Development of reference incident management model
DOI:
https://doi.org/10.15587/1729-4061.2022.266387Keywords:
incident management, service interruption, support line, resolution time, SLA (service level agreement), reference modelAbstract
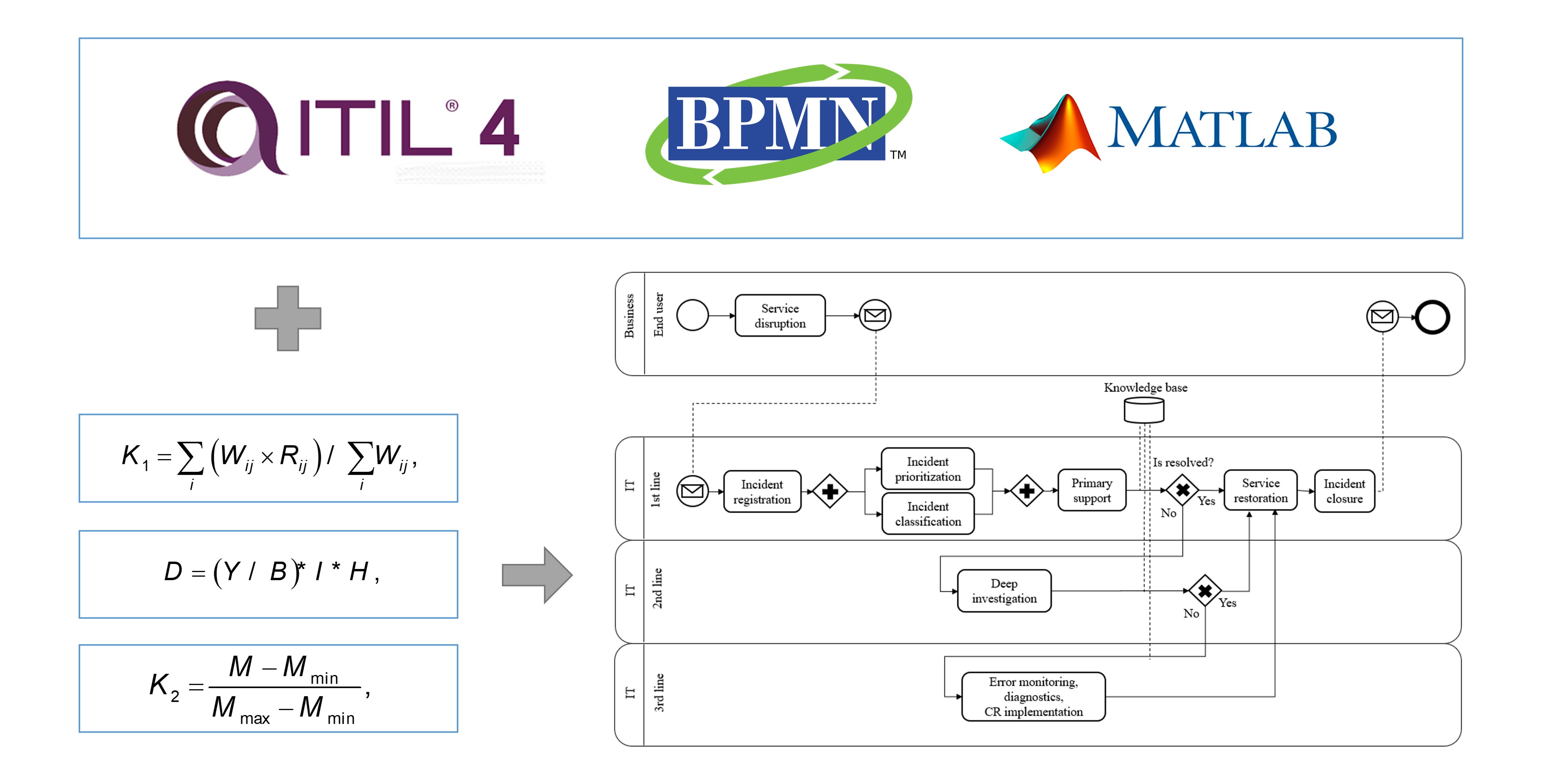
One of the most important tasks of improving the information technology infrastructure of an enterprise is to increase the efficiency of the incident management system. The relevance of this study lies in the fact that at present the work of the technical support service in the conditions of a large flow of applications accelerates violation of the deadlines for resolution established by the business. It, in turn, leads to downtime of information systems and financial losses of the enterprise. This article analyzes the feasibility of introducing a third line of technical support to increase the proportion of incidents resolved within the framework of the Service Level Agreement adopted at the enterprise. A comparative analysis of the widely used two-level model with the proposed three-level model in this work is considered, using business process model notation. The effectiveness of the model is confirmed by automated computations using metrics, by calculating the rate and satisfaction coefficients within the framework of two and three levels of the model and then comparing these indicators to establish patterns. Thus, it is possible to track how successfully and timely incidents of information systems are resolved, which in turn directly reflects the availability and correct functioning of systems and the entire company.
The company's practical losses due to system downtime were calculated, as well as the resulting financial losses before and after the adopting of the three-level system, taking into account the associated costs to identify if the initiation of the model is justified and profitable.
Thus, the proposed model can be adopted by organizations in order to improve the quality of services provided by the IT department, to reduce the effect and impact of incidents on the performance and availability of systems that affect the formation of financial statements
References
- Nikulin, V., Shibaikin, S., Sokolova, M. S. (2022). Application of machine learning techniques for automated classification and routing in ITIL library. Vestnik of Astrakhan State Technical University. Series: Management, Computer Science and Informatics, 2022 (1), 42–52. doi: https://doi.org/10.24143/2073-5529-2022-1-42-52
- Blinnikova, A. V., Nesterova, Ju. O. (2020). Incident management in ITSM using artificial intelligence. Vestnik Universiteta, 6, 36–40. doi: https://doi.org/10.26425/1816-4277-2020-6-36-40
- Loginova, A. (2021). An overview of regulatory sources and practices of information security incidents management. The Herald of the Siberian State University of Telecommunications and Informatics, 1, 50–59. doi: https://doi.org/10.55648/1998-6920-2021-15-1-50-59
- Mayorova, E. V. (2020). Methodological Aspects of Responding to Information Security Incidents in the Digital Economy. Petersburg Economic Journal, 1, 155–164. doi: https://doi.org/10.25631/PEJ.2020.1.155.162
- Palilingan, V. R., Batmetan, J. R. (2018). Incident Management in Academic Information System using ITIL Framework. IOP Conference Series: Materials Science and Engineering, 306, 012110. doi: https://doi.org/10.1088/1757-899x/306/1/012110
- Serikbayeva, S., Tussupov, J., Sambetbayeva, M., Yerimbetova, A., Sadirmekova, Z., Tungatarova, A. et al. (2021). Development of a model and technology of access to documents in scientific and educational activities. Eastern-European Journal of Enterprise Technologies, 6 (2 (114)), 44–58. doi: https://doi.org/10.15587/1729-4061.2021.248506
- Sembina, G. (2022). Building a Scoring Model Using the Adaboost Ensemble Model. 2022 International Conference on Smart Information Systems and Technologies (SIST). doi: https://doi.org/10.1109/sist54437.2022.9945713
- Ocheredko, A. R., Bachmanov, D. A., Putyato, M. M., Makaryan, A. S. (2021). Research of IRP systems based on the analysis of mechanisms of response to information security incidents. CASPIAN JOURNAL: Control and High Technologies, 53 (1), 74–82. doi: https://doi.org/10.21672/2074-1707.2021.53.1.074-082
- Avramenko, V. S., Malikov, A. V. (2020). Procedure of diagnosis security computer incidents in automated special purpose systems. H&ES Research, 12 (1), 44–52. doi: https://doi.org/10.36724/2409-5419-2020-12-1-44-52
- Muromtsev, D. Yu., Popov, S. V., Shamkin, V. N. (2020). Improvement of the Information Security Subsystem in the Bank Information Security Monitoring System. Vestnik Tambovskogo Gosudarstvennogo Tehnicheskogo Universiteta, 26 (2), 176–187. doi: https://doi.org/10.17277/vestnik.2020.02.pp.176-187
- Understanding the Cost of IT System Failure to Your Business. Available at: https://blog.power-net.com.au/blog/understanding-the-cost-of-it-system-failure-to-your-business
Downloads
Published
How to Cite
Issue
Section
License
Copyright (c) 2022 Gulbakyt Sembina, Karina Mayandinova, Lyazat Naizabayeva, Saule Sagnayeva

This work is licensed under a Creative Commons Attribution 4.0 International License.
The consolidation and conditions for the transfer of copyright (identification of authorship) is carried out in the License Agreement. In particular, the authors reserve the right to the authorship of their manuscript and transfer the first publication of this work to the journal under the terms of the Creative Commons CC BY license. At the same time, they have the right to conclude on their own additional agreements concerning the non-exclusive distribution of the work in the form in which it was published by this journal, but provided that the link to the first publication of the article in this journal is preserved.
A license agreement is a document in which the author warrants that he/she owns all copyright for the work (manuscript, article, etc.).
The authors, signing the License Agreement with TECHNOLOGY CENTER PC, have all rights to the further use of their work, provided that they link to our edition in which the work was published.
According to the terms of the License Agreement, the Publisher TECHNOLOGY CENTER PC does not take away your copyrights and receives permission from the authors to use and dissemination of the publication through the world's scientific resources (own electronic resources, scientometric databases, repositories, libraries, etc.).
In the absence of a signed License Agreement or in the absence of this agreement of identifiers allowing to identify the identity of the author, the editors have no right to work with the manuscript.
It is important to remember that there is another type of agreement between authors and publishers – when copyright is transferred from the authors to the publisher. In this case, the authors lose ownership of their work and may not use it in any way.








