Розробка математичної моделі рекомендаційної системи в децентралізованих однорангових комп’ютерних мережах
DOI:
https://doi.org/10.15587/1729-4061.2023.286187Ключові слова:
рекомендаційна система, децентралізована комп’ютерна мережа, однорангова мережа, GERT-мережа, інформаційна безпекаАнотація
Рекомендаційні системи дозволяють полегшити пошук при великій кількості контенту, доповнюючи або заміняючи класичну пошукову видачу рекомендаціями. В P2P мережах їх застосування може мати додаткову користь. Через проблеми індексації і пошуку раніше додані файли можуть бути недоступні для користувача P2P мережі. Якщо користувач не може знайти шуканий файл, можна надати йому список рекомендацій з врахуванням його вподобань і пошукового запиту.
Об’єктом дослідження є процес створення рекомендацій користувачам децентралізованих P2P мереж для полегшення пошуку даних.
Вирішується актуальна проблема підвищення точності математичного моделювання рекомендаційних систем за рахунок врахування вимог до достовірності та безпеки даних під час змін у структурі децентралізованої P2P мережі.
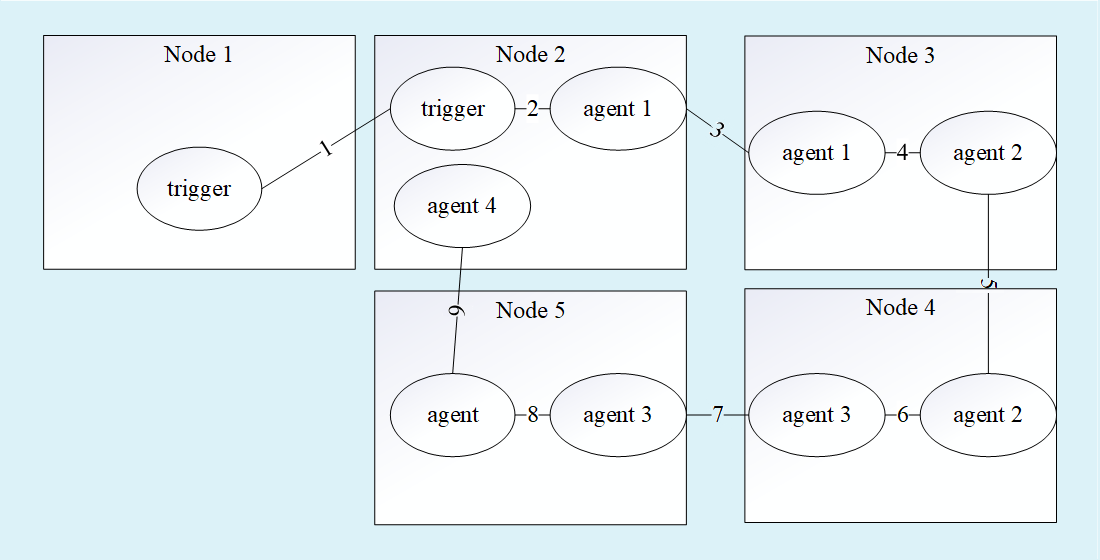
Розроблена аналітична модель рекомендаційної системи децентралізованої P2P мережі, основною особливістю якої є врахування вимог достовірності та безпеки рекомендаційних повідомлень. Це виконано шляхом введення в загальну модель децентралізованої рекомендаційної системи наступних показників – ймовірність достовірної передачі пакета та ймовірність безпечної передачі пакета. Розроблена аналітична модель дозволяє проводити порівняльний аналіз різних методів роботи рекомендаційних систем та встановлювати припустимі параметри, при яких ступінь актуальності не падає нижче визначеного порогу.
Розроблена математична модель системи на основі GERT-схеми відрізняється від відомих врахуванням вимог достовірності і безпеки під час змін у структурі децентралізованої P2P мережі. Це дозволило покращити точність результатів моделювання до 5 %.
Запропонована математична модель може бути використана для прототипування рекомендаційних систем у різних сферах діяльності
Посилання
- Fayyaz, Z., Ebrahimian, M., Nawara, D., Ibrahim, A., Kashef, R. (2020). Recommendation Systems: Algorithms, Challenges, Metrics, and Business Opportunities. Applied Sciences, 10 (21), 7748. doi: https://doi.org/10.3390/app10217748
- Falk, K. (2019). Practical recommender systems. Manning, 432.
- Roy, D., Dutta, M. (2022). A systematic review and research perspective on recommender systems. Journal of Big Data, 9 (1). doi: https://doi.org/10.1186/s40537-022-00592-5
- Fulber-Garcia, V. (2023). Centralized Computing vs. Distributed Computing. Baeldung. Available at: https://www.baeldung.com/cs/centralized-vs-distributed-computing
- Vergne, J. (2020). Decentralized vs. Distributed Organization: Blockchain, Machine Learning and the Future of the Digital Platform. Organization Theory, 1 (4), 263178772097705. doi: https://doi.org/10.1177/2631787720977052
- Kosalka, T. (2006). Decision making through the simulation of centralized and decentralized distribution storage systems. doi: https://doi.org/10.33915/etd.1709
- Gong, S., Ye, H., Su, P. (2009). A Peer-to-Peer Based Distributed Collaborative Filtering Architecture. 2009 International Joint Conference on Artificial Intelligence. doi: https://doi.org/10.1109/jcai.2009.154
- Karaarslan, E., Konacaklı, E. (2020). Data Storage in the Decentralized World: Blockchain and Derivatives. Who Runs the World: Data, 37–69. doi: https://doi.org/10.26650/b/et06.2020.011.03
- Si, M., Li, Q. (2018). Shilling attacks against collaborative recommender systems: a review. Artificial Intelligence Review, 53 (1), 291–319. doi: https://doi.org/10.1007/s10462-018-9655-x
- Meleshko, Y., Drieiev, O., Yakymenko, M., Lysytsia, D. (2020). Developing a model of the dynamics of states of a recommendation system under conditions of profile injection attacks. Eastern-European Journal of Enterprise Technologies, 4 (2 (106)), 14–24. doi: https://doi.org/10.15587/1729-4061.2020.209047
- Meleshko, Y. V., Yakymenko, M., Semenov, S. (2021). A Method of Detecting Bot Networks Based on Graph Clustering in the Recommendation System of Social Network. Computational Linguistics and Intelligent Systems, 2870. Available at: https://ceur-ws.org/Vol-2870/paper92.pdf
- The BitTorrent Protocol Specification (2017). Available at: http://www.bittorrent.org/beps/bep_0003.html
- Gnutella Protocol Development (2003). Available at: https://rfc-gnutella.sourceforge.net
- Kademlia: A Design Specification (2010). Available at: https://xlattice.sourceforge.net/components/protocol/kademlia/specs.html
- Stoica, I., Morris, R., Karger, D., Kaashoek, M. F., Balakrishnan, H. (2001). Chord. ACM SIGCOMM Computer Communication Review, 31 (4), 149–160. doi: https://doi.org/10.1145/964723.383071
- Zhang, S., Yin, H., Chen, T., Huang, Z., Nguyen, Q. V. H., Cui, L. (2022). PipAttack: Poisoning Federated Recommender Systems for Manipulating Item Promotion. Proceedings of the Fifteenth ACM International Conference on Web Search and Data Mining. doi: https://doi.org/10.1145/3488560.3498386
- Mohammed, A. S., Meleshko, Y., Balaji B, S., Serhii, S. (2019). Collaborative Filtering Method with the use of Production Rules. 2019 International Conference on Computational Intelligence and Knowledge Economy (ICCIKE). doi: https://doi.org/10.1109/iccike47802.2019.9004257
- Ko, H., Lee, S., Park, Y., Choi, A. (2022). A Survey of Recommendation Systems: Recommendation Models, Techniques, and Application Fields. Electronics, 11 (1), 141. doi: https://doi.org/10.3390/electronics11010141
- Naeen, H. M., Jalali, M. (2019). A decentralized trust-aware collaborative filtering recommender system based on weighted items for social tagging systems. arXiv. doi: https://doi.org/10.48550/arXiv.1906.05143
- Wang, Y., Han, S., Zhou, J., Chen, L., Chen, C. L. P., Zhang, T. et al. (2023). Random Feature-Based Collaborative Kernel Fuzzy Clustering for Distributed Peer-to-Peer Networks. IEEE Transactions on Fuzzy Systems, 31 (2), 692–706. doi: https://doi.org/10.1109/tfuzz.2022.3188363
- Wang, T., Wang, M. (2018). Distributed collaborative filtering recommendation algorithm based on DHT. Cluster Computing, 22 (S2), 2931–2941. doi: https://doi.org/10.1007/s10586-018-1699-9
- Zhao, Z., Wang, Y., Wang, H. (2021). SDN-based cross-domain cooperative method for trusted nodes recommendation in Mobile crowd sensing. Peer-to-Peer Networking and Applications, 14 (6), 3793–3805. doi: https://doi.org/10.1007/s12083-021-01217-z
- Lisi, A., De Salve, A., Mori, P., Ricci, L. (2019). A Smart Contract Based Recommender System. Lecture Notes in Computer Science, 29–42. doi: https://doi.org/10.1007/978-3-030-36027-6_3
- Bobadilla, D., Lipizzi, C. (2021). A Blockchain-Based Collaborative Filtering Recommendation System Based on Trust. 2021 18th International Computer Conference on Wavelet Active Media Technology and Information Processing (ICCWAMTIP). doi: https://doi.org/10.1109/iccwamtip53232.2021.9674128
- Badis, L., Amad, M., Aïssani, D., Abbar, S. (2021). P2PCF: A collaborative filtering based recommender system for peer to peer social networks. Journal of High Speed Networks, 27 (1), 13–31. doi: https://doi.org/10.3233/jhs-210649
- Yoo, H., Chung, K. (2017). Mining-based lifecare recommendation using peer-to-peer dataset and adaptive decision feedback. Peer-to-Peer Networking and Applications, 11 (6), 1309–1320. doi: https://doi.org/10.1007/s12083-017-0620-2
- Zeng, X., Yu, X. (2023). P2P based on network behavior analysis trust value calculation method. International Conference on Computer Network Security and Software Engineering (CNSSE 2023). doi: https://doi.org/10.1117/12.2683177
- Semenov, S., Zhang, L., Cao, W., Bulba, S., Babenko, V., Davydov, V. (2021). Development of a fuzzy GERT-model for investigating common software vulnerabilities. Eastern-European Journal of Enterprise Technologies, 6 (2 (114)), 6–18. doi: https://doi.org/10.15587/1729-4061.2021.243715
- Semenov, S., Liqiang, Z., Weiling, C., Davydov, V. (2021). Development a mathematical model for the software security testing first stage. Eastern-European Journal of Enterprise Technologies, 3 (2 (111)), 24–34. doi: https://doi.org/10.15587/1729-4061.2021.233417
- Netflix Prize data: Dataset from Netflix's competition to improve their reccommendation algorithm. Available at: https://www.kaggle.com/datasets/netflix-inc/netflix-prize-data?resource=download
##submission.downloads##
Опубліковано
Як цитувати
Номер
Розділ
Ліцензія
Авторське право (c) 2023 Volodymyr Mikhav, Serhii Semenov, Yelyzaveta Meleshko, Mykola Yakymenko, Yaroslav Shulika

Ця робота ліцензується відповідно до Creative Commons Attribution 4.0 International License.
Закріплення та умови передачі авторських прав (ідентифікація авторства) здійснюється у Ліцензійному договорі. Зокрема, автори залишають за собою право на авторство свого рукопису та передають журналу право першої публікації цієї роботи на умовах ліцензії Creative Commons CC BY. При цьому вони мають право укладати самостійно додаткові угоди, що стосуються неексклюзивного поширення роботи у тому вигляді, в якому вона була опублікована цим журналом, але за умови збереження посилання на першу публікацію статті в цьому журналі.
Ліцензійний договір – це документ, в якому автор гарантує, що володіє усіма авторськими правами на твір (рукопис, статтю, тощо).
Автори, підписуючи Ліцензійний договір з ПП «ТЕХНОЛОГІЧНИЙ ЦЕНТР», мають усі права на подальше використання свого твору за умови посилання на наше видання, в якому твір опублікований. Відповідно до умов Ліцензійного договору, Видавець ПП «ТЕХНОЛОГІЧНИЙ ЦЕНТР» не забирає ваші авторські права та отримує від авторів дозвіл на використання та розповсюдження публікації через світові наукові ресурси (власні електронні ресурси, наукометричні бази даних, репозитарії, бібліотеки тощо).
За відсутності підписаного Ліцензійного договору або за відсутністю вказаних в цьому договорі ідентифікаторів, що дають змогу ідентифікувати особу автора, редакція не має права працювати з рукописом.
Важливо пам’ятати, що існує і інший тип угоди між авторами та видавцями – коли авторські права передаються від авторів до видавця. В такому разі автори втрачають права власності на свій твір та не можуть його використовувати в будь-який спосіб.









