure data exchange in the control system of unmanned aerial vehicles (UAVs) is an important aspect for preventing unauthorized access and safety of aerial vehicles. Given the problems of automatic dependent surveillance-broadcast (ADS-B) data protection, the safety level of UAV flight tasks and air traffic in general is significantly reduced. Therefore, the protection of ADS-B data is an urgent task. The object of the study is the process of steganographic protection of ADS-B format data. A relevant problem of estimating the probabilistic time characteristics of the steganographic protection process is solved, taking into account the features of data embedding in the ADS-B format container. To solve it, a mathematical formalization of the methods of finding probabilistic-temporal characteristics of steganographic systems was carried out. A model of steganographic data transformation operations based on the Chinese remainder theorem has been built. The main difference of the model is taking into account the features of the ADS-B format data. This made it possible to formalize and evaluate the time functions of steganographic encoding and decoding of UAV identifiers with an integrated ADS-B system. A model of steganographic data transformation operations based on the finite integral ring theorem has been constructed. A list of operations performed in the developed algorithm has been compiled. This made it possible to carry out mathematical formalization of operations for complex use in the model of steganographic protection of UAV identifiers with a built-in ADS-B system. The mathematical model was studied and the estimation of the random value of the time of steganographic transformation of data, as well as the confidence interval, was performed. With the help of the reported set of models, it is possible to estimate the probability of the algorithm’s execution time falling within the given interval. The results of the calculation of probabilistic-time characteristics could be used in models of a higher level of the hierarchy
References
- Wu, Z., Shang, T., Guo, A. (2020). Security Issues in Automatic Dependent Surveillance - Broadcast (ADS-B): A Survey. IEEE Access, 8, 122147–122167. doi: https://doi.org/10.1109/access.2020.3007182
- Perkaus, J. (2020). ADS-B Cyber Security alert. Available at: https://www.perkausandfarley.com/wp-content/uploads/2022/01/ADSBCyberSecurity.pdf
- Alghamdi, F., Alshhrani, A., Hamza, N. (2018). Effective Security Techniques for Automatic Dependent Surveillance-Broadcast (ADS-B). International Journal of Computer Applications, 180 (26), 23–28. doi: https://doi.org/10.5120/ijca2018916598
- Habibi Markani, J., Amrhar, A., Gagné, J.-M., Landry, R. J. (2023). Security Establishment in ADS-B by Format-Preserving Encryption and Blockchain Schemes. Applied Sciences, 13 (5), 3105. doi: https://doi.org/10.3390/app13053105
- Semenov, S., Zhang, M. J. (2022). Comparative studies of methods for improving the cyber security of unmanned aerial vehicles with the built-in ADS-B system. Advanced Information Systems, 6 (4), 69–73. doi: https://doi.org/10.20998/2522-9052.2022.4.10
- Desai, L., Mali, S. (2018). Crypto-Stego-Real-Time (CSRT) System for Secure Reversible Data Hiding. VLSI Design, 2018, 1–8. doi: https://doi.org/10.1155/2018/4804729
- Shahadi, H. I., Kod, M. S., Qasem, B., Farhan, H. R. (2021). Real-Time Scheme for Covert Communication Based VoIP. Journal of Physics: Conference Series, 1997 (1), 012020. doi: https://doi.org/10.1088/1742-6596/1997/1/012020
- Kuznetsov, A., Onikiychuk, A., Peshkova, O., Gancarczyk, T., Warwas, K., Ziubina, R. (2022). Direct Spread Spectrum Technology for Data Hiding in Audio. Sensors, 22 (9), 3115. doi: https://doi.org/10.3390/s22093115
- Kharchenko, V., Kliushnikov, I., Rucinski, A., Fesenko, H., Illiashenko, O. (2022). UAV Fleet as a Dependable Service for Smart Cities: Model-Based Assessment and Application. Smart Cities, 5 (3), 1151–1178. doi: https://doi.org/10.3390/smartcities5030058
- Semenov, S., Zhang, M., Yenhalychev, S., Smidovych, L. (2022). Generalized model of the ADS-B unmanned aerial vehicle data transmission process in a steganographic system. Innovative Technologies and Scientific Solutions for Industries, 4 (22), 14–19. doi: https://doi.org/10.30837/itssi.2022.22.014
- Li, J., Chen, J. (2006). The Number Theoretical Method in Response Analysis of Nonlinear Stochastic Structures. Computational Mechanics, 39 (6), 693–708. doi: https://doi.org/10.1007/s00466-006-0054-9
- Baake, M., Bustos, Á., Huck, C., Lemańczyk, M., Nickel, A. (2020). Number-theoretic positive entropy shifts with small centralizer and large normalizer. Ergodic Theory and Dynamical Systems, 41 (11), 3201–3226. doi: https://doi.org/10.1017/etds.2020.111
- Alhassan, E. A., Tian, K., Abban, O. J., Ohiami, I. E., Michael Adjabui, M., Armah, G., Agyemang, S. (2021). On Some Algebraic Properties of the Chinese Remainder Theorem with Applications to Real Life. Journal of Applied Mathematics and Computation, 5 (3), 219–224. doi: https://doi.org/10.26855/jamc.2021.09.008
- Selianinau, M. (2020). An efficient implementation of the Chinese Remainder Theorem in minimally redundant Residue Number System. Computer Science, 21 (2). doi: https://doi.org/10.7494/csci.2020.21.2.3616
- Chatterjee, R., Bharti, S. (2018). Finding the ring of integers and its algorithms in algebraic number theory. International Journal of Engineering, Science and Mathematics, 7 (4 (1)), 41–44. Available at: https://www.ijesm.co.in/uploads/68/5367_pdf.pdf
- Kuchuk, N., Mozhaiev, O., Mozhaiev, M., Kuchuk, H. (2017). Method for calculating of R-learning traffic peakedness. 2017 4th International Scientific-Practical Conference Problems of Infocommunications. Science and Technology (PIC S&T). doi: https://doi.org/10.1109/infocommst.2017.8246416
- Kovalenko, A., Kuchuk, H., Kuchuk, N., Kostolny, J. (2021). Horizontal scaling method for a hyperconverged network. 2021 International Conference on Information and Digital Technologies (IDT). doi: https://doi.org/10.1109/idt52577.2021.9497534
- Semenov, S., Davydov, V., Voloshyn, D. (2019). Obfuscated Code Quality Measurement. 2019 XXIX International Scientific Symposium “Metrology and Metrology Assurance” (MMA). doi: https://doi.org/10.1109/mma.2019.8936022
- Mozhaev, O., Kuchuk, H., Kuchuk, N., Mozhaev, M., Lohvynenko, M. (2017). Multiservice network security metric. 2017 2nd International Conference on Advanced Information and Communication Technologies (AICT). doi: https://doi.org/10.1109/aiact.2017.8020083
- Semenov, S., Zhang, L., Cao, W., Bulba, S., Babenko, V., Davydov, V. (2021). Development of a fuzzy GERT-model for investigating common software vulnerabilities. Eastern-European Journal of Enterprise Technologies, 6 (2 (114)), 6–18. doi: https://doi.org/10.15587/1729-4061.2021.243715
- Zhang, N., Ou, M., Liu, B., Liu, J. (2023). A GERT Network Model for input-output optimization of general aviation industry chain based on value flow. Computers & Industrial Engineering, 176, 108945. doi: https://doi.org/10.1016/j.cie.2022.108945
- Kuchuk, N., Mozhaiev, O., Semenov, S., Haichenko, A., Kuchuk, H., Tiulieniev, S. et al. (2023). Devising a method for balancing the load on a territorially distributed foggy environment. Eastern-European Journal of Enterprise Technologies, 1 (4 (121)), 48–55. doi: https://doi.org/10.15587/1729-4061.2023.274177
- Kuznetsov, A., Smirnov, O., Zhora, V., Onikiychuk, A., Pieshkova, O. (2021). Hiding Messages in Audio Files Using Direct Spread Spectrum. 2021 11th IEEE International Conference on Intelligent Data Acquisition and Advanced Computing Systems: Technology and Applications (IDAACS). doi: https://doi.org/10.1109/idaacs53288.2021.9660879
- Mammadov, F. K. (2023). New approach to book cipher: web pages as a cryptographic key. Advanced Information Systems, 7 (1), 59–65. doi: https://doi.org/10.20998/2522-9052.2023.1.10
- Aleksandrov, E., Aleksandrova, T., Kostianyk, I., Morgun, Y. (2023). Simulation of random external disturbance acting on the car body in the urgent braking mode. Advanced Information Systems, 7 (1), 14–17. doi: https://doi.org/10.20998/2522-9052.2023.1.02
- Chiocchio, S., Persia, A., Santucci, F., Graziosi, F., Pratesi, M., Faccio, M. (2020). Modeling and evaluation of enhanced reception techniques for ADS-B signals in high interference environments. Physical Communication, 42, 101171. doi: https://doi.org/10.1016/j.phycom.2020.101171
- Afanasyev, I., Sytnikov, V., Strelsov, O., Stupen, P. (2022). The Applying of Low Order Frequency-Dependent Components in Signal Processing of Autonomous Mobile Robotic Platforms. Intelligent Computing, 882–891. doi: https://doi.org/10.1007/978-3-031-10464-0_61
Downloads
Published
How to Cite
Issue
Section
License
Copyright (c) 2023 Serhii Semenov, Minjian Zhang, Oleksandr Mozhaiev, Nina Kuchuk, Serhii Tiulieniev, Yurii Gnusov, Mykhailo Mozhaiev, Volodymyr Strukov, Yurii Onishchenko, Heorhii Kuchuk

This work is licensed under a Creative Commons Attribution 4.0 International License.
The consolidation and conditions for the transfer of copyright (identification of authorship) is carried out in the License Agreement. In particular, the authors reserve the right to the authorship of their manuscript and transfer the first publication of this work to the journal under the terms of the Creative Commons CC BY license. At the same time, they have the right to conclude on their own additional agreements concerning the non-exclusive distribution of the work in the form in which it was published by this journal, but provided that the link to the first publication of the article in this journal is preserved.
A license agreement is a document in which the author warrants that he/she owns all copyright for the work (manuscript, article, etc.).
The authors, signing the License Agreement with TECHNOLOGY CENTER PC, have all rights to the further use of their work, provided that they link to our edition in which the work was published.
According to the terms of the License Agreement, the Publisher TECHNOLOGY CENTER PC does not take away your copyrights and receives permission from the authors to use and dissemination of the publication through the world's scientific resources (own electronic resources, scientometric databases, repositories, libraries, etc.).
In the absence of a signed License Agreement or in the absence of this agreement of identifiers allowing to identify the identity of the author, the editors have no right to work with the manuscript.
It is important to remember that there is another type of agreement between authors and publishers – when copyright is transferred from the authors to the publisher. In this case, the authors lose ownership of their work and may not use it in any way.








