Developing a new encryption algorithm for images transmitted through WSN systems
DOI:
https://doi.org/10.15587/1729-4061.2023.285261Keywords:
wireless sensor network (WSN), military system SRS algorithm image encryptionAbstract
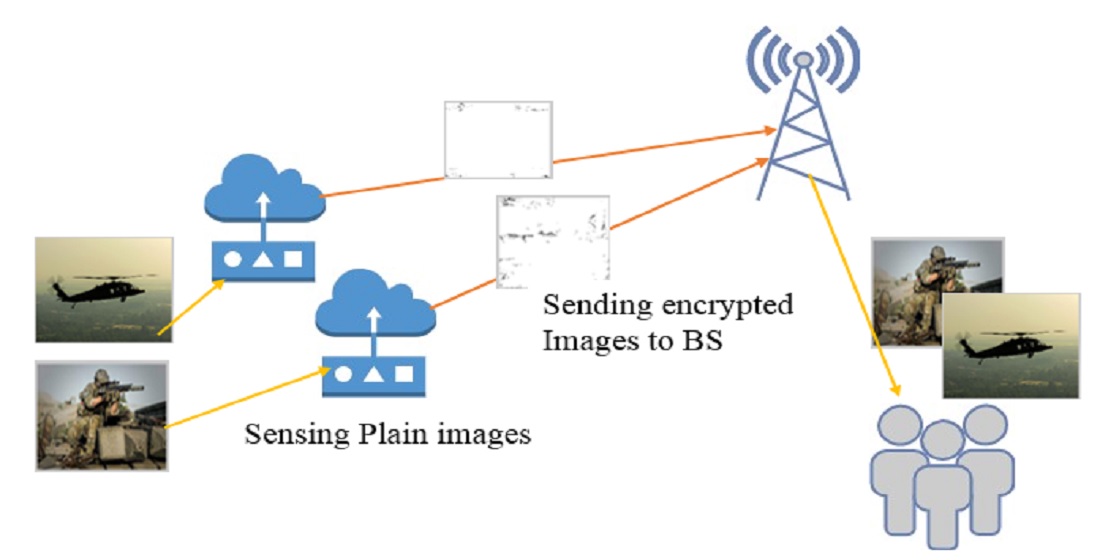
Wireless sensor networks (WSNs) have up until now faced many challenges because of their open, wide-ranging, and resource-limited nature, including security, efficiency, and energy consumption. In the military system, it is essential to provide high-level security to the significant data over wireless network which is proved to be unreliable public communications. To solve the above problem, high level of security with minimum complexity should be applied to be adequate to limited capabilities of transmission system. This paper presents a new algorithm named (SRS) for encrypting transmitted military images to keep them from getting hacked or broken by WSN. The SRS algorithm is designed to be lightweight, fast, and secure, taking into consideration the limited capabilities of the transmission system. It is implemented as a public key cryptosystem specifically designed for image encryption. The algorithm consists of two parts: encryption and decryption. The proposed system suggested some equations and calculations that are applied to the plain and coded images after being transmitted over the WSN. The results of testing the simulation model demonstrate the effectiveness of the system by evaluation using various metrics such as Signal-to-Noise Ratio (SNR), Mean Squared Error (MSE), and Peak Signal-to-Noise Ratio (PSNR). Overall, the paper presents a new encryption algorithm, SRS, specifically designed for securing military images transmitted over wireless sensor networks. The algorithm aims to provide a balance between security, efficiency, and energy consumption, considering the resource-limited nature of WSNs. The simulation results indicate the improvement of the proposed system by 13 %, 10 %, and 55 % in packet delivery ratio (PDR), throughput, and dropping ratio, respectively, and it shows that the suggested SRS method increased execution time by 67 % compared to RSA based algorithm
References
- Khashan, O. A., Ahmad, R., Khafajah, N. M. (2021). An automated lightweight encryption scheme for secure and energy-efficient communication in wireless sensor networks. Ad Hoc Networks, 115, 102448. doi: https://doi.org/10.1016/j.adhoc.2021.102448
- Yi, L., Tong, X., Wang, Z., Zhang, M., Zhu, H., Liu, J. (2019). A Novel Block Encryption Algorithm Based on Chaotic S-Box for Wireless Sensor Network. IEEE Access, 7, 53079–53090. doi: https://doi.org/10.1109/access.2019.2911395
- Khashan, O. A. (2020). Hybrid Lightweight Proxy Re-Encryption Scheme for Secure Fog-to-Things Environment. IEEE Access, 8, 66878–66887. doi: https://doi.org/10.1109/access.2020.2984317
- Yas, R. M., Hashim, S. (2021). Intelligent Approaches for Enhancing Networked Routing Protocol. Iraqi Journal of Science, 4121–4147. doi: https://doi.org/10.24996/ijs.2021.62.11.32
- Mathur, S., Gupta, D., Goar, V., Kuri, M. (2017). Analysis and design of enhanced RSA algorithm to improve the security. 2017 3rd International Conference on Computational Intelligence & Communication Technology (CICT). doi: https://doi.org/10.1109/ciact.2017.7977330
- Rafash, A. G. H., Saeed, E. M. H., Talib, A.-S. M. (2021). Development of an enhanced scatter search algorithm using discrete chaotic Arnold’s cat map. Eastern-European Journal of Enterprise Technologies, 6 (4 (114)), 15–20. doi: https://doi.org/10.15587/1729-4061.2021.234915
- Khashan, O. A., Zin, A. M., Sundararajan, E. A. (2014). Performance study of selective encryption in comparison to full encryption for still visual images. Journal of Zhejiang University SCIENCE C, 15 (6), 435–444. doi: https://doi.org/10.1631/jzus.c1300262
- Kadhim, S. A., abdual Rahman, S. A. A. (2021). A proposed method for encrypting and sending confidential data using polynomials. Global Journal of Engineering and Technology Advances, 8 (2), 082–087. doi: https://doi.org/10.30574/gjeta.2021.8.2.0133
- Szalachowski, P., Kotulski, Z. (2012). One-Time Broadcast Encryption Schemes in Distributed Sensor Networks. International Journal of Distributed Sensor Networks, 8 (3), 536718. doi: https://doi.org/10.1155/2012/536718
- Muhajjar, R. A., Flayh, N. A., Al-Zubaidie, M. (2023). A Perfect Security Key Management Method for Hierarchical Wireless Sensor Networks in Medical Environments. Electronics, 12 (4), 1011. doi: https://doi.org/10.3390/electronics12041011
- Wazery, Y. M., Ali, M. A. S. (2018). An Intuitionistic Fuzzy Sets Implementation for Key Distribution in Hybrid Message Encryption Over Wsns. International Journal of Advances in Applied Sciences, 7 (3), 273. doi: https://doi.org/10.11591/ijaas.v7.i3.pp273-285
- Zhao, G., Yang, X., Zhou, B., Wei, W. (2010). RSA-based digital image encryption algorithm in wireless sensor networks. 2010 2nd International Conference on Signal Processing Systems. doi: https://doi.org/10.1109/icsps.2010.5555601
- Elhoseny, M., Elminir, H., Riad, A., Yuan, X. (2016). A secure data routing schema for WSN using Elliptic Curve Cryptography and homomorphic encryption. Journal of King Saud University - Computer and Information Sciences, 28 (3), 262–275. doi: https://doi.org/10.1016/j.jksuci.2015.11.001
- Ramasamy, J., Kumaresan, J. S. (2020). Image Encryption and Cluster Based Framework for Secured Image Transmission in Wireless Sensor Networks. Wireless Personal Communications, 112 (3), 1355–1368. doi: https://doi.org/10.1007/s11277-020-07106-7
- Leelavathi, G., Shaila, K., Venugopal, K. R. (2020). Message and Image Encryption Embedding Data to GF(2m) Elliptic Curve Point for Nodes in Wireless Sensor Networks. EAI/Springer Innovations in Communication and Computing, 329–338. doi: https://doi.org/10.1007/978-3-030-19562-5_33
- Li, H., Ge, B., Xia, C., Wang, T. (2021). Image Encryption for Wireless Sensor Networks with Modified Logistic Map and New Hash Algorithm. Wireless Algorithms, Systems, and Applications, 29–37. doi: https://doi.org/10.1007/978-3-030-86137-7_4
- Abdulhameed, H. A., Abdalmaaen, H. F., Mohammed, A. T., Mosleh, M. F., Abdulhameed, A. A. (2022). A Lightweight Hybrid Cryptographic Algorithm for WSNs Tested by the Diehard Tests and the Raspberry Pi. 2022 International Conference on Computer Science and Software Engineering (CSASE). doi: https://doi.org/10.1109/csase51777.2022.9759589
- Aruna Deepthi, S., Aruna, V., Leelavathi, R. (2022). Image Transmission Using Leach and Security Using RSA in Wireless Sensor Networks. Advances in Intelligent Systems and Computing, 39–51. doi: https://doi.org/10.1007/978-981-16-9573-5_3
Downloads
Published
How to Cite
Issue
Section
License
Copyright (c) 2023 Sanaa ahmed kadhim, Ruwaida Mohammed yas, Saad abdual azize Abdual Rahman, Sura Khalil Abd

This work is licensed under a Creative Commons Attribution 4.0 International License.
The consolidation and conditions for the transfer of copyright (identification of authorship) is carried out in the License Agreement. In particular, the authors reserve the right to the authorship of their manuscript and transfer the first publication of this work to the journal under the terms of the Creative Commons CC BY license. At the same time, they have the right to conclude on their own additional agreements concerning the non-exclusive distribution of the work in the form in which it was published by this journal, but provided that the link to the first publication of the article in this journal is preserved.
A license agreement is a document in which the author warrants that he/she owns all copyright for the work (manuscript, article, etc.).
The authors, signing the License Agreement with TECHNOLOGY CENTER PC, have all rights to the further use of their work, provided that they link to our edition in which the work was published.
According to the terms of the License Agreement, the Publisher TECHNOLOGY CENTER PC does not take away your copyrights and receives permission from the authors to use and dissemination of the publication through the world's scientific resources (own electronic resources, scientometric databases, repositories, libraries, etc.).
In the absence of a signed License Agreement or in the absence of this agreement of identifiers allowing to identify the identity of the author, the editors have no right to work with the manuscript.
It is important to remember that there is another type of agreement between authors and publishers – when copyright is transferred from the authors to the publisher. In this case, the authors lose ownership of their work and may not use it in any way.








