Development of the sociocyberphysical systems` multi-contour security methodology
DOI:
https://doi.org/10.15587/1729-4061.2024.298844Keywords:
socio-cyberphysical system, cyber security, information security, security of information, critical infrastructure facilitiesAbstract
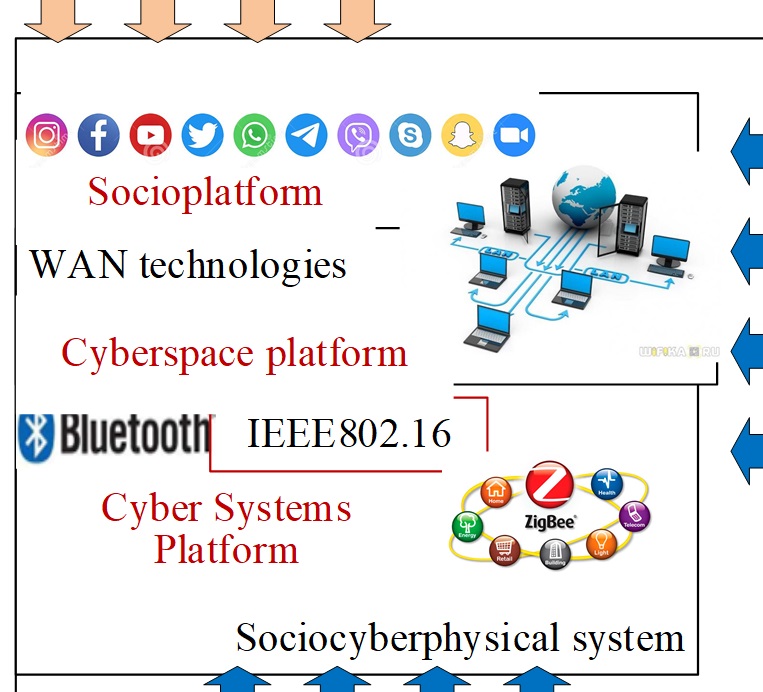
The constant increase in the number of threats to the security of critical infrastructure objects, which include socio-cyberphysical systems, leads to a decrease in the quality of security services and the level of security of infrastructure elements. The object of research is the process of building a complex system of protection in socio-cyberphysical systems. The imperfection of the mechanisms for ensuring the security of critical infrastructure objects, which include socio-cyberphysical systems, the technological complexity of identifying new security threats necessitates an urgent need for a radical revision of the current approaches to its provision. So, it becomes clear that the development of a new approach to ensuring the security of information resources in socio-cyberphysical systems is needed. The article proposes a new approach to the methodological foundations of building multi-contour information protection systems with internal and external circuits on each of the platforms of socio-cyberphysical systems. This approach is based on a universal classifier of threats, which takes into account not the technical aspect of threats, but also their integration with social engineering methods, their synergy of hybridity. The sociopolitical influence on the realization of threats is taken into account, and practical mechanisms for providing basic security services based on post-quantum algorithms are also proposed. To provide basic security services in the proposed multi-contour protection system, it is proposed to use post-quantum algorithms – McEliece crypto-code constructions, which provide Perr=10-9–10-12, safe time Tsec=1025–1035 group operations. Within the framework of the proposed approach, the problem of increasing the level of information security has been formalized and further ways of solving it have been determined
References
- Yevseiev, S., Ponomarenko, V., Laptiev, O., Milov, O., Korol, O., Milevskyi, S. et al.; Yevseiev, S., Ponomarenko, V., Laptiev, O., Milov, O. (Eds.) (2021). Synergy of building cybersecurity systems. Kharkiv: РС ТЕСHNOLOGY СЕNTЕR, 188. https://doi.org/10.15587/978-617-7319-31-2
- Yevseiev, S., Hryshchuk, R., Molodetska, K., Nazarkevych, M., Hrytsyk, V., Milov, O. et al.; Yevseiev, S., Hryshchuk, R., Molodetska, K., Nazarkevych, M. (Eds.) (2022). Modeling of security systems for critical infrastructure facilities. Kharkiv: РС ТЕСHNOLOGY СЕNTЕR, 196. https://doi.org/10.15587/978-617-7319-57-2
- Yevseiev, S., Khokhlachova, Yu., Ostapov, S., Laptiev, O., Korol, O., Milevskyi, S. et al.; Yevseiev, S., Khokhlachova, Yu., Ostapov, S., Laptiev, O. (Eds.) (2023). Models of socio-cyber-physical systems security. Kharkiv: РС ТЕСHNOLOGY СЕNTЕR, 184. https://doi.org/10.15587/978-617-7319-72-5
- Yevseiev, S., Dzheniuk, N., Tolkachov, M., Milov, O., Voitko, T., Prygara, M. et al. (2023). Development of a multi-loop security system of information interactions in socio-cyberphysical systems. Eastern-European Journal of Enterprise Technologies, 5 (9 (125)), 53–74. https://doi.org/10.15587/1729-4061.2023.289467
- Dzheniuk, N., Yevseiev, S., Lazurenko, B., Serkov, O., Kasilov, O. (2023). A method of protecting information in cyber-physical space. Advanced Information Systems, 7 (4), 80–85. https://doi.org/10.20998/2522-9052.2023.4.11
- Shmatko, O., Herasymov, S., Lysetskyi, Y., Yevseiev, S., Sievierinov, О., Voitko, T. et al. (2023). Development of the automated decision-making system synthesis method in the management of information security channels. Eastern-European Journal of Enterprise Technologies, 6 (9 (126)), 39–49. https://doi.org/10.15587/1729-4061.2023.293511
- Haag, S., Siponen, M., Liu, F. (2021). Protection Motivation Theory in Information Systems Security Research. ACM SIGMIS Database: The DATABASE for Advances in Information Systems, 52 (2), 25–67. https://doi.org/10.1145/3462766.3462770
- Li, Y., Xin, T., Siponen, M. (2022). Citizens’ Cybersecurity Behavior: Some Major Challenges. IEEE Security & Privacy, 20 (1), 54–61. https://doi.org/10.1109/msec.2021.3117371
- Shmatko, O., Balakireva, S., Vlasov, A., Zagorodna, N., Korol, O., Milov, O. et al. (2020). Development of methodological foundations for designing a classifier of threats to cyberphysical systems. Eastern-European Journal of Enterprise Technologies, 3 (9 (105)), 6–19. https://doi.org/10.15587/1729-4061.2020.205702
- Khoroshko, V. O., Pavlov, I. M., Bobalo, Y. Ya., Dudykevich, V. B. et al. (2020). Design of complex information protection systems. Lviv: Ed. Lviv Polytechnic, 320.
- Brailovskyi, M. M., Zybin, S. V., Piskun, I. V., Khoroshko, V. O., Khokhlacheva, Yu. E. (2021). Information protection technologies. Kyiv: Central Committee "Comprint", 296.
- Dudykevich, V. B., Khoroshko, V. O., Yaremchuk, Yu. E. (2018). Basics of information security. Vinnytsia: Ed. He. national technical Univ, 315.
- SHA-3 Standard: Permutation-Based Hash and Extendable-Output Functions. FIPS PUB 202. https://doi.org/10.6028/NIST.FIPS.202
- Migration to Post-Quantum Cryptography. Available at: https://www.nccoe.nist.gov/crypto-agility-considerations-migrating-post-quantum-cryptographic-algorithms
- Clarridge, A., Salomaa, K. (2009). A Cryptosystem Based on the Composition of Reversible Cellular Automata. Lecture Notes in Computer Science, 314–325. https://doi.org/10.1007/978-3-642-00982-2_27
- Lightweight Cryptography. Available at: https://csrc.nist.gov/Projects/lightweight-cryptography
- Davydiuk, A. (2023). Implementation of new tools and methods for increasing the level of cyber security of critical infrastructure objects. Ukrainian Scientific Journal of Information Security, 25 (3). https://doi.org/10.18372/2410-7840.25.17937
- Khomik, M., Harasymchuk, O. (2023). Analysis of threats to generators of pseudo-random numbers and pseudo-random sequences and protection measures. Ukrainian Information Security Research Journal, 25 (4). https://doi.org/10.18372/2410-7840.25.18222
- Klimovych, S. (2023). Methodology of traffic masking in a specialized data transmission network. Ukrainian Scientific Journal of Information Security, 25 (3). https://doi.org/10.18372/2410-7840.25.17935
- Risk assessment methodologies. Available at: https://www.cisa.gov/sites/default/files/publications/Risk%2520Assessment%2520Methodologies.pdf
- UNOCT launches Update of the UN Compendium of Good Practices on the Protection of Critical Infrastructure against Terrorist Attacks. Available at: https://www.un.org/counterterrorism/events/unoct-launches-2022-update-un-compendium-good-practices-protection-critical-infrastructure
- Methodology for assessing regional infrastructure resilience (2021). Washington. Available at: https://www.cisa.gov/sites/default/files/publications/DIS_DHS_Methodology_Report_ISD%2520EAD%2520Signed_with%2520alt-text_0.pdf
- Theocharidou, M., Giannopoulos, G. (2015). Risk assessment methodologies for critical infrastructure protection. Part II, A new approach. Publications Office of the European Union. https://doi.org/10.2788/621843
- Giannopoulos, G., Dorneanu, B., Jonkeren, O. (2013). Risk Assessment Methodology for Critical Infrastructure Protection. EUR 25745 EN. Luxembourg (Luxembourg): Publications Office of the European Union. Available at: https://publications.jrc.ec.europa.eu/repository/handle/JRC78292
- Threat and Hazard Identification and Risk Assessment (THIRA) and Stakeholder Preparedness Review (SPR) Guide (2018). Available at: https://www.fema.gov/sites/default/files/2020-07/threat-hazard-identification-risk-assessment-stakeholder-preparedness-review-guide.pdf
- National Protection Framework (2016). Available at: https://www.fema.gov/sites/default/files/2020-04/National_Protection_Framework2nd-june2016.pdf
- Yevseiev, S., Hryhorii, K., Liekariev, Y. (2016). Developing of multi-factor authentication method based on niederreiter-mceliece modified crypto-code system. Eastern-European Journal of Enterprise Technologies, 6 (4 (84)), 11–23. https://doi.org/10.15587/1729-4061.2016.86175
- Yevseiev, S., Korol, O., Kots, H. (2017). Construction of hybrid security systems based on the crypto-code structures and flawed codes. Eastern-European Journal of Enterprise Technologies, 4 (9 (88)), 4–21. https://doi.org/10.15587/1729-4061.2017.108461
- Yevseiev, S., Tsyhanenko, O., Ivanchenko, S., Aleksiyev, V., Verheles, D., Volkov, S. et al. (2018). Practical implementation of the Niederreiter modified cryptocode system on truncated elliptic codes. Eastern-European Journal of Enterprise Technologies, 6 (4 (96)), 24–31. https://doi.org/10.15587/1729-4061.2018.150903
- Yevseiev, S., Tsyhanenko, O., Gavrilova, A., Guzhva, V., Milov, O., Moskalenko, V. et al. (2019). Development of Niederreiter hybrid crypto-code structure on flawed codes. Eastern-European Journal of Enterprise Technologies, 1 (9 (97)), 27–38. https://doi.org/10.15587/1729-4061.2019.156620
- Yevseiev, S., Havrylova, A., Korol, O., Dmitriiev, O., Nesmiian, O., Yufa, Y., Hrebennikov, A. (2022). Research of collision properties of the modified UMAC algorithm on crypto-code constructions. EUREKA: Physics and Engineering, 1, 34–43. https://doi.org/10.21303/2461-4262.2022.002213
- Yevseiev, S., Havrylova, A., Milevskyi, S., Sinitsyn, I., Chalapko, V., Dukin, H. et al. (2023). Development of an improved SSL/TLS protocol using post-quantum algorithms. Eastern-European Journal of Enterprise Technologies, 3 (9 (123)), 33–48. https://doi.org/10.15587/1729-4061.2023.281795
- Pohasii, S., Yevseiev, S., Zhuchenko, O., Milov, O., Lysechko, V., Kovalenko, O. et al. (2022). Development of crypto-code constructs based on LDPC codes. Eastern-European Journal of Enterprise Technologies, 2 (9 (116)), 44–59. https://doi.org/10.15587/1729-4061.2022.254545
- Yevseiev, S., Abdalla, A., Osiievskyi, S., Larin, V., Lytvynenko, M. (2020). Development of an advanced method of video information resource compression in navigation and traffic control systems. EUREKA: Physics and Engineering, 5, 31–42. https://doi.org/10.21303/2461-4262.2020.001405
- Korchenko, A., Breslavskyi, V., Yevseiev, S., Zhumangalieva, N., Zvarych, A., Kazmirchuk, S. et al. (2021). Development of a method for constructing linguistic standards for multi-criteria assessment of honeypot efficiency. Eastern-European Journal of Enterprise Technologies, 1 (2 (109)), 14–23. https://doi.org/10.15587/1729-4061.2021.225346
- Yevseiev, S., Kuznietsov, O., Herasimov, S., Horielyshev, S., Karlov, A., Kovalov, I. et al. (2021). Development of an optimization method for measuring the Doppler frequency of a packet taking into account the fluctuations of the initial phases of its radio pulses. Eastern-European Journal of Enterprise Technologies, 2 (9 (110)), 6–15. https://doi.org/10.15587/1729-4061.2021.229221
- Yevseiev, S., Melenti, Y., Voitko, O., Hrebeniuk, V., Korchenko, A., Mykus, S. et al. (2021). Development of a concept for building a critical infrastructure facilities security system. Eastern-European Journal of Enterprise Technologies, 3 (9 (111)), 63–83. https://doi.org/10.15587/1729-4061.2021.233533
- Yevseiev, S., Laptiev, O., Lazarenko, S., Korchenko, A., Manzhul, I. (2021). Modeling the protection of personal data from trust and the amount of information on social networks. EUREKA: Physics and Engineering, 1, 24–31. https://doi.org/10.21303/2461-4262.2021.001615
- Cybersecurity classifier. Available at: https://skl.sspu.sumy.ua/
- Milevsky, S. (2023). Development of threat classifier in socio-cyber-physical systems. Ukrainian Scientific Journal of Information Security, 29 (3). https://doi.org/10.18372/2225-5036.29.18070
- Yevseiev, S., Milevskyi, S., Bortnik, L., Voropay, A., Bondarenko, K., Pohasii, S. (2022). Socio-Cyber-Physical Systems Security Concept. 2022 International Congress on Human-Computer Interaction, Optimization and Robotic Applications (HORA). https://doi.org/10.1109/hora55278.2022.9799957
- Yevseiev, S., Ryabukha, Y., Milov, O., Milevskyi, S., Pohasii, S., Melenti, Y. et al. (2021). Development of a method for assessing forecast of social impact in regional communities. Eastern-European Journal of Enterprise Technologies, 6 (2 (114)), 30–43. https://doi.org/10.15587/1729-4061.2021.249313
- Yevseiev, S., Pohasii, S., Milevskyi, S., Milov, O., Melenti, Y., Grod, I. et al. (2021). Development of a method for assessing the security of cyber-physical systems based on the Lotka–Volterra model. Eastern-European Journal of Enterprise Technologies, 5 (9 (113)), 30–47. https://doi.org/10.15587/1729-4061.2021.241638
- Ranjitha, C. R., Thomas, J., Chithra, K. R. (2016). A brief study on LDPC codes. International Journal of Engineering Research and General Science, 4, (2), 612–618. Available at: http://pnrsolution.org/Datacenter/Vol4/Issue2/85.pdf
- Broul´ım, J. (2018). LDPC codes - new methodologies. University of West Bohemia, 127. Available at: https://cds.cern.ch/record/2730008/files/CERN-THESIS-2018-479.pdf
- Zhu, H., Pu, L., Xu, H., Zhang, B. (2018). Construction of Quasi-Cyclic LDPC Codes Based on Fundamental Theorem of Arithmetic. Wireless Communications and Mobile Computing, 2018, 1–9. https://doi.org/10.1155/2018/5264724
- Singh, H. (2020). Code based Cryptography: Classic McEliece. arXiv.org. https://doi.org/10.48550/arXiv.1907.12754
- Otmani, A., Tillich, J.-P., Dallot, L. (2010). Cryptanalysis of Two McEliece Cryptosystems Based on Quasi-Cyclic Codes. Mathematics in Computer Science, 3 (2), 129–140. https://doi.org/10.1007/s11786-009-0015-8
- Liva, G., Song, S., Lan, L., Zhang, Y., Lin, S., Ryan, W. E. (2017). Design of LDPC Codes: A Survey and New Results. Journal of Communications Software and Systems, 2 (3), 191. https://doi.org/10.24138/jcomss.v2i3.283
- Richardson, T. J., Urbanke, R. L. (2001). Efficient encoding of low-density parity-check codes. IEEE Transactions on Information Theory, 47 (2), 638–656. https://doi.org/10.1109/18.910579
- Chandrasetty, V. A., Aziz, S. M. (2011). FPGA Implementation of a LDPC Decoder using a Reduced Complexity Message Passing Algorithm. Journal of Networks, 6 (1). https://doi.org/10.4304/jnw.6.1.36-45
- Wang, Y. (2008). Generalized constructions, decoding and implementation of LDPC codes. University of Hawaii at Manoa.
- Rukhin, A., Sota, J., Nechvatal, J., Smid, M., Barker, E., Leigh, S. et al. (2000). A statistical test suite for random and pseudorandom number generators for cryptographic applications. National Institute of Standards and Technology. https://doi.org/10.6028/nist.sp.800-22
- Milevsky, S. (2023). Sociocyberphysical systems’ security models. Ukrainian Information Security Research Journal, 25 (4). https://doi.org/10.18372/2410-7840.25.18224
Downloads
Published
How to Cite
Issue
Section
License
Copyright (c) 2024 Stanislav Milevskyi, Olha Korol, Galyna Mykytyn, Iryna Lozova, Svetlana Solnyshkova, Iryna Husarova, Alla Hrebeniuk, Andrii Vlasov, Vladyslav Sukhoteplyi, Dmytro Balagura

This work is licensed under a Creative Commons Attribution 4.0 International License.
The consolidation and conditions for the transfer of copyright (identification of authorship) is carried out in the License Agreement. In particular, the authors reserve the right to the authorship of their manuscript and transfer the first publication of this work to the journal under the terms of the Creative Commons CC BY license. At the same time, they have the right to conclude on their own additional agreements concerning the non-exclusive distribution of the work in the form in which it was published by this journal, but provided that the link to the first publication of the article in this journal is preserved.
A license agreement is a document in which the author warrants that he/she owns all copyright for the work (manuscript, article, etc.).
The authors, signing the License Agreement with TECHNOLOGY CENTER PC, have all rights to the further use of their work, provided that they link to our edition in which the work was published.
According to the terms of the License Agreement, the Publisher TECHNOLOGY CENTER PC does not take away your copyrights and receives permission from the authors to use and dissemination of the publication through the world's scientific resources (own electronic resources, scientometric databases, repositories, libraries, etc.).
In the absence of a signed License Agreement or in the absence of this agreement of identifiers allowing to identify the identity of the author, the editors have no right to work with the manuscript.
It is important to remember that there is another type of agreement between authors and publishers – when copyright is transferred from the authors to the publisher. In this case, the authors lose ownership of their work and may not use it in any way.








