Development of a method for automatic control of monitoring means for information protection objects
DOI:
https://doi.org/10.15587/1729-4061.2024.319058Keywords:
information protection, automatic control of monitoring tools, monitoring of information protection objectsAbstract
For the modern stage of science and technology development, the problem of information protection from unauthorized access is becoming relevant. The object of research is the process of monitoring information protection objects for timely detection and securing of leakage channels. The subject of research is ensuring automatic control of monitoring means for information protection objects.
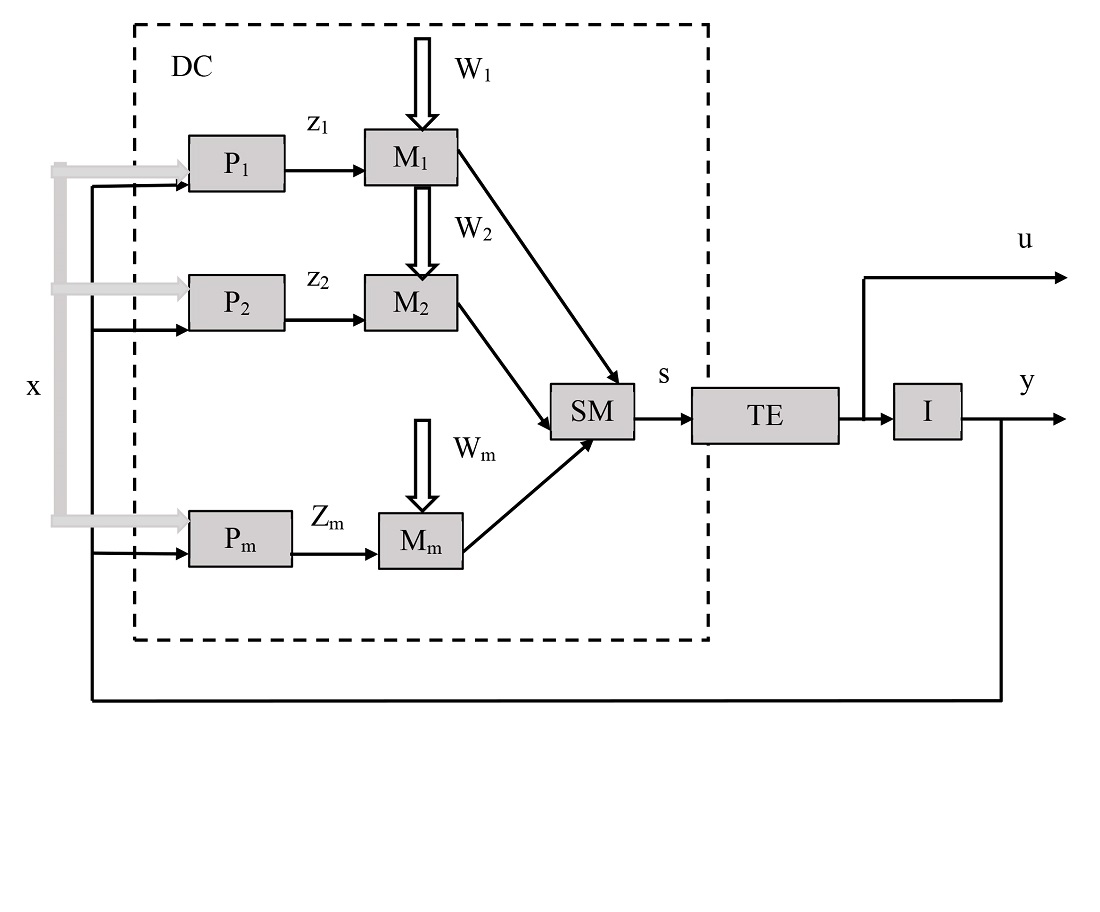
The article presents the results of the development of a method for automatic control of information protection object monitoring means by improving the control process, taking into account the peculiarities of the potential threats impact. The advantage of this study is the involvement of artificial intelligence in monitoring information protection objects in order to timely detect new threats to leakage channels. The essence of the method is to use a cybernetic approach to the development of adaptive control systems for monitoring information protection objects. The structure of the modeling method is considered, the procedure for assessing the adequacy and accuracy of determining the parameters of monitoring information protection objects. Proposals for implementing a method for controlling information protection object monitoring means based on associative control devices are substantiated. Schemes for implementing an associative control device for determining the parameters of an information protection object are presented, and the results of the practical implementation of the proposed method are also presented. A feature of the study are the developed associative control devices that provide the accumulation of knowledge in the process of learning about the threats of information leakage to the object of protection. The results of the study allow to improve the quality of detecting threats of information leakage to the object of protection and take into account possible changes in the characteristics of promising information leakage channels
References
- Yevseiev, S., Hryshchuk, R., Molodetska, K., Nazarkevych, M., Hrytsyk, V., Milov, O. et al.; Yevseiev, S., Hryshchuk, R., Molodetska, K., Nazarkevych, M. (Eds.) (2022). Modeling of security systems for critical infrastructure facilities. Kharkiv: РС ТЕСHNOLOGY СЕNTЕR, 196. https://doi.org/10.15587/978-617-7319-57-2
- Balitskyi, N., Іvanyk, E., Bolkot, P., Ilkiv, I., Smychok, V., Vankevych, P. (2022). Adaptation of extreme planning methodology to optimize the functioning of training simulators for personnel of the army land divisions. The scientific heritage, 1 (83 (83)), 29–32. https://doi.org/10.33577/2312-4458.23.2020.79-85
- Shmatko, O., Herasymov, S., Lysetskyi, Y., Yevseiev, S., Sievierinov, О., Voitko, T. et al. (2023). Development of the automated decision-making system synthesis method in the management of information security channels. Eastern-European Journal of Enterprise Technologies, 6 (9 (126)), 39–49. https://doi.org/10.15587/1729-4061.2023.293511
- Kоshevoy, N. D., Kostenko, E. M., Pavlyk, A. V., Koshevaya, I. I., Rozhnova, T. G. (2019). Research of multiple plans in multi-factor experiments with a minimum number of transitions of levels of factors. Radio Electronics, Computer Science, Control, 2, 53–59. https://doi.org/10.15588/1607-3274-2019-2-6
- Prabu, A. V., Kumar, G. S., Rajasoundaran, S., Malla, P. P., Routray, S., Mukherjee, A. (2021). Internet of things‐based deeply proficient monitoring and protection system for crop field. Expert Systems, 39 (5). https://doi.org/10.1111/exsy.12876
- Khudyntsev, M., Lebid, O., Bychenok, M., Zhylin, A., Davydiuk, A. (2023). Network Monitoring Index in the Information Security Management System of Critical Information Infrastructure Objects. Information and Communication Technologies and Sustainable Development, 270–290. https://doi.org/10.1007/978-3-031-46880-3_17
- Li, Z., Lin, Q., Wu, Y.-C., Ng, D. W. K., Nallanathan, A. (2024). Enhancing Physical Layer Security With RIS Under Multi-Antenna Eavesdroppers and Spatially Correlated Channel Uncertainties. IEEE Transactions on Communications, 72 (3), 1532–1547. https://doi.org/10.1109/tcomm.2023.3333919
- Mizuno, T., Nishikawa, H., Kong, X., Tomiyama, H. (2023). Empirical analysis of power side-channel leakage of high-level synthesis designed AES circuits. International Journal of Reconfigurable and Embedded Systems (IJRES), 12 (3), 305. https://doi.org/10.11591/ijres.v12.i3.pp305-319
- Sun, Q., Liu, X., Sun, Y., Wang, M., Han, X., Chen, X. (2021). A Security Wireless Monitoring and Automatic Protection System for CCEL. Wireless Communications and Mobile Computing, 2021 (1). https://doi.org/10.1155/2021/6652246
- Qiu, X., Yu, J., Zhuang, W., Li, G., Sun, X. (2023). Channel Prediction-Based Security Authentication for Artificial Intelligence of Things. Sensors, 23 (15), 6711. https://doi.org/10.3390/s23156711
- Marumoto, K., Suzuki, N., Shibata, Y., Takeuchi, A., Takami, A., Yamakawa, A. et al. (2024). Comparison between a manual monitoring method based on active sampling and an automatic active monitoring method at urban and rural sites: Toward the accumulation of comparable data for effectiveness evaluation of the Minamata Convention. Environmental Monitoring and Contaminants Research, 4, 55–68. https://doi.org/10.5985/emcr.20230015
- Culbreth, S., Graham, S. (2023). Demonstrating Redundancy Advantages of a Three-Channel Communication Protocol. International Conference on Cyber Warfare and Security, 18 (1), 513–522. https://doi.org/10.34190/iccws.18.1.964
- Ramos Luna, J. P., Ibarra Villegas, F. J., Pérez Wences, C. (2024). Automatic method for collecting and monitoring fault codes in industrial processes guided by PLCs. Revista de Ciencias Tecnológicas, 7 (3), e361. https://doi.org/10.37636/recit.v7n3e361
- Marabissi, D., Abrardo, A., Mucchi, L. (2023). A new framework for Physical Layer Security in HetNets based on Radio Resource Allocation and Reinforcement Learning. Mobile Networks and Applications, 28 (4), 1473–1481. https://doi.org/10.1007/s11036-023-02149-z
- Díaz, Á., Kaschel, H. (2023). Scalable Electronic Health Record Management System Using a Dual-Channel Blockchain Hyperledger Fabric. Systems, 11 (7), 346. https://doi.org/10.3390/systems11070346
- Wang, L., Zhang, X., Bai, C., Xie, H., Li, J., Ge, J. et al. (2024). Rapid automatic multiple moving objects detection method based on feature extraction from images with non-sidereal tracking. Monthly Notices of the Royal Astronomical Society, 534 (1), 385–399. https://doi.org/10.1093/mnras/stae2073
- Fedushko, S., Molodetska, K., Syerov, Y. (2023). Analytical method to improve the decision-making criteria approach in managing digital social channels. Heliyon, 9 (6), e16828. https://doi.org/10.1016/j.heliyon.2023.e16828
- Herasymov, S., Tkachov, A., Bazarnyi, S. (2024). Complex method of determining the location of social network agents in the interests of information operations. Advanced Information Systems, 8 (1), 31–36. https://doi.org/10.20998/2522-9052.2024.1.04
- Wen, Y., Wang, M., Wang, G., Ariyachandra, M., Brilakis, I., Xiao, L. (2024). An Integrated Solution for Automatic 3D Object-based Information Retrieval. Apollo - University of Cambridge Repository. https://doi.org/10.17863/CAM.107961
- Huang, R. (2024). Protection of Personal Information of Workers under Algorithmic Monitoring. Communications in Humanities Research, 33 (1), 198–204. https://doi.org/10.54254/2753-7064/33/20240094
- Mookerjee, R., Samuel, J. (2023). Managing the security of information systems with partially observable vulnerability. Production and Operations Management, 32 (9), 2902–2920. https://doi.org/10.1111/poms.14015
- Nguyen, T. B. D., Le, V. H., Tran, D. C. (2023). Safety Warnings for Technical Status of Port Structure by Automatic Monitoring in Vietnam. Proceedings of the 4th International Conference on Sustainability in Civil Engineering, 665–672. https://doi.org/10.1007/978-981-99-2345-8_68
- Abba, S., Bizi, A. M., Lee, J.-A., Bakouri, S., Crespo, M. L. (2024). Real-time object detection, tracking, and monitoring framework for security surveillance systems. Heliyon, 10 (15), e34922. https://doi.org/10.1016/j.heliyon.2024.e34922
- Yevseiev, S., Kuznietsov, O., Herasimov, S., Horielyshev, S., Karlov, A., Kovalov, I. et al. (2021). Development of an optimization method for measuring the Doppler frequency of a packet taking into account the fluctuations of the initial phases of its radio pulses. Eastern-European Journal of Enterprise Technologies, 2 (9 (110)), 6–15. https://doi.org/10.15587/1729-4061.2021.229221
- Yevseiev, S., Ponomarenko, V., Laptiev, O., Milov, O., Korol, O., Milevskyi, S. et al.; Yevseiev, S., Ponomarenko, V., Laptiev, O., Milov, O. (Eds.) (2021). Synergy of building cybersecurity systems. Kharkiv: РС ТЕСHNOLOGY СЕNTЕR, 188. https://doi.org/10.15587/978-617-7319-31-2
- Derevickiy, D. P., Fradkov, A. L. (1981). Prikladnaya teoriya diskretnyh adaptivnyh sistem upravleniya. Moscow: Nauka, 215.
- Yevseiev, S., Milevskyi, S., Sokol, V., Yemanov, V., Volobuiev, A., Dakova, L. et al. (2024). Development of functionality principles for the automated data transmission system through wireless communication channels to ensure information protection. Information and Controlling System, 4 (9 (130)), 18–33. https://doi.org/10.15587/1729-4061.2024.310547
Downloads
Published
How to Cite
Issue
Section
License
Copyright (c) 2024 Serhii Herasymov, Serhii Yevseiev, Stanislav Milevskyi, Nazar Balitskyi, Viktor Zaika, Serhii Povaliaiev, Sergii Golovashych, Oleksandr Huk, Anton Smirnov, Kostiantyn Rubel

This work is licensed under a Creative Commons Attribution 4.0 International License.
The consolidation and conditions for the transfer of copyright (identification of authorship) is carried out in the License Agreement. In particular, the authors reserve the right to the authorship of their manuscript and transfer the first publication of this work to the journal under the terms of the Creative Commons CC BY license. At the same time, they have the right to conclude on their own additional agreements concerning the non-exclusive distribution of the work in the form in which it was published by this journal, but provided that the link to the first publication of the article in this journal is preserved.
A license agreement is a document in which the author warrants that he/she owns all copyright for the work (manuscript, article, etc.).
The authors, signing the License Agreement with TECHNOLOGY CENTER PC, have all rights to the further use of their work, provided that they link to our edition in which the work was published.
According to the terms of the License Agreement, the Publisher TECHNOLOGY CENTER PC does not take away your copyrights and receives permission from the authors to use and dissemination of the publication through the world's scientific resources (own electronic resources, scientometric databases, repositories, libraries, etc.).
In the absence of a signed License Agreement or in the absence of this agreement of identifiers allowing to identify the identity of the author, the editors have no right to work with the manuscript.
It is important to remember that there is another type of agreement between authors and publishers – when copyright is transferred from the authors to the publisher. In this case, the authors lose ownership of their work and may not use it in any way.








