Improving the process of control and correction of errors in non-positional code structures
DOI:
https://doi.org/10.15587/1729-4061.2025.322427Keywords:
data processing speed, non-positional code structure, residue class system, control efficiency, data correctionAbstract
The object of this study is the processes of operational control and correction of data errors in non-positional code structures (NCS). Based on a critical analysis of the existing data control method based on the use of the projection of a number in RCS, limited control efficiency and the ability to detect only single errors have been established.
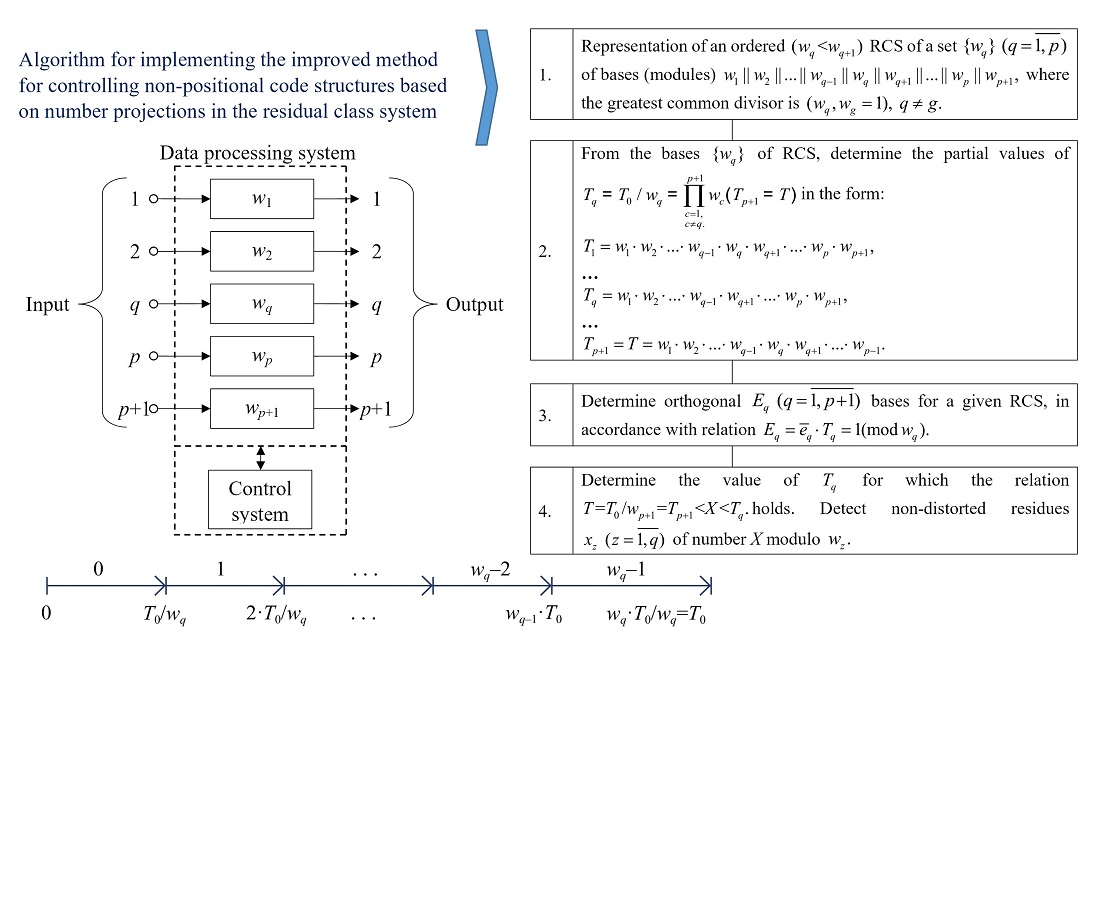
The study improves methods for rapid control and data correction of a real-time computer system (CS) operating in a non-positional number system, in the so-called residual class system (RCS). A comprehensive approach to control and eliminate errors in RCS is built on the basis of non-positional coding, underlying which is the Chinese residual theorem. This theorem proves that NSC is the next stage in the development of the theory of information control using arithmetic control by modulus. The use of the property of complete arithmetic of NSC has made it possible to improve the method and increase the efficiency of data control due to information processing in RCS without controlling each intermediate result obtained. Comparison with the most efficient existing method has made it possible to establish that the devised method provides an increase in the speed of data control by 1.2–1.3 times.
An effective process of operational and accurate error detection based on an improved method of data control in RCS, which is based on the use of the corrective properties of NCS, has been proposed. Parallel error correction in NCS increases the efficiency of error correction by 2 times, due to a decrease in the number of intermediate operations in the improved method. At the same time, with an increase in the bit grid of the operands being processed, the efficiency of the application of the considered error correction process improves
References
- Shyman, A., Kuchuk, N., Filatova, A., Bellorin-Herrera, O. (2024). Development of a method for assessing the adequacy of a computer system model based on petri nets. Advanced Information Systems, 8 (3), 46–52. https://doi.org/10.20998/2522-9052.2024.3.05
- Shvahirev, P., Lopakov, O., Kosmachevskiy, V., Salii, V. (2020). Method for assessing of reliability characteristics in designing of failureresistant real-time operating systems. Odes’kyi Politechnichnyi Universytet Pratsi, 2 (61), 108–118. https://doi.org/10.15276/opu.2.61.2020.13
- Krasnobayev, V., Yanko, A., Hlushko, A. (2023). Information Security of the National Economy Based on an Effective Data Control Method. Journal of International Commerce, Economics and Policy, 14 (03). https://doi.org/10.1142/s1793993323500217
- Kasianchuk, M. N., Nykolaychuk, Y. N., Yakymenko, I. Z. (2016). Theory and Methods of Constructing of Modules System of the Perfect Modified Form of the System of Residual Classes. Journal of Automation and Information Sciences, 48 (8), 56–63. https://doi.org/10.1615/jautomatinfscien.v48.i8.60
- Bahachuk, D., Hadzhyiev, M., Nazarenko, A., Odegov, N., Stepanov, D. (2023). Multiplex technique of data transmission in residual class systems. Eastern-European Journal of Enterprise Technologies, 6 (9 (126)), 23–31. https://doi.org/10.15587/1729-4061.2023.292504
- Safari, A., Nugent, J., Kong, Y. (2013). Novel implementation of full adder based scaling in Residue Number Systems. 2013 IEEE 56th International Midwest Symposium on Circuits and Systems (MWSCAS), 657–660. https://doi.org/10.1109/mwscas.2013.6674734
- Yanko, A., Krasnobayev, V., Kruk, O. (2024). A Method of Control and Operational Diagnostics of Data Errors Presented in a Non-positional Number System in Residual Classes. Proceedings of The Seventh International Workshop on Computer Modeling and Intelligent Systems (CMIS 2024). Zaporizhzhia, 389–399. Available at: https://ceur-ws.org/Vol-3702/paper32.pdf
- Onyshchenko, S., Yanko, A., Hlushko, A., Maslii, O., Cherviak, A. (2023). Cybersecurity and Improvement of the Information Security System. Journal of the Balkan Tribological Association, 29 (5), 818–835. Available at: https://scibulcom.net/en/article/L8nV7It2dVTBPX09mzWB
- Krylova, V., Tverytnykova, E., Vasylchenkov, O., Kolisnyk, T. (2022). Punctured NCC codes for information protection in information and measurement systems. Bulletin of the National Technical University «KhPI» Series: New Solutions in Modern Technologies, 1 (11), 38–43. https://doi.org/10.20998/2413-4295.2022.01.06
- Talib, H. A., Alothman, R. B., Mohammed, M. S. (2023). Malicious attacks modelling: a prevention approach for ad hoc network security. Indonesian Journal of Electrical Engineering and Computer Science, 30 (3), 1856. https://doi.org/10.11591/ijeecs.v30.i3.pp1856-1865
- Almomani, A. (2022). Classification of Virtual Private networks encrypted traffic using ensemble learning algorithms. Egyptian Informatics Journal, 23 (4), 57–68. https://doi.org/10.1016/j.eij.2022.06.006
- Lekan, S. H. (2024). An Improved DNA Cryptography Using Residue Number System. International Journal of Research and Innovation in Social Science, VIII (VI), 488–501. https://doi.org/10.47772/ijriss.2024.806037
- Noor, S. E. (2022). Learning the basics of cryptography with practical examples. ReiDoCrea: Revista Electrónica de Investigación Docencia Creativa, 11 (24). https://doi.org/10.30827/digibug.74740
- Rama Devi, K., Prabakaran, S. (2016). An Enhanced Bilateral Information Security towards a Conventional Cryptographic System using DNA Sequences. Indian Journal of Science and Technology, 9 (39). https://doi.org/10.17485/ijst/2016/v9i39/102067
- Boyko, Y., Pyatin, I. (2023). Features of code redundancy formation in information transmission channels. Infocommunication and computer technologies, 2 (04), 12–25. https://doi.org/10.36994/2788-5518-2022-02-04-01
- Upadhyaya, P., Yu, X., Mink, J., Cordero, J., Parmar, P., Jiang, A. (2019). Error correction for hardware-implemented deep neural networks. Texas A&M University. Available at: http://nvmw.ucsd.edu/nvmw2019-program/unzip/current/nvmw2019-final87.pdf
- Huang, K., Siegel, P. H., Jiang, A. (2020). Functional Error Correction for Robust Neural Networks. IEEE Journal on Selected Areas in Information Theory, 1 (1), 267–276. https://doi.org/10.1109/jsait.2020.2991430
- Agbedemnab, P. A., Baagyere, E. Y., Daabo, M. I. (2020). Single and Multiple Error Detection and Correction using Redundant Residue Number System for Cryptographic and Stenographic Schemes. Asian Journal of Research in Computer Science, 4 (4), 1–14. https://doi.org/10.9734/ajrcos/2019/v4i430123
- Xiao, H., Garg, H. K., Hu, J., Xiao, G. (2016). New Error Control Algorithms for Residue Number System Codes. ETRI Journal, 38 (2), 326–336. https://doi.org/10.4218/etrij.16.0115.0575
- Onyshchenko, S., Skryl, V., Hlushko, A., Maslii, O. (2023). Inclusive Development Index. Proceedings of the 4th International Conference on Building Innovations, 779–790. https://doi.org/10.1007/978-3-031-17385-1_66
- Shefer, O., Laktionov, O., Pents, V., Hlushko, A., Kuchuk, N. (2024). Practical principles of integrating artificial intelligence into the technology of regional security predicting. Advanced Information Systems, 8 (1), 86–93. https://doi.org/10.20998/2522-9052.2024.1.11
- Krasnobayev, V., Yanko, A., Martynenko, A., Kovalchuk, D. (2023). Method for computing exponentiation modulo the positive and negative integers. Proceedings of XI International Scientific and Practical Conference "Information Control Systems & Technologies (ICST-2023)". Odesa, 374–383. Available at: https://ceur-ws.org/Vol-3513/paper31.pdf
- Onyshchenko, S., Yanko, A., Hlushko, A. (2023). Improving the efficiency of diagnosing errors in computer devices for processing economic data functioning in the class of residuals. Eastern-European Journal of Enterprise Technologies, 5 (4 (125)), 63–73. https://doi.org/10.15587/1729-4061.2023.289185
- Krasnobayev, V., Kuznetsov, A., Yanko, A., Kuznetsova, T. (2020). The analysis of the methods of data diagnostic in a residue number system. Computer Modeling and Intelligent Systems, 2608, 594–609. https://doi.org/10.32782/cmis/2608-46
- Ananda Mohan, P. V. (2016). Error Detection, Correction and Fault Tolerance in RNS-Based Designs. Residue Number Systems, 163–175. https://doi.org/10.1007/978-3-319-41385-3_7
- Boutillon, E., Jego, C., Jezequel, M. (2010). A new single-error correction scheme based on self-diagnosis residue number arithmetic. 2010 Conference on Design and Architectures for Signal and Image Processing (DASIP), 27–33. https://doi.org/10.1109/dasip.2010.5706242
- McEliece, R. (2009). Coding theory. The Theory of Information and Coding. Encyclopedia of Mathematics and its Applications. Cambridge University Press, 137–138.
- Gregory, R. T., Krishnamurthy, E. V. (1984). Residue or Modular Arithmetic. Methods and Applications of Error-Free Computation, 1–62. https://doi.org/10.1007/978-1-4612-5242-9_1
- Dummermuth, E. (1998). Advanced diagnostic methods in process control. ISA Transactions, 37 (2), 79–85. https://doi.org/10.1016/s0019-0578(98)00012-3
- Krasnobayev, V., Yanko, A., Hlushko, A., Kruk, O., Kruk, O., Gakh, V. (2023). Cyberspace protection system based on the data comparison method. Economic and Cyber Security, 3–29. https://doi.org/10.15587/978-617-7319-98-5.ch1
Downloads
Published
How to Cite
Issue
Section
License
Copyright (c) 2025 Alina Yanko, Victor Krasnobayev, Alina Hlushko

This work is licensed under a Creative Commons Attribution 4.0 International License.
The consolidation and conditions for the transfer of copyright (identification of authorship) is carried out in the License Agreement. In particular, the authors reserve the right to the authorship of their manuscript and transfer the first publication of this work to the journal under the terms of the Creative Commons CC BY license. At the same time, they have the right to conclude on their own additional agreements concerning the non-exclusive distribution of the work in the form in which it was published by this journal, but provided that the link to the first publication of the article in this journal is preserved.
A license agreement is a document in which the author warrants that he/she owns all copyright for the work (manuscript, article, etc.).
The authors, signing the License Agreement with TECHNOLOGY CENTER PC, have all rights to the further use of their work, provided that they link to our edition in which the work was published.
According to the terms of the License Agreement, the Publisher TECHNOLOGY CENTER PC does not take away your copyrights and receives permission from the authors to use and dissemination of the publication through the world's scientific resources (own electronic resources, scientometric databases, repositories, libraries, etc.).
In the absence of a signed License Agreement or in the absence of this agreement of identifiers allowing to identify the identity of the author, the editors have no right to work with the manuscript.
It is important to remember that there is another type of agreement between authors and publishers – when copyright is transferred from the authors to the publisher. In this case, the authors lose ownership of their work and may not use it in any way.








