Development of a method for protecting information resources in a corporate network by segmenting traffic
DOI:
https://doi.org/10.15587/1729-4061.2024.313158Keywords:
cybersecurity, protection of information resources, security policy, semiotic model, socio-cyber-physical system, confidentiality, integrity, authenticity, intelligent analysis, traffic controlAbstract
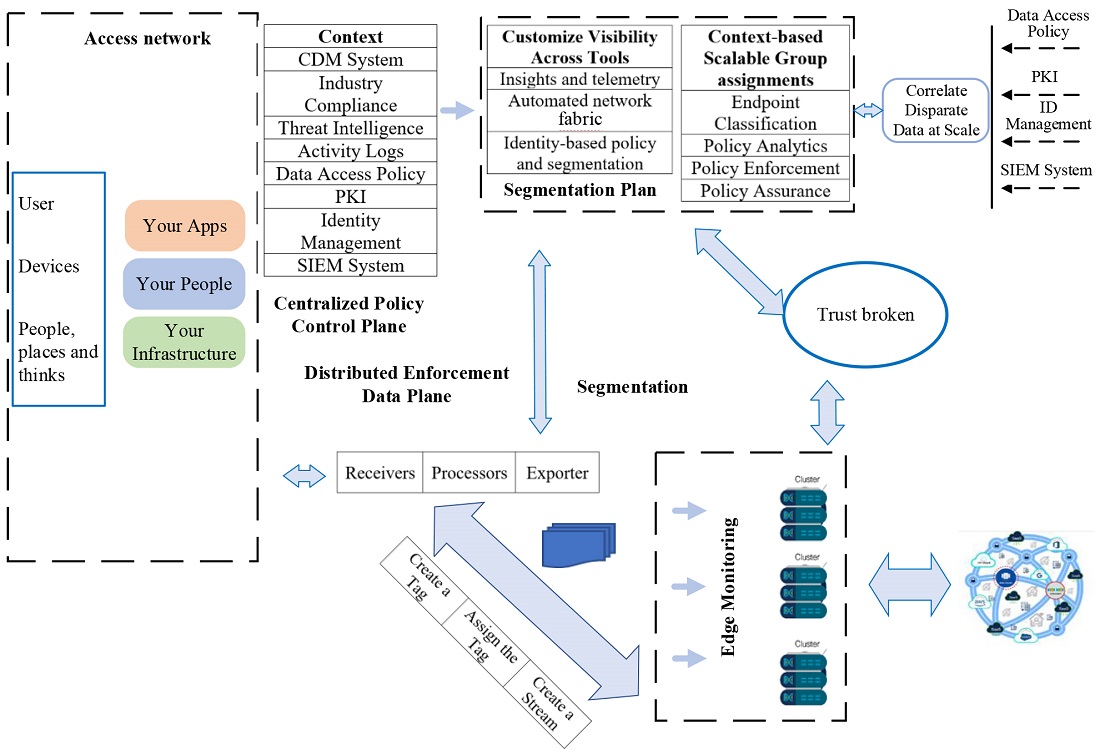
The object of the study is a corporate network with a dynamic structure and centralized management. The subject of the research is the processes of ensuring the protection of information resources in the corporate network. The goal is to develop a method of protecting information in the corporate network. The development is based on the Zero Trust Security strategy, according to which access to the network is allowed only after verification and identification of information. The task is to develop an effective method of protecting information resources and managing cyber security in the corporate network, taking into account the complex aspects of malicious influence. The following results were obtained. It is shown that the complex, diverse presentation of information in the network requires a comprehensive approach with the division of mixed content of information into segments according to the target orientation. Based on CISA's (Cybersecurity and Infrastructure Security Agency) Zero Trust Maturity Model, a method of targeted traffic segmentation is proposed. It allows detailed analysis of the interaction between applications, users and corporate network infrastructure, which increases the level of complex threats detection by 15 %. A method of protecting information resources of a socio-cyber-physical system is proposed, which, based on the principle of the Zero Trust Security strategy, improves the monitoring and management of cyber security of information resources by taking into account social aspects. This allows to detect and respond to threats in real time and adapt security policies according to the dynamics of user behavior and general security conditions. Integrating analytical methods and modern technologies into a security strategy creates a foundation for adaptive and resilient cyber defense.
References
- NIST Special Publication 800-207. Zero Trust Architecture (2020). U.S. Department of Commerce. National Institute of Standards and Technology Special Publication 800-207 Natl. Inst. Stand. Technol. Spec. Publ. 800-207, 59. Available at: https://doi.org/10.6028/NIST.SP.800-207
- Jammine, A., Serkov, A., Lazurenko, B., Nait-Abdesselam, F. (2023). The Order of Formation of Information Signals in IIoT. IJCSNS International Journal of Computer Science and Network Security, 23 (3), 139–143. https://doi.org/10.22937/IJCSNS.2023.23.3.14
- Standard ISO/IEC 27032:2023 (2023). Cybersecurity. Guidelines for Internet security. Available at: https://www.iso.org/obp/ui/#iso:std:iso-iec:27032:ed-2:v1:en
- Grusho, A. A., Grusho, N. A., Zabezhailo, M. I., Timonina, E. E. (2016). Intelligent data analysis in information security. Automatic Control and Computer Sciences, 50 (8), 722–725. https://doi.org/10.3103/s0146411616080307
- Miloslavskaya, N. (2020). Stream Data Analytics for Network Attacks’ Prediction. Procedia Computer Science, 169, 57–62. https://doi.org/10.1016/j.procs.2020.02.114
- Vasilyev, V., Vulfin, A., Kuchkarova, N. (2020). Automation of Software Vulnerabilities Analysis on the Basis of Text Mining Technology. Voprosy Kiberbezopasnosti, 4 (38), 22–31. https://doi.org/10.21681/2311-3456-2020-04-22-31
- Fatkieva, R. R., Levonevskiy, D. K. (2015). Application of Binary Trees for the IDS Events Aggregation Task. SPIIRAS Proceedings, 3 (40), 110–121. https://doi.org/10.15622/sp.40.8
- Gonzalez Granadillo, G., El-Barbori, M., Debar, H. (2016). New Types of Alert Correlation for Security Information and Event Management Systems. 2016 8th IFIP International Conference on New Technologies, Mobility and Security (NTMS). Larnaca, 1–7. https://doi.org/10.1109/ntms.2016.7792462
- Nevliudov, I., Yevsieiev, V., Maksymova, S., Filippenko, I. (2020). Development of an architectural-logical model to automate the management of the process of creating complex cyber-physical industrial systems. Eastern-European Journal of Enterprise Technologies, 4 (3 (106)), 44–52. https://doi.org/10.15587/1729-4061.2020.210761
- Embracing a Zero Trust Security Model (2021). NSA. Available at: https://media.defense.gov/2021/Feb/25/2002588479/-1/-1/0/CSI_EMBRACING_ZT_SECURITY_MODEL_UOO115131-21.PDF
- Evans, M., Maglaras, L. A., He, Y., Janicke, H. (2016). Human behaviour as an aspect of cybersecurity assurance. Security and Communication Networks, 9 (17), 4667–4679. https://doi.org/10.1002/sec.1657
- Security and privacy controls for federal information systems and organizations (2022). U.S. Department of Commerce, Washington, D.C. NIST Special Publication 800-53, Rev 4. Available at: http://dx.doi.org/10.6028/NIST.SP.800-53r4
- Dzheniuk, N., Yevseiev, S., Lazurenko, B., Serkov, O., Kasilov, O. (2023). A method of protecting information in cyber-physical space. Advanced Information Systems, 7 (4), 80–85. https://doi.org/10.20998/2522-9052.2023.4.11
- Chen, Y., Zhang, Y., Wang, Z., Wei, T. (2017). Downgrade Attack on TrustZone. https://doi.org/10.48550/arXiv.1707.05082
- Pohasii, S., Milevskyi, S., Tomashevsky, B., Voropay, N. (2022). Development of the double-contour protection concept in socio-cyberphysical systems. Advanced Information Systems, 6 (2), 57–66. https://doi.org/10.20998/2522-9052.2022.2.10
- Zhang, M., Wang, L., Jajodia, S., Singhal, A. (2021). Network Attack Surface: Lifting the Concept of Attack Surface to the Network Level for Evaluating Networks’ Resilience Against Zero-Day Attacks. IEEE Transactions on Dependable and Secure Computing, 18 (1), 310–324. https://doi.org/10.1109/tdsc.2018.2889086
- NIST AI 100-1 Artificial Intelligence Risk Management Framework (AI RMF 1.0) (2023). National Institute of Standards and Technology. https://doi.org/10.6028/NIST.AI.100-1
- Zakharzhevskyy, A. G., Tolkachov, M. Yu., Dzhenyuk, N. V., Pogasii, S. S., Glukhov, S. I. (2024). The method of protecting information resources based on the semiotic model of cyberspace. Modern Information Security, 57 (1), 57–68. https://doi.org/10.31673/2409-7292.2024.010007
- Canadian Institute for Cybersecurity (CIC) project funded by Canadian Internet Registration Authority (CIRA). Available at: https://www.unb.ca/cic/datasets/dohbrw-2020.html
- Susto, G. A., Cenedese, A., Terzi, M. (2018). Time-Series Classification Methods: Review and Applications to Power Systems Data. Big Data Application in Power Systems, 179–220. https://doi.org/10.1016/b978-0-12-811968-6.00009-7
- Vu, L., Pavuluri, V. N., Chang, Y., Turaga, D. S., Zhong, A., Agrawal, P. et al. (2018). A Large-Scale System for Real-Time Glucose Monitoring. 2018 48th Annual IEEE/IFIP International Conference on Dependable Systems and Networks Workshops (DSN-W), 3, 34–37. https://doi.org/10.1109/dsn-w.2018.00020
- Yevseiev, S., Tolkachov, M., Shetty, D., Khvostenko, V., Strelnikova, A., Milevskyi, S., Golovashych, S. (2023). The concept of building security of the network with elements of the semiotic approach. ScienceRise, 1, 24–34. https://doi.org/10.21303/2313-8416.2023.002828
Downloads
Published
How to Cite
Issue
Section
License
Copyright (c) 2024 Maksym Tolkachov, Nataliia Dzheniuk, Serhii Yevseiev, Yurii Lysetskyi, Volodymyr Shulha, Ivan Grod, Serhii Faraon, Ihor Ivanchenko, Igor Pasko, Dmytro Balagura

This work is licensed under a Creative Commons Attribution 4.0 International License.
The consolidation and conditions for the transfer of copyright (identification of authorship) is carried out in the License Agreement. In particular, the authors reserve the right to the authorship of their manuscript and transfer the first publication of this work to the journal under the terms of the Creative Commons CC BY license. At the same time, they have the right to conclude on their own additional agreements concerning the non-exclusive distribution of the work in the form in which it was published by this journal, but provided that the link to the first publication of the article in this journal is preserved.
A license agreement is a document in which the author warrants that he/she owns all copyright for the work (manuscript, article, etc.).
The authors, signing the License Agreement with TECHNOLOGY CENTER PC, have all rights to the further use of their work, provided that they link to our edition in which the work was published.
According to the terms of the License Agreement, the Publisher TECHNOLOGY CENTER PC does not take away your copyrights and receives permission from the authors to use and dissemination of the publication through the world's scientific resources (own electronic resources, scientometric databases, repositories, libraries, etc.).
In the absence of a signed License Agreement or in the absence of this agreement of identifiers allowing to identify the identity of the author, the editors have no right to work with the manuscript.
It is important to remember that there is another type of agreement between authors and publishers – when copyright is transferred from the authors to the publisher. In this case, the authors lose ownership of their work and may not use it in any way.








