Створення системи виявлення мережевих вторгнень на основі згорткової нейронної мережі та двонаправленого вентильного рекурентного вузла з механізмом уваги
DOI:
https://doi.org/10.15587/1729-4061.2024.305685Ключові слова:
глибоке навчання, комбінована модель, системи виявлення мережевих вторгнень, механізм увагиАнотація
Об'єктом дослідження є процес розпізнавання вторгнень в комп’ютерних мережах. Системи виявлення мережевих вторгнень (NIDS) стали актуальною сферою досліджень, оскільки вони використовуються для захисту комп'ютерних систем від хакерських атак. Глибоке навчання стає все більш популярним для виявлення та класифікації шкідливого мережевого трафіку, в тому числі і для побудови NIDS.
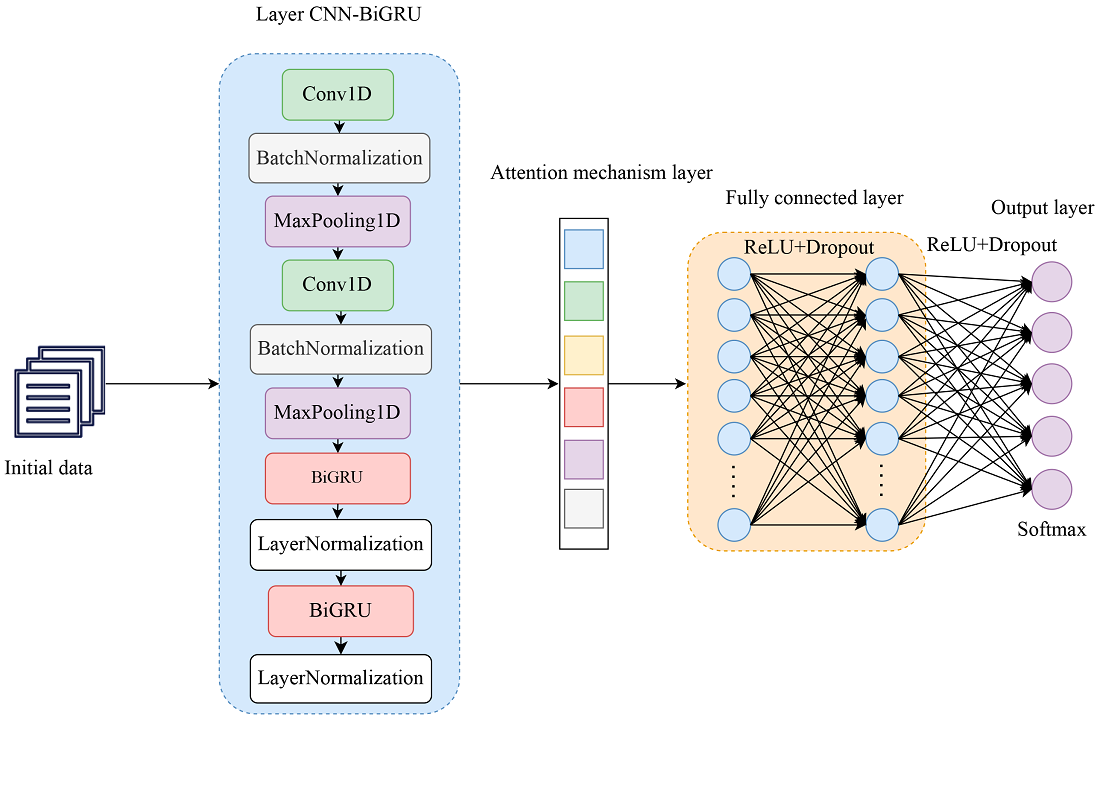
У роботі пропонується модель виявлення мережевих вторгнень CNN-BiGRU-Attention, що заснована на часовому підході до глибокого навчання з використанням механізму уваги. Головна ціль дослідження: побудувати ефективну комбіновану модель глибокого навчання, яка здатна виявляти різноманітні мережеві кіберзагрози.
Реалізовано 1D згорткову нейронну мережу для вилучення високорівневих представлень ознак інформації про вторгнення. Розроблено двонаправленний вентильний рекурентний вузол (BiGRU) з механізмом уваги для класифікації даних трафіку. Механізм уваги грає ключову роль у розробленій моделі, так як дозволяє системі зосередитися лише на важливих аспектах мережевого трафіку та дозволяє моделі адаптуватися до нових видів загроз.
Результати дослідження показують, що використання комбінації CNN та BiGRU з механізмом уваги прискорює та покращує процес класифікації атак на мережу. На тренувальних наборах даних NSL-KDD та UNSW-NB15 модель показує точність у 99.81 % та 97.80 %. На тестувальних наборах даних NSL-KDD та UNSW-NB15 модель показує точність у 82.16 % та 97.72 %.
Пропонована модель NIDS розглядатиметься для впровадження в систему захисту корпоративних мереж у режимі реального часу.
Загалом, результати дослідження дають новий погляд на покращення роботи NIDS і є доволі актуальними з точки зору використання механізмів уваги для класифікації мережевого трафіку
Посилання
- Boukhalfa, A., Abdellaoui, A., Hmina, N., Chaoui, H. (2020). LSTM deep learning method for network intrusion detection system. International Journal of Electrical and Computer Engineering (IJECE), 10 (3), 3315. https://doi.org/10.11591/ijece.v10i3.pp3315-3322
- Ahmad, Z., Shahid Khan, A., Wai Shiang, C., Abdullah, J., Ahmad, F. (2020). Network intrusion detection system: A systematic study of machine learning and deep learning approaches. Transactions on Emerging Telecommunications Technologies, 32 (1). https://doi.org/10.1002/ett.4150
- Kumar, S., Gupta, S., Arora, S. (2021). Research Trends in Network-Based Intrusion Detection Systems: A Review. IEEE Access, 9, 157761–157779. https://doi.org/10.1109/access.2021.3129775
- Aldweesh, A., Derhab, A., Emam, A. Z. (2020). Deep learning approaches for anomaly-based intrusion detection systems: A survey, taxonomy, and open issues. Knowledge-Based Systems, 189, 105124. https://doi.org/10.1016/j.knosys.2019.105124
- Thirimanne, S. P., Jayawardana, L., Yasakethu, L., Liyanaarachchi, P., Hewage, C. (2022). Deep Neural Network Based Real-Time Intrusion Detection System. SN Computer Science, 3 (2). https://doi.org/10.1007/s42979-022-01031-1
- Qazi, E. U. H., Almorjan, A., Zia, T. (2022). A One-Dimensional Convolutional Neural Network (1D-CNN) Based Deep Learning System for Network Intrusion Detection. Applied Sciences, 12 (16), 7986. https://doi.org/10.3390/app12167986
- Zhang, J., Ling, Y., Fu, X., Yang, X., Xiong, G., Zhang, R. (2020). Model of the intrusion detection system based on the integration of spatial-temporal features. Computers & Security, 89, 101681. https://doi.org/10.1016/j.cose.2019.101681
- Rajesh Kanna, P., Santhi, P. (2021). Unified Deep Learning approach for Efficient Intrusion Detection System using Integrated Spatial–Temporal Features. Knowledge-Based Systems, 226, 107132. https://doi.org/10.1016/j.knosys.2021.107132
- Khan, F. A., Gumaei, A., Derhab, A., Hussain, A. (2019). TSDL: A Two-Stage Deep Learning Model for Efficient Network Intrusion Detection. IEEE Access, 7, 30373–30385. https://doi.org/10.1109/access.2019.2899721
- Binbusayyis, A., Vaiyapuri, T. (2021). Unsupervised deep learning approach for network intrusion detection combining convolutional autoencoder and one-class SVM. Applied Intelligence, 51 (10), 7094–7108. https://doi.org/10.1007/s10489-021-02205-9
- Hnamte, V., Hussain, J. (2023). DCNNBiLSTM: An Efficient Hybrid Deep Learning-Based Intrusion Detection System. Telematics and Informatics Reports, 10, 100053. https://doi.org/10.1016/j.teler.2023.100053
- Sinha, J., Manollas, M. (2020). Efficient Deep CNN-BiLSTM Model for Network Intrusion Detection. Proceedings of the 2020 3rd International Conference on Artificial Intelligence and Pattern Recognition. https://doi.org/10.1145/3430199.3430224
- Cao, B., Li, C., Song, Y., Fan, X. (2022). Network Intrusion Detection Technology Based on Convolutional Neural Network and BiGRU. Computational Intelligence and Neuroscience, 2022, 1–20. https://doi.org/10.1155/2022/1942847
- Gu, J., Wang, Z., Kuen, J., Ma, L., Shahroudy, A., Shuai, B. et al. (2018). Recent advances in convolutional neural networks. Pattern Recognition, 77, 354–377. https://doi.org/10.1016/j.patcog.2017.10.013
- Song, Y., Luktarhan, N., Shi, Z., Wu, H. (2023). TGA: A Novel Network Intrusion Detection Method Based on TCN, BiGRU and Attention Mechanism. Electronics, 12 (13), 2849. https://doi.org/10.3390/electronics12132849
- Li, X. (2023). CNN-GRU model based on attention mechanism for large-scale energy storage optimization in smart grid. Frontiers in Energy Research, 11. https://doi.org/10.3389/fenrg.2023.1228256
- Yu, X., Li, T., Hu, A. (2020). Time-series Network Anomaly Detection Based on Behaviour Characteristics. 2020 IEEE 6th International Conference on Computer and Communications (ICCC). https://doi.org/10.1109/iccc51575.2020.9345249
- Liu, X., Liu, J. (2021). Malicious traffic detection combined deep neural network with hierarchical attention mechanism. Scientific Reports, 11 (1). https://doi.org/10.1038/s41598-021-91805-z
- Huang, Y., Chen, J., Zheng, S., Xue, Y., Hu, X. (2021). Hierarchical multi-attention networks for document classification. International Journal of Machine Learning and Cybernetics, 12 (6), 1639–1647. https://doi.org/10.1007/s13042-020-01260-x x
- Nikitenko, A. (2023). Nabory danykh dlia stvorennia system vyiavlennia merezhevykh vtorhnen z vykorystanniam neironnykh merezh. Materialy XLI naukovo-tekhnichnoi konferentsiyi molodykh vchenykh ta spetsialistiv Instytutu problem modeliuvannia v enerhetytsi im. H.Ye. Pukhova NAN Ukrainy, 104–106. Available at: https://ipme.kiev.ua/wp-content/uploads/2023/05/%D0%9C%D0%B0%D1%82%D0%B5%D1%80%D1%96%D0%B0%D0%BB%D0%B8-%D0%BA%D0%BE%D0%BD%D1%84%D0%B5%D1%80%D0%B5%D0%BD%D1%86%D1%96%D1%97-2023.pdf
- The UNSW-NB15 Dataset. Available at: https://research.unsw.edu.au/projects/unsw-nb15-dataset
- Nikitenko, A. (2023). Network intrusion detection systems based on deep learning neural networks. Naukovi pratsi DonNTU. Seriya “Informatyka, kibernetyka ta obchysliuvalna tekhnika”, 2 (37), 15–21.
- ISCX NSL-KDD dataset 2009. Available at: https://www.unb.ca/cic/datasets/nsl.html
- Xiao, Y., Xiao, X. (2019). An Intrusion Detection System Based on a Simplified Residual Network. Information, 10 (11), 356. https://doi.org/10.3390/info10110356
- Cao, B., Li, C., Song, Y., Qin, Y., Chen, C. (2022). Network Intrusion Detection Model Based on CNN and GRU. Applied Sciences, 12 (9), 4184. https://doi.org/10.3390/app12094184
- Ren, K., Yuan, S., Zhang, C., Shi, Y., Huang, Z. (2023). CANET: A hierarchical CNN-Attention model for Network Intrusion Detection. Computer Communications, 205, 170–181. https://doi.org/10.1016/j.comcom.2023.04.018
- Marir, N., Wang, H., Feng, G., Li, B., Jia, M. (2018). Distributed Abnormal Behavior Detection Approach Based on Deep Belief Network and Ensemble SVM Using Spark. IEEE Access, 6, 59657–59671. https://doi.org/10.1109/access.2018.2875045
##submission.downloads##
Опубліковано
Як цитувати
Номер
Розділ
Ліцензія
Авторське право (c) 2024 Andrii Nikitenko, Yevhen Bashkov

Ця робота ліцензується відповідно до Creative Commons Attribution 4.0 International License.
Закріплення та умови передачі авторських прав (ідентифікація авторства) здійснюється у Ліцензійному договорі. Зокрема, автори залишають за собою право на авторство свого рукопису та передають журналу право першої публікації цієї роботи на умовах ліцензії Creative Commons CC BY. При цьому вони мають право укладати самостійно додаткові угоди, що стосуються неексклюзивного поширення роботи у тому вигляді, в якому вона була опублікована цим журналом, але за умови збереження посилання на першу публікацію статті в цьому журналі.
Ліцензійний договір – це документ, в якому автор гарантує, що володіє усіма авторськими правами на твір (рукопис, статтю, тощо).
Автори, підписуючи Ліцензійний договір з ПП «ТЕХНОЛОГІЧНИЙ ЦЕНТР», мають усі права на подальше використання свого твору за умови посилання на наше видання, в якому твір опублікований. Відповідно до умов Ліцензійного договору, Видавець ПП «ТЕХНОЛОГІЧНИЙ ЦЕНТР» не забирає ваші авторські права та отримує від авторів дозвіл на використання та розповсюдження публікації через світові наукові ресурси (власні електронні ресурси, наукометричні бази даних, репозитарії, бібліотеки тощо).
За відсутності підписаного Ліцензійного договору або за відсутністю вказаних в цьому договорі ідентифікаторів, що дають змогу ідентифікувати особу автора, редакція не має права працювати з рукописом.
Важливо пам’ятати, що існує і інший тип угоди між авторами та видавцями – коли авторські права передаються від авторів до видавця. В такому разі автори втрачають права власності на свій твір та не можуть його використовувати в будь-який спосіб.









