Construction of a network intrusion detection system based on a convolutional neural network and a bidirectional gated recurrent unit with attention mechanism
DOI:
https://doi.org/10.15587/1729-4061.2024.305685Keywords:
deep learning, combined model, network intrusion detection systems, attention mechanismAbstract
The object of this study is the process of recognizing intrusions in computer networks. Network intrusion detection systems (NIDS) have become an important area of research as they are used to protect computer systems from hacker attacks. Deep learning is becoming increasingly popular for detecting and classifying malicious network traffic, including for building NIDS.
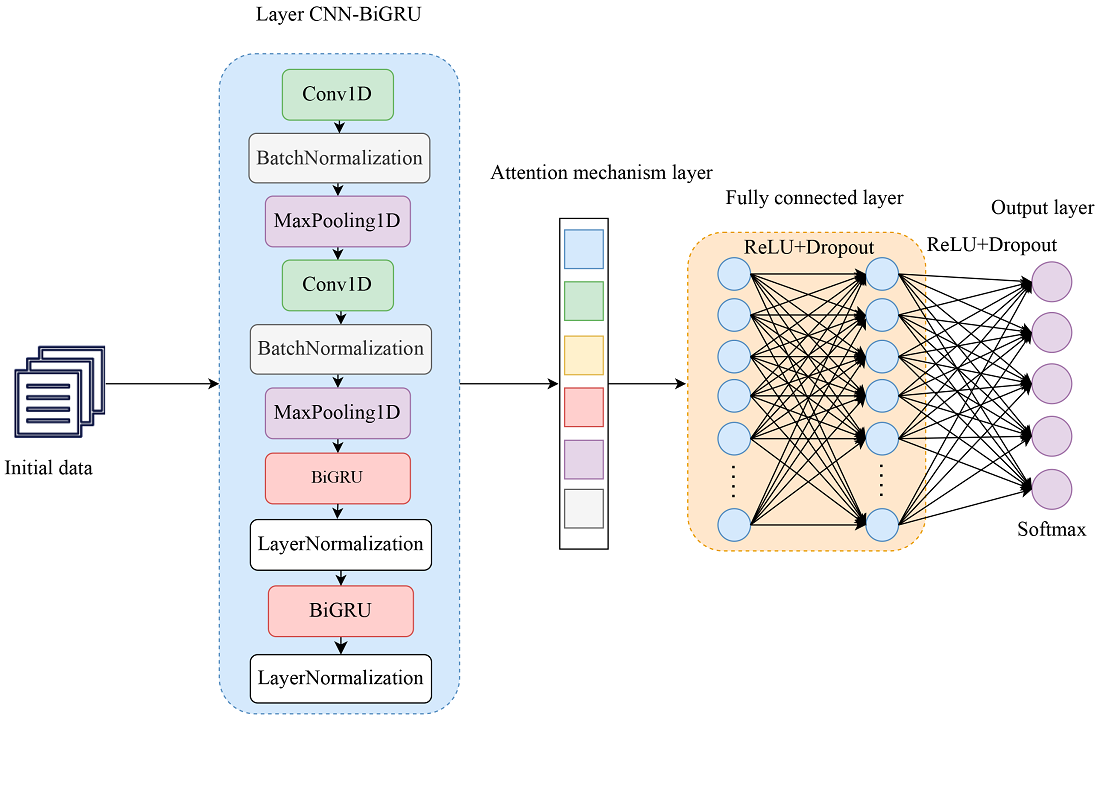
In this paper, we propose a network intrusion detection model CNN-BiGRU-Attention based on a time-based approach to deep learning using the attention mechanism. The main goal of the study is to build an effective combined deep learning model that can detect various network cyber threats.
A 1D convolutional neural network is implemented to extract high-level representations of intrusion information features. A bidirectional gated recurrent unit (BiGRU) with an attention mechanism for traffic data classification has been designed. The attention mechanism plays a key role in the constructed model as it allows the system to focus only on important aspects of network traffic and allows the model to adapt to new types of threats.
The results of the study show that using a combination of CNN and BiGRU with the attention mechanism speeds up and improves the process of classifying network attacks. On the NSL-KDD and UNSW-NB15 training datasets, the model shows an accuracy of 99.81 % and 97.80 %. On the NSL-KDD and UNSW-NB15 test datasets, the model demonstrates 82.16 % and 97.72 % accuracy.
The proposed NIDS model will be considered for implementation in a real-time corporate network security system.
In general, the results of the study provide a new perspective on improving the performance of NIDS and are quite relevant in terms of using attention mechanisms to classify network traffic
References
- Boukhalfa, A., Abdellaoui, A., Hmina, N., Chaoui, H. (2020). LSTM deep learning method for network intrusion detection system. International Journal of Electrical and Computer Engineering (IJECE), 10 (3), 3315. https://doi.org/10.11591/ijece.v10i3.pp3315-3322
- Ahmad, Z., Shahid Khan, A., Wai Shiang, C., Abdullah, J., Ahmad, F. (2020). Network intrusion detection system: A systematic study of machine learning and deep learning approaches. Transactions on Emerging Telecommunications Technologies, 32 (1). https://doi.org/10.1002/ett.4150
- Kumar, S., Gupta, S., Arora, S. (2021). Research Trends in Network-Based Intrusion Detection Systems: A Review. IEEE Access, 9, 157761–157779. https://doi.org/10.1109/access.2021.3129775
- Aldweesh, A., Derhab, A., Emam, A. Z. (2020). Deep learning approaches for anomaly-based intrusion detection systems: A survey, taxonomy, and open issues. Knowledge-Based Systems, 189, 105124. https://doi.org/10.1016/j.knosys.2019.105124
- Thirimanne, S. P., Jayawardana, L., Yasakethu, L., Liyanaarachchi, P., Hewage, C. (2022). Deep Neural Network Based Real-Time Intrusion Detection System. SN Computer Science, 3 (2). https://doi.org/10.1007/s42979-022-01031-1
- Qazi, E. U. H., Almorjan, A., Zia, T. (2022). A One-Dimensional Convolutional Neural Network (1D-CNN) Based Deep Learning System for Network Intrusion Detection. Applied Sciences, 12 (16), 7986. https://doi.org/10.3390/app12167986
- Zhang, J., Ling, Y., Fu, X., Yang, X., Xiong, G., Zhang, R. (2020). Model of the intrusion detection system based on the integration of spatial-temporal features. Computers & Security, 89, 101681. https://doi.org/10.1016/j.cose.2019.101681
- Rajesh Kanna, P., Santhi, P. (2021). Unified Deep Learning approach for Efficient Intrusion Detection System using Integrated Spatial–Temporal Features. Knowledge-Based Systems, 226, 107132. https://doi.org/10.1016/j.knosys.2021.107132
- Khan, F. A., Gumaei, A., Derhab, A., Hussain, A. (2019). TSDL: A Two-Stage Deep Learning Model for Efficient Network Intrusion Detection. IEEE Access, 7, 30373–30385. https://doi.org/10.1109/access.2019.2899721
- Binbusayyis, A., Vaiyapuri, T. (2021). Unsupervised deep learning approach for network intrusion detection combining convolutional autoencoder and one-class SVM. Applied Intelligence, 51 (10), 7094–7108. https://doi.org/10.1007/s10489-021-02205-9
- Hnamte, V., Hussain, J. (2023). DCNNBiLSTM: An Efficient Hybrid Deep Learning-Based Intrusion Detection System. Telematics and Informatics Reports, 10, 100053. https://doi.org/10.1016/j.teler.2023.100053
- Sinha, J., Manollas, M. (2020). Efficient Deep CNN-BiLSTM Model for Network Intrusion Detection. Proceedings of the 2020 3rd International Conference on Artificial Intelligence and Pattern Recognition. https://doi.org/10.1145/3430199.3430224
- Cao, B., Li, C., Song, Y., Fan, X. (2022). Network Intrusion Detection Technology Based on Convolutional Neural Network and BiGRU. Computational Intelligence and Neuroscience, 2022, 1–20. https://doi.org/10.1155/2022/1942847
- Gu, J., Wang, Z., Kuen, J., Ma, L., Shahroudy, A., Shuai, B. et al. (2018). Recent advances in convolutional neural networks. Pattern Recognition, 77, 354–377. https://doi.org/10.1016/j.patcog.2017.10.013
- Song, Y., Luktarhan, N., Shi, Z., Wu, H. (2023). TGA: A Novel Network Intrusion Detection Method Based on TCN, BiGRU and Attention Mechanism. Electronics, 12 (13), 2849. https://doi.org/10.3390/electronics12132849
- Li, X. (2023). CNN-GRU model based on attention mechanism for large-scale energy storage optimization in smart grid. Frontiers in Energy Research, 11. https://doi.org/10.3389/fenrg.2023.1228256
- Yu, X., Li, T., Hu, A. (2020). Time-series Network Anomaly Detection Based on Behaviour Characteristics. 2020 IEEE 6th International Conference on Computer and Communications (ICCC). https://doi.org/10.1109/iccc51575.2020.9345249
- Liu, X., Liu, J. (2021). Malicious traffic detection combined deep neural network with hierarchical attention mechanism. Scientific Reports, 11 (1). https://doi.org/10.1038/s41598-021-91805-z
- Huang, Y., Chen, J., Zheng, S., Xue, Y., Hu, X. (2021). Hierarchical multi-attention networks for document classification. International Journal of Machine Learning and Cybernetics, 12 (6), 1639–1647. https://doi.org/10.1007/s13042-020-01260-x x
- Nikitenko, A. (2023). Nabory danykh dlia stvorennia system vyiavlennia merezhevykh vtorhnen z vykorystanniam neironnykh merezh. Materialy XLI naukovo-tekhnichnoi konferentsiyi molodykh vchenykh ta spetsialistiv Instytutu problem modeliuvannia v enerhetytsi im. H.Ye. Pukhova NAN Ukrainy, 104–106. Available at: https://ipme.kiev.ua/wp-content/uploads/2023/05/%D0%9C%D0%B0%D1%82%D0%B5%D1%80%D1%96%D0%B0%D0%BB%D0%B8-%D0%BA%D0%BE%D0%BD%D1%84%D0%B5%D1%80%D0%B5%D0%BD%D1%86%D1%96%D1%97-2023.pdf
- The UNSW-NB15 Dataset. Available at: https://research.unsw.edu.au/projects/unsw-nb15-dataset
- Nikitenko, A. (2023). Network intrusion detection systems based on deep learning neural networks. Naukovi pratsi DonNTU. Seriya “Informatyka, kibernetyka ta obchysliuvalna tekhnika”, 2 (37), 15–21.
- ISCX NSL-KDD dataset 2009. Available at: https://www.unb.ca/cic/datasets/nsl.html
- Xiao, Y., Xiao, X. (2019). An Intrusion Detection System Based on a Simplified Residual Network. Information, 10 (11), 356. https://doi.org/10.3390/info10110356
- Cao, B., Li, C., Song, Y., Qin, Y., Chen, C. (2022). Network Intrusion Detection Model Based on CNN and GRU. Applied Sciences, 12 (9), 4184. https://doi.org/10.3390/app12094184
- Ren, K., Yuan, S., Zhang, C., Shi, Y., Huang, Z. (2023). CANET: A hierarchical CNN-Attention model for Network Intrusion Detection. Computer Communications, 205, 170–181. https://doi.org/10.1016/j.comcom.2023.04.018
- Marir, N., Wang, H., Feng, G., Li, B., Jia, M. (2018). Distributed Abnormal Behavior Detection Approach Based on Deep Belief Network and Ensemble SVM Using Spark. IEEE Access, 6, 59657–59671. https://doi.org/10.1109/access.2018.2875045
Downloads
Published
How to Cite
Issue
Section
License
Copyright (c) 2024 Andrii Nikitenko, Yevhen Bashkov

This work is licensed under a Creative Commons Attribution 4.0 International License.
The consolidation and conditions for the transfer of copyright (identification of authorship) is carried out in the License Agreement. In particular, the authors reserve the right to the authorship of their manuscript and transfer the first publication of this work to the journal under the terms of the Creative Commons CC BY license. At the same time, they have the right to conclude on their own additional agreements concerning the non-exclusive distribution of the work in the form in which it was published by this journal, but provided that the link to the first publication of the article in this journal is preserved.
A license agreement is a document in which the author warrants that he/she owns all copyright for the work (manuscript, article, etc.).
The authors, signing the License Agreement with TECHNOLOGY CENTER PC, have all rights to the further use of their work, provided that they link to our edition in which the work was published.
According to the terms of the License Agreement, the Publisher TECHNOLOGY CENTER PC does not take away your copyrights and receives permission from the authors to use and dissemination of the publication through the world's scientific resources (own electronic resources, scientometric databases, repositories, libraries, etc.).
In the absence of a signed License Agreement or in the absence of this agreement of identifiers allowing to identify the identity of the author, the editors have no right to work with the manuscript.
It is important to remember that there is another type of agreement between authors and publishers – when copyright is transferred from the authors to the publisher. In this case, the authors lose ownership of their work and may not use it in any way.








