Determining quality indicators for projects of information protection of information activity objects
DOI:
https://doi.org/10.15587/1729-4061.2023.291616Keywords:
information security, quality of projects, security of protection objects, comparison of the quality of information protection projectsAbstract
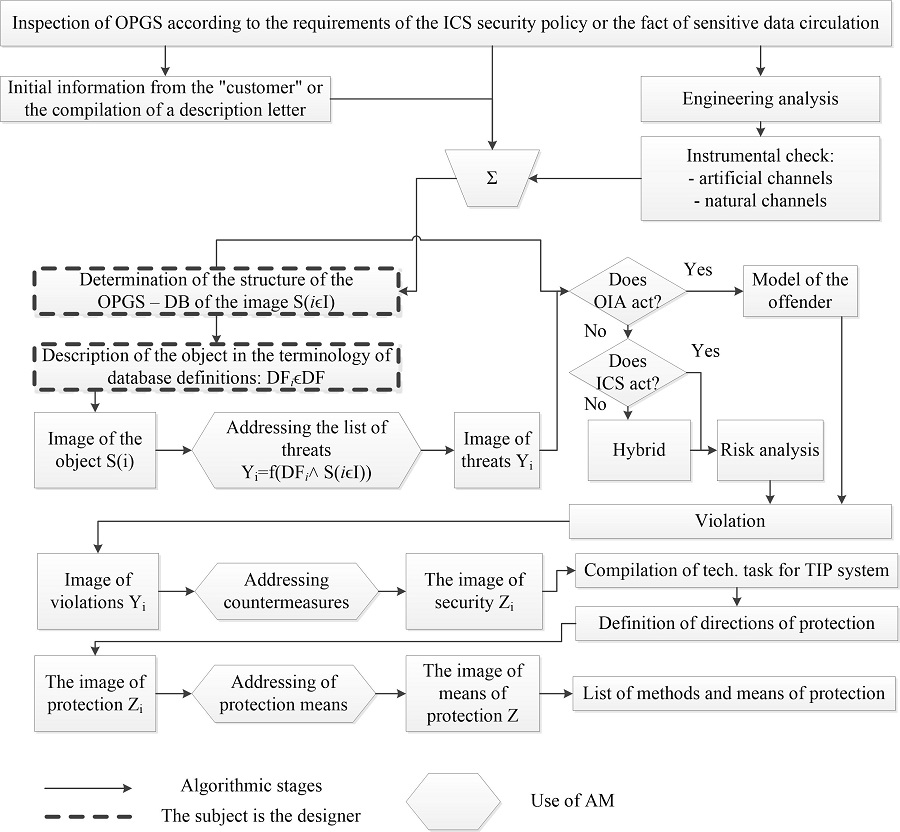
The design and analysis of the effectiveness of modern integrated information protection systems (IIPS) is complicated by the influence of the designer's subjective decisions regarding methods and means of protection, the need to determine the quality criteria for the functioning of the designed objects. The work is aimed at improving the technology of automated design of IIPS by determining the quality of projects. When creating a database (DB) of objects with such "qualitative" performance indicators of information protection systems, it is possible to compare existing and new protection objects and to adjust the protection projects of existing objects. Moreover, the ontological properties of active and threat-resistant objects are taken into account.
To illustrate the use of the methodology for determining and comparing the quality of projects, an example of comparing the quality of projects obtained in different ways is given. One way currently operating involves the use of expert evaluation of the quality of protection projects for existing facilities. The second way is intended for objects defined as objects of protection of the general structure (OPGS) and involves a principally objective assessment of design quality using known quality diagrams and control of Ishikawa and Pareto design consequences. As a result of the given example, it was determined that the quality of projects according to quality diagrams and control of design consequences should increase by more than two times.
The proposed method of comparing the quality of information protection projects for different objects or different protection projects of one object allows to improve the process of creating information protection projects. At the same time, it is possible to exclude the human controller from the process of determining the reliability of object protection. It also allows you to automate the design process, reduce the time and cost of design costs
References
- DSTU 3396.0-96. Information protection. Technical protection of information. Basic principles. Available at: https://tzi.com.ua/downloads/DSTU%203396.0-96.pdf
- ND TZI 3.7-003-2005. Poriadok provedennia robit iz stvorennia kompleksnoi systemy zakhystu informatsiyi v informatsiyno-telekomunikatsiyniy systemi. Available at: https://tzi.com.ua/downloads/3.7-003-2005.pdf
- Jiang, Y., Ye, J., Zhang, Z. (2023). Protection and Utilization of Personal Information in the Context of Big Data. 2023 International Conference on Distributed Computing and Electrical Circuits and Electronics (ICDCECE). doi: https://doi.org/10.1109/icdcece57866.2023.10151146
- Blix, F., Elshekeil, S. A., Laoyookhong, S. (2017). Data protection by design in systems development: From legal requirements to technical solutions. 2017 12th International Conference for Internet Technology and Secured Transactions (ICITST). doi: https://doi.org/10.23919/icitst.2017.8356355
- Lutsenko, V., Progonov, D. (2022). Application of the principle of information objects description formalization for the design of information protection systems. Eastern-European Journal of Enterprise Technologies, 6 (9 (120)), 28–37. doi: https://doi.org/10.15587/1729-4061.2022.269030
- Yaremchuk, Yu. Ye., Pavlovskyi, P. V., Kataiev, V. S., Siniuhin, V. V. Kompleksni systemy zakhystu informatsiyi. Available at: https://web.posibnyky.vntu.edu.ua/fmib/41yaremchuk_kompleksni_systemy_zahystu_informaciyi/
- Yudin, O. K., Korchenko, O. H., Konakhovych, H. F. (2009). Zakhyst informatsiyi v merezhakh peredachi danykh. Kyiv: Vyd-vo TOV «NVP» INTERSERVIS», 716. Available at: http://bit.nau.edu.ua/vydannya/pidruchnyky/743
- Informatsionnye tehnologii. Metody zashchity. Sistemy menedzhmenta zashchity informatsii. Trebovaniya. ISO/IEC 27001:2005(E):ISO/MEK.
- Isazadeh, A., Lamb, D. A., MacEwen, G. H. (1996). Behavioral views for software requirements engineering. Proceedings IEEE Symposium and Workshop on Engineering of Computer-Based Systems. doi: https://doi.org/10.1109/ecbs.1996.494542
- Harel, D. (1987). Statecharts: a visual formalism for complex systems. Science of Computer Programming, 8 (3), 231–274. doi: https://doi.org/10.1016/0167-6423(87)90035-9
- von Solms, R. (1998). Information security management (3): the Code of Practice for Information Security Management (BS 7799). Information Management & Computer Security, 6 (5), 224–225. doi: https://doi.org/10.1108/09685229810240158
- Buchyk, S. S., Shalaev, V. A. (2017). The analysis instrumental methods of identification of risks of information security information and telecommunication systems. Science-Based Technologies, 35 (3). doi: https://doi.org/10.18372/2310-5461.35.11841
- Dombrovskyi, V. A., Kryzhanivskyi, I. M., Matskiv, R. S., Myhovych, F. M., Nemish, V. M., Okrepkyi, B. S. et al. (2003). Vyshcha matematyka. Ternopil: Vydavnytstvo Karpiuka, 480. Available at: http://dspace.wunu.edu.ua/bitstream/316497/612/1/vm_pidr.pdf
- Zubenko, V. V., Shkilniak, S. S. (2020). Osnovy matematychnoi lohiky. Kyiv: NUBiP Ukrainy, 102. Available at: http://csc.knu.ua/media/filer_public/3b/80/3b805f5a-fb43-4249-b587-f13852e8ba37/osnovy_mat_logyky_posibn_020620.pdf
- Bokan, B., Santos, J. (2022). Threat Modeling for Enterprise Cybersecurity Architecture. 2022 Systems and Information Engineering Design Symposium (SIEDS). doi: https://doi.org/10.1109/sieds55548.2022.9799322
- Kiran, A., Dharanikota, S., Basava, A. (2019). Blockchain based Data Access Control using Smart Contracts. TENCON 2019 - 2019 IEEE Region 10 Conference (TENCON). doi: https://doi.org/10.1109/tencon.2019.8929451
- Peiris, C., Pillai, B., Kudrati, A. (2021). AWS Cloud Threat Prevention Framework. Threat Hunting in the Cloud: Defending AWS, Azure and Other Cloud Platforms Against Cyberattacks. Wiley, 243–319.
- Tekinerdogan, B., Ozcan, K., Yagiz, S., Yakin, I. (2021). Model-Based Development of Design Basis Threat for Physical Protection Systems. 2021 IEEE International Symposium on Systems Engineering (ISSE). doi: https://doi.org/10.1109/isse51541.2021.9582528
- Pidvyshenna, N. V., Kubyshyna, N. S. (2015). The quality management of productsin industrial enterprises. Efektyvna ekonomika, 11. Available at: https://ela.kpi.ua/bitstream/123456789/12600/1/2013_5_Pidvyshenna.pdf
- Kalashnikova, Kh. I. (2023). Upravlinnia yakistiu. Kharkiv: KhNUMH im. Beketova, 138. Available at: https://files.znu.edu.ua/files/Bibliobooks/Inshi72/0052415.pdf
Downloads
Published
How to Cite
Issue
Section
License
Copyright (c) 2023 Vladymyr Lutsenko, Dmytro Progonov

This work is licensed under a Creative Commons Attribution 4.0 International License.
The consolidation and conditions for the transfer of copyright (identification of authorship) is carried out in the License Agreement. In particular, the authors reserve the right to the authorship of their manuscript and transfer the first publication of this work to the journal under the terms of the Creative Commons CC BY license. At the same time, they have the right to conclude on their own additional agreements concerning the non-exclusive distribution of the work in the form in which it was published by this journal, but provided that the link to the first publication of the article in this journal is preserved.
A license agreement is a document in which the author warrants that he/she owns all copyright for the work (manuscript, article, etc.).
The authors, signing the License Agreement with TECHNOLOGY CENTER PC, have all rights to the further use of their work, provided that they link to our edition in which the work was published.
According to the terms of the License Agreement, the Publisher TECHNOLOGY CENTER PC does not take away your copyrights and receives permission from the authors to use and dissemination of the publication through the world's scientific resources (own electronic resources, scientometric databases, repositories, libraries, etc.).
In the absence of a signed License Agreement or in the absence of this agreement of identifiers allowing to identify the identity of the author, the editors have no right to work with the manuscript.
It is important to remember that there is another type of agreement between authors and publishers – when copyright is transferred from the authors to the publisher. In this case, the authors lose ownership of their work and may not use it in any way.








