Development of a hardware cryptosystem based on a random number generator with two types of entropy sources
DOI:
https://doi.org/10.15587/1729-4061.2022.265774Keywords:
crypto-resistance, crypto-algorithm, random numbers, pseudo-random numbers, uncertainty zone, entropy sources, cipher stabilityAbstract
In modern software, crypto-algorithms are widely used for both data encryption tasks, and authentication and integrity checks. There are well-known and proven crypto-algorithms. Their cryptoresistance is either mathematically proven or based on the need to solve a mathematically complex problem (factorization, discrete logarithm, etc.). On the other hand, in the computer world, information constantly appears about errors or «holes» in a particular program (including one that uses crypto-algorithms) or that it was broken (cracked). This creates distrust both in specific programs and in the possibility to protect something in general by cryptographic methods not only from special services, but also from ordinary hackers. A promising direction of research in this field is the implementation of a hybrid random number generator with two types of entropy sources in cryptosystems.
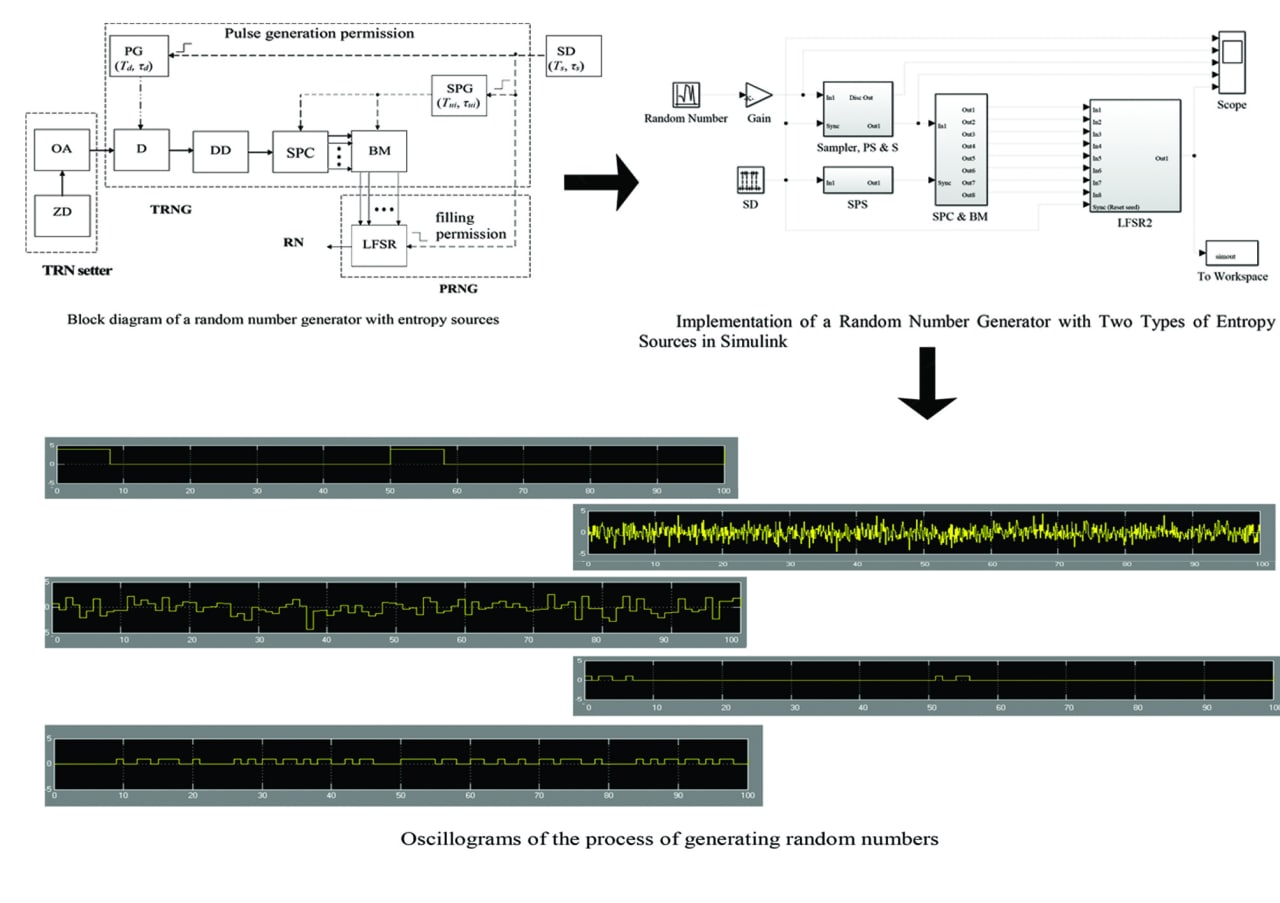
The method and means of implementing a hybrid random number generator with two types of entropy sources: external – based on Zener diode noise and internal – based on the uncertainty state of the transistor-transistor logic structure are presented. One of the options for the practical implementation of a random number generator is presented, where two sources are used as a source of entropy: an external source – Zener diode noise and an internal source – the undefined state of the transistor-transistor logic structure. The functional diagram of the proposed random number generator with two types of entropy sources is given. The MATLAB/Simulink model of the proposed random number generator is built, the results of the statistical analysis of the generated random sequences by the NIST SP 800-22 test package are given.
References
- Lienkov, S., Zhyrov, G., Pampukha, I., Chetverikov, I. (2019). Block Encryption Algorithm for Digital Information Using Open Keys for Selfgeneration of Closed Random Private Keys. 2019 IEEE International Conference on Advanced Trends in Information Theory (ATIT). doi: https://doi.org/10.1109/atit49449.2019.9030509
- Pampukha, I., Zhyrov, G., Druzhynin, V., Chetverikov, I., Lienkov, S., Komarova, L. (2021). Description and Application of Network and Terminal Security Device Based on the Block Algorithm of Cryptographic Transformation of Information Using Random Keys. 2021 IEEE 3rd International Conference on Advanced Trends in Information Theory (ATIT). doi: https://doi.org/10.1109/atit54053.2021.9678870
- Yevseiev, S., Ponomarenko, V., Laptiev, O., Milov, O., Korol, O., Milevskyi, S. et. al.; Yevseiev, S., Ponomarenko, V., Laptiev, O., Milov, O. (Eds.) (2021). Synergy of building cybersecurity systems. Kharkiv: РС ТЕСHNOLOGY СЕNTЕR, 188. doi: https://doi.org/10.15587/978-617-7319-31-2
- Iovane, G., Amorosia, A., Benedetto, E., Lamponi, G. (2015). An Information Fusion approach based on prime numbers coming from RSA algorithm and Fractals for secure coding. Journal of Discrete Mathematical Sciences and Cryptography, 18 (5), 455–479. doi: https://doi.org/10.1080/09720529.2014.894311
- Long, M., Chen, Y. (2019). Average throughput and BER analysis for energy harvesting communications. IET Communications, 13 (3), 289–296.
- Glory, F. Z., Ul Aftab, A., Tremblay-Savard, O., Mohammed, N. (2019). Strong Password Generation Based On User Inputs. 2019 IEEE 10th Annual Information Technology, Electronics and Mobile Communication Conference (IEMCON). doi: https://doi.org/10.1109/iemcon.2019.8936178
- Lemire, D. (2019). Fast Random Integer Generation in an Interval. ACM Transactions on Modeling and Computer Simulation, 29 (1), 1–12. doi: https://doi.org/10.1145/3230636
- Chakrabarty, D., Sarma, B. K. (2017). Comparison of degree of randomness of the tables of random numbers due to Tippet, Fisher & Yates, Kendall & Smith and Rand corporation. Journal of reliability and statistical studies, 10 (1), 27–42. Available at: https://www.journal.riverpublishers.com/index.php/JRSS/article/view/2205/1526
- Ewert, M. (2018). A Random Number Generator Based on Electronic Noise and the Xorshift Algorithm. Proceedings of the 2018 VII International Conference on Network, Communication and Computing - ICNCC 2018. doi: https://doi.org/10.1145/3301326.3301359
- Kim, J., Nili, H., Truong, N. D., Ahmed, T., Yang, J., Jeong, D. S. et. al. (2019). Nano-Intrinsic True Random Number Generation: A Device to Data Study. IEEE Transactions on Circuits and Systems I: Regular Papers, 66 (7), 2615–2626. doi: https://doi.org/10.1109/tcsi.2019.2895045
- Kyrychok, R., Laptiev, O., Lisnevskyi, R., Kozlovskyi, V., Klobukov, V. (2022). Development of a method for checking vulnerabilities of a corporate network using Bernstein transformations. Eastern-European Journal of Enterprise Technologies, 1 (9 (115)), 93–101. doi: https://doi.org/10.15587/1729-4061.2022.253530
- Petrivskyi, V., Shevchenko, V., Yevseiev, S., Milov, O., Laptiev, O., Bychkov, O. et. al. (2022). Development of a modification of the method for constructing energy-efficient sensor networks using static and dynamic sensors. Eastern-European Journal of Enterprise Technologies, 1 (9 (115)), 15–23. doi: https://doi.org/10.15587/1729-4061.2022.252988
- Vlasyk, H., Zamrii, I., Shkapa, V., Laptiev, S., Kalyniuk, A., Laptieva, T. (2021). The Method of Solving Problems of Optimal Restoration of Telecommunication Signals. 2021 IEEE 3rd International Conference on Advanced Trends in Information Theory (ATIT). doi: https://doi.org/10.1109/atit54053.2021.9678649
- Laptiev, O. et. al. (2019). The Method of Hidden Transmitters Detection based on the Differential Transformation Model. International Journal of Advanced Trends in Computer Science and Engineering, 8 (6), 2840–2846. doi: https://doi.org/10.30534/ijatcse/2019/26862019
- Laptiev, O., Tkachev, V., Maystrov, O., Krasikov, O., Open’ko, P., Khoroshko, V., Parkhuts, L. (2021). The method of spectral analysis of the determination of random digital signals. International Journal of Communication Networks and Information Security (IJCNIS), 13 (2). Available at: https://www.ijcnis.org/index.php/ijcnis/article/view/5008
- Ruban, I., Martovytskyi, V., Lukova-Chuiko, N. (2016). Designing a monitoring model for cluster super–computers. Eastern-European Journal of Enterprise Technologies, 6 (2 (84)), 32–37. doi: https://doi.org/10.15587/1729-4061.2016.85433
Downloads
Published
How to Cite
Issue
Section
License
Copyright (c) 2022 Serhii Yevseiev, Khazail Rzayev, Oleksandr Laptiev, Ruslan Hasanov, Oleksandr Milov, Bahar Asgarova, Jala Camalova, Serhii Pohasii

This work is licensed under a Creative Commons Attribution 4.0 International License.
The consolidation and conditions for the transfer of copyright (identification of authorship) is carried out in the License Agreement. In particular, the authors reserve the right to the authorship of their manuscript and transfer the first publication of this work to the journal under the terms of the Creative Commons CC BY license. At the same time, they have the right to conclude on their own additional agreements concerning the non-exclusive distribution of the work in the form in which it was published by this journal, but provided that the link to the first publication of the article in this journal is preserved.
A license agreement is a document in which the author warrants that he/she owns all copyright for the work (manuscript, article, etc.).
The authors, signing the License Agreement with TECHNOLOGY CENTER PC, have all rights to the further use of their work, provided that they link to our edition in which the work was published.
According to the terms of the License Agreement, the Publisher TECHNOLOGY CENTER PC does not take away your copyrights and receives permission from the authors to use and dissemination of the publication through the world's scientific resources (own electronic resources, scientometric databases, repositories, libraries, etc.).
In the absence of a signed License Agreement or in the absence of this agreement of identifiers allowing to identify the identity of the author, the editors have no right to work with the manuscript.
It is important to remember that there is another type of agreement between authors and publishers – when copyright is transferred from the authors to the publisher. In this case, the authors lose ownership of their work and may not use it in any way.








