Enhancing healthcare data security: a two-step authentication scheme with cloud technology and blockchain
DOI:
https://doi.org/10.15587/1729-4061.2023.289325Keywords:
blockchain technology, two-step authentication, medical data security, fingerprintAbstract
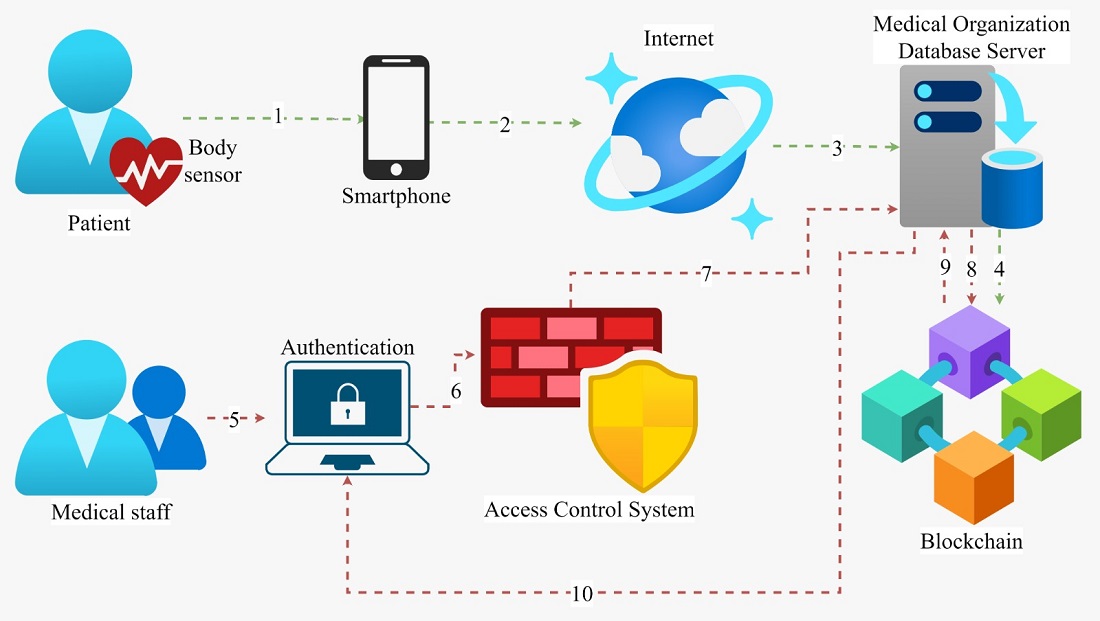
In the modern world, medical data leakage has many external and internal threats. Information systems of medical organizations are constantly subject to various types of cyber-attacks and unauthorized penetration attempts, which leads to the publication of patient medical data online. Existing authentication schemes using blockchain technologies in medical organization systems ensure the integrity of medical data and secure access to patient data. However, one of the serious reasons for unauthorized access to the healthcare system is the human factor, which manifests itself in a negligent attitude towards account security, non-compliance with the rules and policies of information security, and transferring to third parties personal login details to the information system of a medical organization. This paper proposes a solution to this problem through an improved two-step authentication scheme using cloud technology and blockchain. The combined use of cloud technologies and blockchain is a distinctive feature of the proposed authentication scheme since it provides two levels of protection:
1) two-step authentication, the second stage of which includes biometrics through a mobile application. It prevents unauthorized access to the system by third parties;
2) cloud encryption keys for decrypting medical data, which are also accessed through the user's biometrics. The practical part of the paper includes the implementation of biometric login in Python using the OpenCV library. As a result of the practical part, unique fingerprint samples were obtained. The biometric user verification algorithm is designed for a mobile application, which we plan to implement in the future
References
- Jansen, W. (2003). Authenticating users on handheld devices. Canadian Information Technology Security Symposium, 1–12. Available at: https://tsapps.nist.gov/publication/get_pdf.cfm?pub_id=50736
- O’Gorman, L. (2003). Comparing passwords, tokens, and biometrics for user authentication. Proceedings of the IEEE, 91 (12), 2021–2040. doi: https://doi.org/10.1109/jproc.2003.819611
- Almadani, M. S., Alotaibi, S., Alsobhi, H., Hussain, O. K., Hussain, F. K. (2023). Blockchain-based multi-factor authentication: A systematic literature review. Internet of Things, 23, 100844. doi: https://doi.org/10.1016/j.iot.2023.100844
- Barkadehi, M. H., Nilashi, M., Ibrahim, O., Zakeri Fardi, A., Samad, S. (2018). Authentication systems: A literature review and classification. Telematics and Informatics, 35 (5), 1491–1511. doi: https://doi.org/10.1016/j.tele.2018.03.018
- Addobea, A. A., Li, Q., Obiri, I. A., Hou, J. (2023). Secure multi-factor access control mechanism for pairing blockchains. Journal of Information Security and Applications, 74, 103477. doi: https://doi.org/10.1016/j.jisa.2023.103477
- Al-Shareeda, M. A., Saare, M. A., Manickam, S. (2023). The blockchain internet of things: review, opportunities, challenges, and recommendations. Indonesian Journal of Electrical Engineering and Computer Science, 31 (3), 1673. doi: https://doi.org/10.11591/ijeecs.v31.i3.pp1673-1683
- Zhou, B., Zhao, J., Chen, G., Yin, Y. (2023). Security Authentication Mechanism of Spatio-Temporal Big Data Based on Blockchain. Applied Sciences, 13 (11), 6641. doi: https://doi.org/10.3390/app13116641
- Mohammed, Z. H., Chankaew, K., Vallabhuni, R. R., Sonawane, V. R., Ambala, S., S, M. (2023). Blockchain-enabled bioacoustics signal authentication for cloud-based electronic medical records. Measurement: Sensors, 26, 100706. doi: https://doi.org/10.1016/j.measen.2023.100706
- Li, C., Jiang, B., Guo, Y., Xin, X. (2023). Efficient Group Blind Signature for Medical Data Anonymous Authentication in Blockchain-Enabled IoMT. Computers, Materials & Continua, 76 (1), 591–606. doi: https://doi.org/10.32604/cmc.2023.038129
- Chen, F., Tang, Y., Cheng, X., Xie, D., Wang, T., Zhao, C. (2021). Blockchain-Based Efficient Device Authentication Protocol for Medical Cyber-Physical Systems. Security and Communication Networks, 2021, 1–13. doi: https://doi.org/10.1155/2021/5580939
- Li, C.-T., Shih, D.-H., Wang, C.-C., Chen, C.-L., Lee, C.-C. (2020). A Blockchain Based Data Aggregation and Group Authentication Scheme for Electronic Medical System. IEEE Access, 8, 173904–173917. doi: https://doi.org/10.1109/access.2020.3025898
- Gibson, A., Thamilarasu, G. (2020). Protect Your Pacemaker: Blockchain based Authentication and Consented Authorization for Implanted Medical Devices. Procedia Computer Science, 171, 847–856. doi: https://doi.org/10.1016/j.procs.2020.04.092
- Shi, S., Luo, M., Wen, Y., Wang, L., He, D. (2022). A Blockchain-Based User Authentication Scheme with Access Control for Telehealth Systems. Security and Communication Networks, 2022, 1–18. doi: https://doi.org/10.1155/2022/6735003
- Shukla, S., Thakur, S., Hussain, S., Breslin, J. G., Jameel, S. M. (2021). Identification and Authentication in Healthcare Internet-of-Things Using Integrated Fog Computing Based Blockchain Model. Internet of Things, 15, 100422. doi: https://doi.org/10.1016/j.iot.2021.100422
- Alzubi, J. A. (2021). Blockchain-based Lamport Merkle Digital Signature: Authentication tool in IoT healthcare. Computer Communications, 170, 200–208. doi: https://doi.org/10.1016/j.comcom.2021.02.002
- Yazdinejad, A., Srivastava, G., Parizi, R. M., Dehghantanha, A., Choo, K.-K. R., Aledhari, M. (2020). Decentralized Authentication of Distributed Patients in Hospital Networks Using Blockchain. IEEE Journal of Biomedical and Health Informatics, 24 (8), 2146–2156. doi: https://doi.org/10.1109/jbhi.2020.2969648
- Xiang, X., Wang, M., Fan, W. (2020). A Permissioned Blockchain-Based Identity Management and User Authentication Scheme for E-Health Systems. IEEE Access, 8, 171771–171783. doi: https://doi.org/10.1109/access.2020.3022429
- Tao, Q., Liu, S., Zhang, J., Jiang, J., Jin, Z., Huang, Y. et al. (2023). Clinical applications of smart wearable sensors. IScience, 26 (9), 107485. doi: https://doi.org/10.1016/j.isci.2023.107485
- Altay, A., Learney, R., Güder, F., Dincer, C. (2022). Sensors in blockchain. Trends in Biotechnology, 40 (2), 141–144. doi: https://doi.org/10.1016/j.tibtech.2021.04.011
- Rouhani, S., Deters, R. (2019). Blockchain based access control systems: State of the art and challenges. IEEE/WIC/ACM International Conference on Web Intelligence. doi: https://doi.org/10.1145/3350546.3352561
- Thapliyal, S., Wazid, M., Singh, D. P., Das, A. K., Shetty, S., Alqahtani, A. (2023). Design of Robust Blockchain-Envisioned Authenticated Key Management Mechanism for Smart Healthcare Applications. IEEE Access, 11, 93032–93047. doi: https://doi.org/10.1109/access.2023.3310264
- Tanwar, S., Parekh, K., Evans, R. (2020). Blockchain-based electronic healthcare record system for healthcare 4.0 applications. Journal of Information Security and Applications, 50, 102407. doi: https://doi.org/10.1016/j.jisa.2019.102407
- Aliya, B., Olga, U., Yenlik, B., Sogukpinar, I. (2023). Ensuring Information Security of Web Resources Based on Blockchain Technologies. International Journal of Advanced Computer Science and Applications, 14 (6). doi: https://doi.org/10.14569/ijacsa.2023.0140689
- Basori, A. A., Ariffin, N. H. M. (2022). The adoption factors of two-factors authentication in blockchain technology for banking and financial institutions. Indonesian Journal of Electrical Engineering and Computer Science, 26 (3), 1758. doi: https://doi.org/10.11591/ijeecs.v26.i3.pp1758-1764
- Papaioannou, M., Karageorgou, M., Mantas, G., Sucasas, V., Essop, I., Rodriguez, J., Lymberopoulos, D. (2020). A Survey on Security Threats and Countermeasures in Internet of Medical Things (IoMT). Transactions on Emerging Telecommunications Technologies, 33 (6). doi: https://doi.org/10.1002/ett.4049
- Gowda, N. C., Shaw, S. et al. (2023). Digital Signatures in Digital Communications: A Review. International Journal of Computational Learning & Intelligence, 2 (2), 76–86. doi: https://doi.org/10.5281/zenodo.7920995
- Nysanbayeva, S., Wójcik, W., Ussatova, O. (2019). Algorithm for generating temporary password based on the two- factor authentication model. Przegląd Elektrotechniczny, 1 (5), 103–107. doi: https://doi.org/10.15199/48.2019.05.25
- Indriyawati, H., Winarti, T., Vydia, V. (2021). Web-based document certification system with advanced encryption standard digital signature. Indonesian Journal of Electrical Engineering and Computer Science, 22 (1), 516. doi: https://doi.org/10.11591/ijeecs.v22.i1.pp516-521
- Yenlik, B., Оlga, U., Rustem, B., Saule, N. (2020). Development of an automated system model of information protection in the cross-border exchange. Cogent Engineering, 7 (1), 1724597. doi: https://doi.org/10.1080/23311916.2020.1724597
- Mehbodniya, A., Webber, J. L., Neware, R., Arslan, F., Pamba, R. V., Shabaz, M. (2022). Modified Lamport Merkle Digital Signature blockchain framework for authentication of internet of things healthcare data. Expert Systems, 39 (10). doi: https://doi.org/10.1111/exsy.12978
- Glover, J. D., Sudderick, Z. R., Shih, B. B.-J., Batho-Samblas, C., Charlton, L., Krause, A. L. et al. (2023). The developmental basis of fingerprint pattern formation and variation. Cell, 186 (5), 940-956.e20. doi: https://doi.org/10.1016/j.cell.2023.01.015
- Sugadev, M., Sreekar, B. V. S. S., Velan, B. (2020). Development of open-CV framework for minutiae Extraction and matching of fingerprints. 2020 Third International Conference on Smart Systems and Inventive Technology (ICSSIT). doi: https://doi.org/10.1109/icssit48917.2020.9214209
Downloads
Published
How to Cite
Issue
Section
License
Copyright (c) 2023 Olga Ussatova, Shakirt Makilenov, Arshidinova Mukaddas, Saule Amanzholova, Yenlik Begimbayeva, Nikita Ussatov

This work is licensed under a Creative Commons Attribution 4.0 International License.
The consolidation and conditions for the transfer of copyright (identification of authorship) is carried out in the License Agreement. In particular, the authors reserve the right to the authorship of their manuscript and transfer the first publication of this work to the journal under the terms of the Creative Commons CC BY license. At the same time, they have the right to conclude on their own additional agreements concerning the non-exclusive distribution of the work in the form in which it was published by this journal, but provided that the link to the first publication of the article in this journal is preserved.
A license agreement is a document in which the author warrants that he/she owns all copyright for the work (manuscript, article, etc.).
The authors, signing the License Agreement with TECHNOLOGY CENTER PC, have all rights to the further use of their work, provided that they link to our edition in which the work was published.
According to the terms of the License Agreement, the Publisher TECHNOLOGY CENTER PC does not take away your copyrights and receives permission from the authors to use and dissemination of the publication through the world's scientific resources (own electronic resources, scientometric databases, repositories, libraries, etc.).
In the absence of a signed License Agreement or in the absence of this agreement of identifiers allowing to identify the identity of the author, the editors have no right to work with the manuscript.
It is important to remember that there is another type of agreement between authors and publishers – when copyright is transferred from the authors to the publisher. In this case, the authors lose ownership of their work and may not use it in any way.








