Development of a mechanism for information security risk management of transport service provision systems
DOI:
https://doi.org/10.15587/1729-4061.2024.298144Keywords:
information security, countering threats, transport services, risk management, vulnerabilities and threatsAbstract
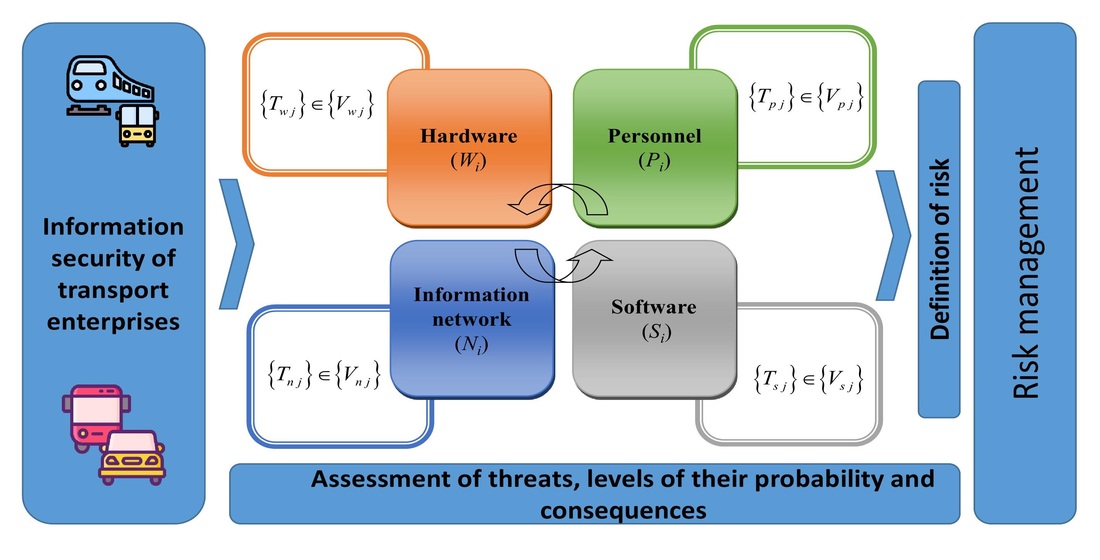
The object of the study is the process of analysis, assessment, and management of information security risks in transport service provision systems.
The problem of applying the information security risk management approach in the activities of transport business entities was investigated. As a result of the application of effective forms, methods, and means of information security risk management based on international standards, a risk management mechanism was developed. The risk assessment process of transport systems has been systematized. This allows business entities in the transport sector to determine ways to prevent and counter information threats and challenges in their activities, both when designing and operating systems for providing transport services.
Verification of the devised methodical approach to information security risk management was carried out on an example of the taxi company «Taxifay N». Threats and challenges of the company’s information system were evaluated by an expert method. Based on the results of the analysis of expert risk assessment, it was found that the concordance coefficient (0.86) confirms the high level of agreement of experts’ opinions. As a result, the company’s information security risk management program was developed. The effectiveness of the program was assessed by the efficiency ratio, which was 0.64. This testifies to the effectiveness of the implemented program of measures to manage information security risks.
The scope of application may be the activity of business entities that provide transport services to the population, aimed at data storage and processing.
The prospect of this study is to expand the list of threats and categories of vulnerabilities depending on the characteristics of the economic activity of various enterprises
References
- Ferdman, G. (2020). The essence of the concept of transport safety: public administration aspect. Law and Public Administration, 2, 231–236. https://doi.org/10.32840/pdu.2020.2.34
- Semeryanova, N., Mordvinov, A. (2019). Information security in the field of transport services. E3S Web of Conferences, 135, 04072. https://doi.org/10.1051/e3sconf/201913504072
- Tubis, A. (2018). Risk Assessment in Road Transport – Strategic and Business Approach. Journal of KONBiN, 45 (1), 305–324. https://doi.org/10.2478/jok-2018-0016
- Chow, A. H. F., Kuo, Y.-H., Angeloudis, P., Bell, M. G. H. (2020). Dynamic modelling and optimisation of transportation systems in the connected era. Transportmetrica B: Transport Dynamics, 10 (1), 801–802. https://doi.org/10.1080/21680566.2020.1851312
- Ersoy, P., Tanyeri, M. (2021). Risk management tools in the road transportation industry with mediation and moderation analysis. Scientific Journal of Logistics, 17 (4), 555–567. Available at: https://www.logforum.net/pdf/17_4_8_21.pdf
- Vagiokas, N., Zacharias, C. (2021). Tool for Analyzing the Risks in Dangerous Goods Transportation. OALib, 08 (05), 1–22. https://doi.org/10.4236/oalib.1107373
- Cheung, K.-F., Bell, M. G. H. (2021). Attacker–defender model against quantal response adversaries for cyber security in logistics management: An introductory study. European Journal of Operational Research, 291 (2), 471–481. https://doi.org/10.1016/j.ejor.2019.10.019
- Wu, P.-J., Chaipiyaphan, P. (2019). Diagnosis of delivery vulnerability in a logistics system for logistics risk management. The International Journal of Logistics Management, 31 (1), 43–58. https://doi.org/10.1108/ijlm-02-2019-0069
- Fan, H., Li, G., Sun, H., Cheng, T. C. E. (2017). An information processing perspective on supply chain risk management: Antecedents, mechanism, and consequences. International Journal of Production Economics, 185, 63–75. https://doi.org/10.1016/j.ijpe.2016.11.015
- Mohamed, I. B., Labarthe, O., Bouchery, Y., Klibi, W., Stauffer, G. (2023). Multi-echelon Urban Distribution Networks. The Routledge Handbook of Urban Logistics, 208–224. https://doi.org/10.4324/9781003241478-19
- Tang, C. S., Yang, S. A., Wu, J. (2019). Financing Suppliers under Performance Risk. Foundations and Trends® in Technology, Information and Operations Management, 12 (2-3), 135–151. https://doi.org/10.1561/0200000091
- Aven, T. (2015). On the allegations that small risks are treated out of proportion to their importance. Reliability Engineering & System Safety, 140, 116–121. https://doi.org/10.1016/j.ress.2015.04.001
- Andersson, A., Hedström, K., Karlsson, F. (2022). Standardizing information security – a structurational analysis. Information & Management, 59 (3), 103623. https://doi.org/10.1016/j.im.2022.103623
- The NIST Cybersecurity Framework 2.0 (2023). National Institute of Standards and Technology. https://doi.org/10.6028/nist.cswp.29.ipd
- Pizzi, G. (2020). Cybersecurity and its integration with safety for transport systems: not a formal fulfillment but an actual commitment. Transportation Research Procedia, 45, 250–257. https://doi.org/10.1016/j.trpro.2020.03.014
- Bélanger, F., Collignon, S., Enget, K., Negangard, E. (2017). Determinants of early conformance with information security policies. Information & Management, 54 (7), 887–901. https://doi.org/10.1016/j.im.2017.01.003
- Caralli, R. A., Stevens, J. F., Young, L. R. Wilson, W. R. (2007). Introducing OCTAVE Allegro: Improving the information security risk assessment process. https://doi.org/10.1184/R1/6574790.v1
- Threat Modeling. OWASP. Available at: https://owasp.org/www-community/Threat_Modeling
- Shameli-Sendi, A., Aghababaei-Barzegar, R., Cheriet, M. (2016). Taxonomy of information security risk assessment (ISRA). Computers & Security, 57, 14–30. https://doi.org/10.1016/j.cose.2015.11.001
- Haji, S., Tan, Q., Costa, R. S. (2019). A Hybrid Model for Information Security Risk Assessment. International Journal of Advanced Trends in Computer Science and Engineering, 8 (1.1), 100–106. https://doi.org/10.30534/ijatcse/2019/1981.12019
- van Ginkel, K. C. H., Dottori, F., Alfieri, L., Feyen, L., Koks, E. E. (2021). Flood risk assessment of the European road network. Natural Hazards and Earth System Sciences, 21 (3), 1011–1027. https://doi.org/10.5194/nhess-21-1011-2021
- Abrahamsen, E. B., Aven, T. (2012). Why risk acceptance criteria need to be defined by the authorities and not the industry? Reliability Engineering & System Safety, 105, 47–50. https://doi.org/10.1016/j.ress.2011.11.004
- Aven, T. (2014). The Concept of Antifragility and its Implications for the Practice of Risk Analysis. Risk Analysis, 35 (3), 476–483. https://doi.org/10.1111/risa.12279
- Kitsios, F., Chatzidimitriou, E., Kamariotou, M. (2022). Developing a Risk Analysis Strategy Framework for Impact Assessment in Information Security Management Systems: A Case Study in IT Consulting Industry. Sustainability, 14 (3), 1269. https://doi.org/10.3390/su14031269
- Smerichevskyi, S., Mykhalchenko, O., Poberezhna, Z., Kryvovyazyuk, I. (2023). Devising a systematic approach to the implementation of innovative technologies to provide the stability of transportation enterprises. Eastern-European Journal of Enterprise Technologies, 3 (13 (123)), 6–18. https://doi.org/10.15587/1729-4061.2023.279100
- Floreale, G., Baraldi, P., Lu, X., Rossetti, P., Zio, E. (2024). Sensitivity analysis by differential importance measure for unsupervised fault diagnostics. Reliability Engineering & System Safety, 243, 109846. https://doi.org/10.1016/j.ress.2023.109846
- Coit, D. W., Zio, E. (2019). The evolution of system reliability optimization. Reliability Engineering & System Safety, 192, 106259. https://doi.org/10.1016/j.ress.2018.09.008
- Sultana, S., Salon, D., Kuby, M. (2021). Transportation sustainability in the urban context: a comprehensive review. Geographic Perspectives on Urban Sustainability, 13–42. https://doi.org/10.4324/9781003130185-2
- Shahjee, D., Ware, N. (2022). Integrated Network and Security Operation Center: A Systematic Analysis. IEEE Access, 10, 27881–27898. https://doi.org/10.1109/access.2022.3157738
- Dubois, D. (2010). Representation, Propagation, and Decision Issues in Risk Analysis Under Incomplete Probabilistic Information. Risk Analysis, 30 (3), 361–368. https://doi.org/10.1111/j.1539-6924.2010.01359.x
- Fertis, A., Baes, M., Lüthi, H.-J. (2012). Robust risk management. European Journal of Operational Research, 222 (3), 663–672. https://doi.org/10.1016/j.ejor.2012.03.036
- Joshi, N. N., Lambert, J. H. (2011). Diversification of infrastructure projects for emergent and unknown non‐systematic risks. Journal of Risk Research, 14 (6), 717–733. https://doi.org/10.1080/13669877.2011.553733
- Maselli, G., Macchiaroli, M. (2020). Tolerability and Acceptability of the Risk for Projects in the Civil Sector. Smart Innovation, Systems and Technologies, 686–695. https://doi.org/10.1007/978-3-030-48279-4_64
- Reinert, J. M., Apostolakis, G. E. (2006). Including model uncertainty in risk-informed decision making. Annals of Nuclear Energy, 33 (4), 354–369. https://doi.org/10.1016/j.anucene.2005.11.010
- Shapiro, A. (2013). On Kusuoka Representation of Law Invariant Risk Measures. Mathematics of Operations Research, 38 (1), 142–152. https://doi.org/10.1287/moor.1120.0563
- Vanem, E. (2012). Ethics and fundamental principles of risk acceptance criteria. Safety Science, 50 (4), 958–967. https://doi.org/10.1016/j.ssci.2011.12.030
- Zsidisin, G. A. (2003). A grounded definition of supply risk. Journal of Purchasing and Supply Management, 9 (5-6), 217–224. https://doi.org/10.1016/j.pursup.2003.07.002
- Melnichenko, O., Ignatenko, O., Dmytrychenko, A., Dereguz, I. (2023). Logistics management of the system for providing transportation services to the population: anti-crisis aspect. The National Transport University Bulletin, 1 (55). https://doi.org/10.33744/2308-6645-2023-1-55-200-210
- Khrutba, V., Kharchenko, A., Khrutba, Y., Kolbasin, M., Tsybulskyi, V., Silantieva, I., Lysak, R. (2022). Applying a design mindset to develop a prototype of an electronic service for assessing the impact on the environment. Eastern-European Journal of Enterprise Technologies, 4 (2 (118)), 6–15. https://doi.org/10.15587/1729-4061.2022.262356
Downloads
Published
How to Cite
Issue
Section
License
Copyright (c) 2024 Olexandr Melnychenko, Oleksandr Ignatenko, Vitalii Tsybulskyi, Anastasia Degtiarova, Mykola Kashuba, Igor Derehuz

This work is licensed under a Creative Commons Attribution 4.0 International License.
The consolidation and conditions for the transfer of copyright (identification of authorship) is carried out in the License Agreement. In particular, the authors reserve the right to the authorship of their manuscript and transfer the first publication of this work to the journal under the terms of the Creative Commons CC BY license. At the same time, they have the right to conclude on their own additional agreements concerning the non-exclusive distribution of the work in the form in which it was published by this journal, but provided that the link to the first publication of the article in this journal is preserved.
A license agreement is a document in which the author warrants that he/she owns all copyright for the work (manuscript, article, etc.).
The authors, signing the License Agreement with TECHNOLOGY CENTER PC, have all rights to the further use of their work, provided that they link to our edition in which the work was published.
According to the terms of the License Agreement, the Publisher TECHNOLOGY CENTER PC does not take away your copyrights and receives permission from the authors to use and dissemination of the publication through the world's scientific resources (own electronic resources, scientometric databases, repositories, libraries, etc.).
In the absence of a signed License Agreement or in the absence of this agreement of identifiers allowing to identify the identity of the author, the editors have no right to work with the manuscript.
It is important to remember that there is another type of agreement between authors and publishers – when copyright is transferred from the authors to the publisher. In this case, the authors lose ownership of their work and may not use it in any way.








