Comprehensive methodology for estimating information safety at enterprises of electroenergy system under the conditions of digital coherence
DOI:
https://doi.org/10.15587/1729-4061.2025.327159Keywords:
energy enterprises, information threats, information risks, indicators of information security, digital coherence, methodology for assessing information securityAbstract
The object of this study is the process of assessing the information security of enterprises within an electric power system at the economy’s micro-level under the conditions of digital coherence.
The work solves the task to devise a comprehensive and adaptive approach to assessing information security, taking into account modern challenges associated with the integration of digital systems. The main feature is that the methodology enables to analyze the relationships between infrastructure components, taking into account digital coherence, which makes it possible to improve the accuracy of risk assessment and the effectiveness of information security management.
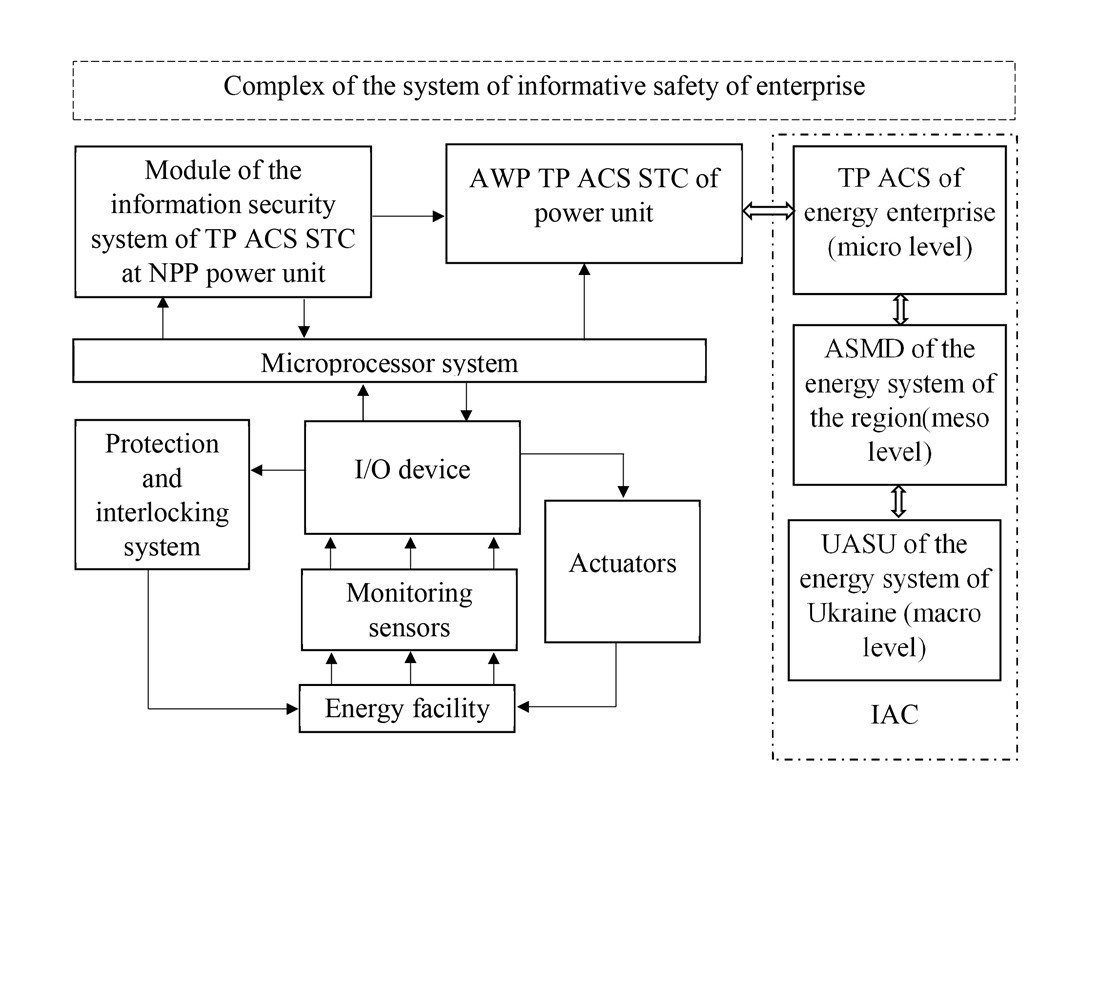
The devised methodology is based on eight interconnected stages, which include the integration of indicators, assessment of the interaction of system components, and monitoring changes in information security indicators in real time. This allows enterprises to respond to threats in a timely manner, minimizing risks.
A computational algorithm has been developed that monitors the dynamics of changes in information security indicators, which contributes to making timely management decisions.
The practical application of the methodology has been justified by scenarios of its integration into the work of energy industry enterprises. Testing at the power unit of the Zaporizhzhia Nuclear Power Plant confirmed its effectiveness, providing an economic effect of about USD 90 thousand. The methodology could be applied at different levels of the economy and adapted to the needs of specific enterprises, including integration into existing monitoring and management systems.
The results demonstrate the uniqueness of the proposed approach due to its complexity, adaptability, and practical significance, which makes the methodology an effective tool for assessing information security in the context of digital coherence
References
- Kirilchuk, S., Reutov, V., Nalivaychenko, E., Shevchenko, E., Yaroshenko, A. (2022). Ensuring the security of an automated information system in a regional innovation cluster. Transportation Research Procedia, 63, 607–617. https://doi.org/10.1016/j.trpro.2022.06.054
- Chang, H. H., Wong, K. H., Lee, H. C. (2022). Peer privacy protection motivation and action on social networking sites: Privacy self-efficacy and information security as moderators. Electronic Commerce Research and Applications, 54, 101176. https://doi.org/10.1016/j.elerap.2022.101176
- Taherdoost, H. (2022). Cybersecurity vs. Information Security. Procedia Computer Science, 215, 483–487. https://doi.org/10.1016/j.procs.2022.12.050
- Alraja, M. N., Butt, U. J., Abbod, M. (2023). Information security policies compliance in a global setting: An employee’s perspective. Computers & Security, 129, 103208. https://doi.org/10.1016/j.cose.2023.103208
- Tolah, A., Furnell, S. M., Papadaki, M. (2021). An empirical analysis of the information security culture key factors framework. Computers & Security, 108, 102354. https://doi.org/10.1016/j.cose.2021.102354
- Hadlington, L., Binder, J., Stanulewicz, N. (2021). Exploring role of moral disengagement and counterproductive work behaviours in information security awareness. Computers in Human Behavior, 114, 106557. https://doi.org/10.1016/j.chb.2020.106557
- Andersson, A., Hedström, K., Karlsson, F. (2022). “Standardizing information security – a structurational analysis.” Information & Management, 59 (3), 103623. https://doi.org/10.1016/j.im.2022.103623
- Kang, M., Miller, A., Jang, K., Kim, H. (2022). Firm performance and information security technology intellectual property. Technological Forecasting and Social Change, 181, 121735. https://doi.org/10.1016/j.techfore.2022.121735
- Antunes, M., Maximiano, M., Gomes, R. (2022). A Customizable Web Platform to Manage Standards Compliance of Information Security and Cybersecurity Auditing. Procedia Computer Science, 196, 36–43. https://doi.org/10.1016/j.procs.2021.11.070
- Ali, S. E. A., Lai, F.-W., Dominic, P. D. D., Brown, N. J., Lowry, P. B. B., Ali, R. F. (2021). Stock market reactions to favorable and unfavorable information security events: A systematic literature review. Computers & Security, 110, 102451. https://doi.org/10.1016/j.cose.2021.102451
- Gebremeskel, B. K., Jonathan, G. M., Yalew, S. D. (2023). Information Security Challenges During Digital Transformation. Procedia Computer Science, 219, 44–51. https://doi.org/10.1016/j.procs.2023.01.262
- Tendikov, N., Rzayeva, L., Saoud, B., Shayea, I., Azmi, M. H., Myrzatay, A., Alnakhli, M. (2024). Security Information Event Management data acquisition and analysis methods with machine learning principles. Results in Engineering, 22, 102254. https://doi.org/10.1016/j.rineng.2024.102254
- Razikin, K., Soewito, B. (2022). Cybersecurity decision support model to designing information technology security system based on risk analysis and cybersecurity framework. Egyptian Informatics Journal, 23 (3), 383–404. https://doi.org/10.1016/j.eij.2022.03.001
- Prokhorova, V., Protsenko, V., Bezuglaya, Y., Us, J. (2018). The optimization algorithm for the directions of influence of risk factors on the system that manages the potential of machine-building enterprises. Eastern-European Journal of Enterprise Technologies, 4 (1 (94)), 6–13. https://doi.org/10.15587/1729-4061.2018.139513
- Shibaeva, N., Baban, T., Prokhorova, V., Karlova, O., Girzheva, O., Krutko, M. (2019). Methodological bases of estimating the efficiency of organizational and economic mechanism of regulatory policy in agriculture. Global Journal of Environmental Science and Management, 5, 160–171. https://doi.org/10.22034/gjesm.2019.05.SI.18
- Babenko, V., Baksalova, O., Prokhorova, V., Dykan, V., Ovchynnikova, V., Chobitok, V. (2021). Information And Consulting Service Using In The Organization Of Personnel Management. Studies of Applied Economics, 38 (4). https://doi.org/10.25115/eea.v38i4.3999
- Iarmosh, O., Prokhorova, V., Shcherbyna, I., Kashaba, O., Slastianykova, K. (2021). Innovativeness of the creative economy as a component of the Ukrainian and the world sustainable development strategy. IOP Conference Series: Earth and Environmental Science, 628 (1), 012035. https://doi.org/10.1088/1755-1315/628/1/012035
- Budanov, P., Oliinyk, Y., Cherniuk, A., Brovko, K. (2024). Dynamic Fractal Cluster Model of Informational Space Technological Process of Power Station. Information Technology for Education, Science, and Technics, 141–155. https://doi.org/10.1007/978-3-031-71801-4_11
- Budanov, P., Brovko, K., Cherniuk, A., Vasyuchenko, P., Khomenko, V. (2018). Improving the reliability of informationcontrol systems at power generation facilities based on the fractalcluster theory. Eastern-European Journal of Enterprise Technologies, 2 (9 (92)), 4–12. https://doi.org/10.15587/1729-4061.2018.126427
- IAEA Annual Report 2022. IAEA. Available at: https://www.iaea.org/sites/default/files/publications/reports/2022/gc67-2.pdf
- IAEA Annual Report 2023. IAEA. Available at: https://www.iaea.org/sites/default/files/gc/gc68-2.pdf
- IAEA Year in Review 2024. IAEA. Available at: https://www.iaea.org/newscenter/news/iaea-year-in-review-2024
- Prokhorova, V., Budanov, M., Budanov, P., Zaitseva, A., Slastianykova, A. (2025). Devising a comprehensive methodology for estimating the economic efficiency of implementing an investment project for ensuring energy security of enterprises: organizational-economic aspect. Eastern-European Journal of Enterprise Technologies, 1 (13 (133)), 59–68. https://doi.org/10.15587/1729-4061.2025.321965
- Bondar-Pіdhurska, O. V., Khomenko, I. I. (2022). Scientific and Methodological Principles of Assessing the Efficiency of the Information Security Process Management of Small and Medium-Sized Businesses: Cybersecurity and Intellectual Property. The Problems of Economy, 2 (52), 108–116. https://doi.org/10.32983/2222-0712-2022-2-108-116
Downloads
Published
How to Cite
Issue
Section
License
Copyright (c) 2025 Viktoriia Prokhorova, Oleksandr Budanov, Pavlo Budanov, Krystyna Slastianykova

This work is licensed under a Creative Commons Attribution 4.0 International License.
The consolidation and conditions for the transfer of copyright (identification of authorship) is carried out in the License Agreement. In particular, the authors reserve the right to the authorship of their manuscript and transfer the first publication of this work to the journal under the terms of the Creative Commons CC BY license. At the same time, they have the right to conclude on their own additional agreements concerning the non-exclusive distribution of the work in the form in which it was published by this journal, but provided that the link to the first publication of the article in this journal is preserved.
A license agreement is a document in which the author warrants that he/she owns all copyright for the work (manuscript, article, etc.).
The authors, signing the License Agreement with TECHNOLOGY CENTER PC, have all rights to the further use of their work, provided that they link to our edition in which the work was published.
According to the terms of the License Agreement, the Publisher TECHNOLOGY CENTER PC does not take away your copyrights and receives permission from the authors to use and dissemination of the publication through the world's scientific resources (own electronic resources, scientometric databases, repositories, libraries, etc.).
In the absence of a signed License Agreement or in the absence of this agreement of identifiers allowing to identify the identity of the author, the editors have no right to work with the manuscript.
It is important to remember that there is another type of agreement between authors and publishers – when copyright is transferred from the authors to the publisher. In this case, the authors lose ownership of their work and may not use it in any way.








