Design of an integrated defense-in-depth system with an artificial intelligence assistant to counter malware
DOI:
https://doi.org/10.15587/1729-4061.2024.318336Keywords:
advanced persistent threat, intrusion detection systems, machine learning, anomaly detection, large language modelsAbstract
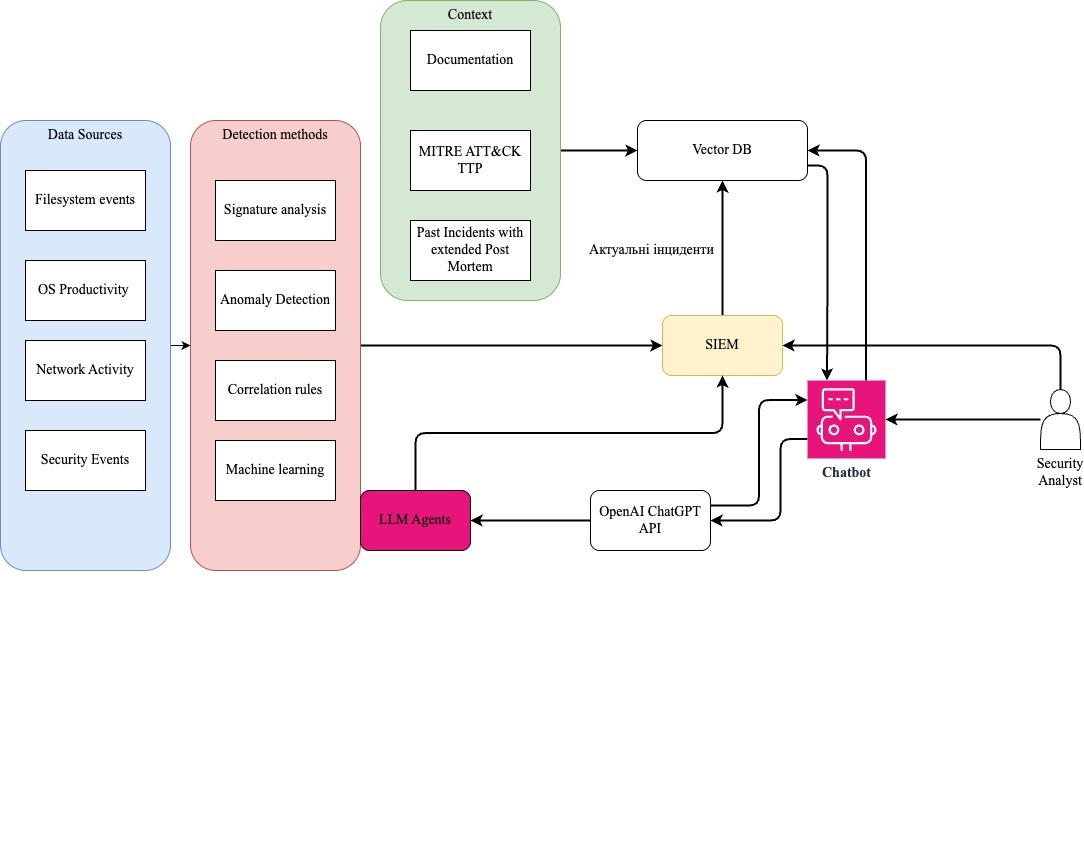
The object of this study is multi-layered cybersecurity systems for detecting and countering advanced persistent threats through the integration of machine learning technologies, artificial intelligence, and multi-layered security systems. The task relates to the need to design adaptive detection systems capable of effectively responding to new and modified threats while improving accuracy and minimizing delays. An integrated approach was devised in the study, which combines conventional detection methods (signature analysis, correlation rules) with modern technologies such as machine learning and Artificial Intelligence assistants. Each layer of the system showed varying levels of effectiveness: for example, antivirus solutions were most effective at detecting known threats but failed to cope with modified threats, which were detected by correlation rules. Machine learning proved most effective at detecting fileless attacks and anomalous activity that other tools could not detect. It is through the combination of these methods that the detection system proved to be effective, providing a high level of protection. The results are due to the efficiency of combining several layers of defense, in which each subsequent layer compensates for the shortcomings of the previous one. Antivirus solutions detected 100 % of known threats, while correlation rules identified all modified malicious files. Overall, the system was able to detect 98 % of malicious files and 99 % of tactics, techniques, and procedures used in advanced persistent threats attacks. A unique feature of the research is the integration of the Artificial Intelligence assistant, which automates threat analysis processes and speeds up response times by leveraging historical data and the context of past incidents. This reduces the workload on cybersecurity specialists and improves the overall effectiveness of the detection system, allowing for the quick identification of new threats and a reduction in false positives. Practical application of the results is possible in various critical sectors, including financial institutions, government organizations, and energy companies. The system demonstrates high flexibility and scalability, making it possible to easily adapt to different infrastructures and types of threats
References
- The swiss cheese model of security and why its important to have multiple layers of security. Firm Guardian. Available at: https://www.firmguardian.com/blog/swiss-cheese-model
- McKee, F., Noever, D. (2023). Chatbots in a Botnet World. International Journal on Cybernetics & Informatics, 12 (2), 77–95. https://doi.org/10.5121/ijci.2023.120207
- Ruby, A. R., Banu, A., Priya, S., Chandran, S. (2023). Taxonomy of AISecOps Threat Modeling for Cloud Based Medical Chatbots. arXiv. https://doi.org/10.48550/arXiv.2305.11189
- Third-Party Cybersecurity Risk Management: A Short Guide for 2024. Available at: https://flare.io/learn/resources/blog/third-party-cybersecurity-risk-management/
- Hassannataj Joloudari, J., Haderbadi, M., Mashmool, A., Ghasemigol, M., Band, S. S., Mosavi, A. (2020). Early Detection of the Advanced Persistent Threat Attack Using Performance Analysis of Deep Learning. IEEE Access, 8, 186125–186137. https://doi.org/10.1109/access.2020.3029202
- Li, S., Dong, F., Xiao, X., Wang, H., Shao, F., Chen, J. et al. (2024). NODLINK: An Online System for Fine-Grained APT Attack Detection and Investigation. Proceedings 2024 Network and Distributed System Security Symposium. https://doi.org/10.14722/ndss.2024.23204
- Wang, N., Wen, X., Zhang, D., Zhao, X., Ma, J., Luo, M. et al. (2023). TBDetector:Transformer-Based Detector for Advanced Persistent Threats with Provenance Graph. arXiv. https://doi.org/10.48550/arXiv.2304.02838
- Chen, Z., Liu, J., Shen, Y., Simsek, M., Kantarci, B., Mouftah, H. T., Djukic, P. (2022). Machine Learning-Enabled IoT Security: Open Issues and Challenges Under Advanced Persistent Threats. ACM Computing Surveys, 55 (5), 1–37. https://doi.org/10.1145/3530812
- Pham, V.-H., Nghi Hoang, K., Duy, P. T., Ngo Duc Hoang, S., Huynh Thai, T. (2024). Xfedhunter: An Explainable Federated Learning Framework for Advanced Persistent Threat Detection in Sdn. https://doi.org/10.2139/ssrn.4883207
- Zhang, R., Sun, W., Liu, J.-Y. (2020). Construction of two statistical anomaly features for small-sample APT attack traffic classification. arXiv. http://dx.doi.org/10.48550/arXiv.2010.13978
- Jia, B., Tian, Y., Zhao, D., Wang, X., Li, C., Niu, W. et al. (2021). Bidirectional RNN-Based Few-Shot Training for Detecting Multi-stage Attack. Information Security and Cryptology, 37–52. https://doi.org/10.1007/978-3-030-71852-7_3
- Getting Started with Windows Security and Windows Defender. Institute for Advanced Study. Available at: https://www.ias.edu/security/getting-started-with-windows-security-windows-defender
- Downloads. Available at: https://www.snort.org/downloads
- About data models. Splunk. Available at: https://docs.splunk.com/Documentation/Splunk/latest/Knowledge/Aboutdatamodels
- VMware Workstation Pro: Now Available Free for Personal Use. VMware Workstation Zealot. Available at: https://blogs.vmware.com/workstation/2024/05/vmware-workstation-pro-now-available-free-for-personal-use.html
- Redcanaryco/atomic-red-team. Small and highly portable detection tests based on MITRE's ATT&CK. GitHub. Available at: https://github.com/redcanaryco/atomic-red-team
- Piskozub, A., Zhuravchak, D., Tolkachova, A. (2023). Researching vulnerabilities in chatbots with LLM (large language model). Ukrainian Scientific Journal of Information Security, 29 (3), 111–117. https://doi.org/10.18372/2225-5036.29.18069
- Sysmon v15.15. Available at: https://learn.microsoft.com/en-us/sysinternals/downloads/sysmon
Downloads
Published
How to Cite
Issue
Section
License
Copyright (c) 2024 Danyil Zhuravchak, Maksym Opanovych, Anastasiia Tolkachova, Valerii Dudykevych, Andrian Piskozub

This work is licensed under a Creative Commons Attribution 4.0 International License.
The consolidation and conditions for the transfer of copyright (identification of authorship) is carried out in the License Agreement. In particular, the authors reserve the right to the authorship of their manuscript and transfer the first publication of this work to the journal under the terms of the Creative Commons CC BY license. At the same time, they have the right to conclude on their own additional agreements concerning the non-exclusive distribution of the work in the form in which it was published by this journal, but provided that the link to the first publication of the article in this journal is preserved.
A license agreement is a document in which the author warrants that he/she owns all copyright for the work (manuscript, article, etc.).
The authors, signing the License Agreement with TECHNOLOGY CENTER PC, have all rights to the further use of their work, provided that they link to our edition in which the work was published.
According to the terms of the License Agreement, the Publisher TECHNOLOGY CENTER PC does not take away your copyrights and receives permission from the authors to use and dissemination of the publication through the world's scientific resources (own electronic resources, scientometric databases, repositories, libraries, etc.).
In the absence of a signed License Agreement or in the absence of this agreement of identifiers allowing to identify the identity of the author, the editors have no right to work with the manuscript.
It is important to remember that there is another type of agreement between authors and publishers – when copyright is transferred from the authors to the publisher. In this case, the authors lose ownership of their work and may not use it in any way.








