Devising a code-free method for detecting signs of informational-psychological influences in messages
DOI:
https://doi.org/10.15587/1729-4061.2025.342297Keywords:
informational-psychological operation, semantic network, LLM, prompt engineering, codeless analytics, AI, disinformationAbstract
This study investigates text messages that potentially contain signs of informational-psychological operations (IPSOs). The task addressed aims to solve the problem of detecting signs of IPSOs in the media space.
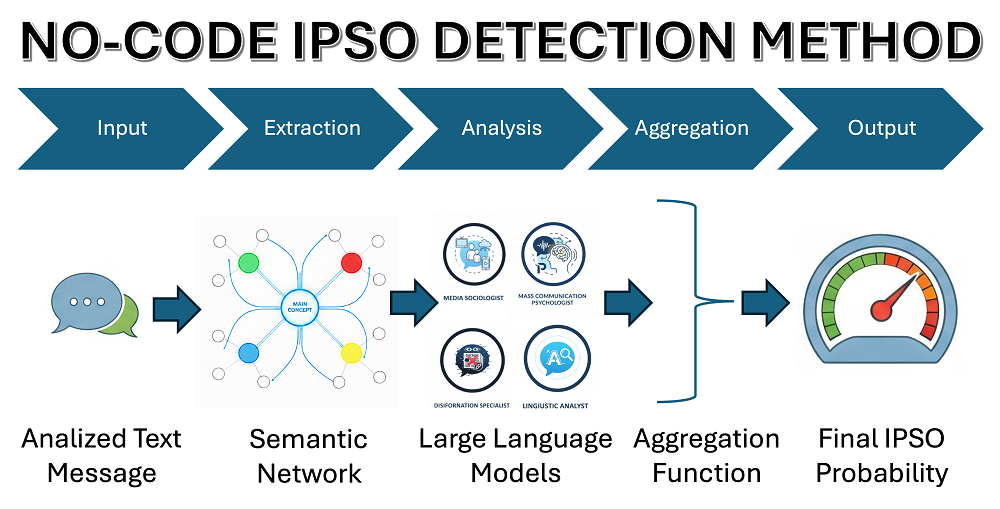
An innovative method for detecting such signs has been proposed, based on the construction and analysis of semantic networks and implemented without the use of program code by using large language models (LLMs). This makes it possible to generate formalized analytical queries to LLMs in the form of a code-free system based on the composition of structured prompts.
The method's unique feature is the parallel analysis of data from two sources of knowledge: internal and external. The internal one contains generalized IPSO patterns formed on the basis of a wide corpus of data. The external one includes verified examples of fake messages from social networks, news outlets, and archives of fact-checking organizations.
To improve the accuracy of analysis, semantic normalization of concepts is used, which employs embedded vectors to unify terminology, as well as comparison of causal paths in semantic networks to identify connections. The assessment of the probability of a message belonging to IPSO is formed by aggregating the results using a weighted average, which makes it possible to take into account semantic and structural similarity. An example of applying the method to the analysis of a disinformation message is given, demonstrating the ability to detect key signs of psychological influence: manipulative narratives, emotional loading, and cause-and-effect relationships.
The proposed method is flexible, reproducible, and accessible to researchers without programming skills, which makes it a valuable tool for monitoring information threats and analyzing disinformation in the context of information confrontations
References
- Hassan, S. U., Ahamed, J., Ahmad, K. (2022). Analytics of machine learning-based algorithms for text classification. Sustainable Operations and Computers, 3, 238–248. https://doi.org/10.1016/j.susoc.2022.03.001
- Zgurovsky, M., Lande, D., Dmytrenko, O., Yefremov, K., Boldak, A., Soboliev, A. (2023). Technological Principles of Using Media Content for Evaluating Social Opinion. System Analysis and Artificial Intelligence, 379–396. https://doi.org/10.1007/978-3-031-37450-0_22
- Ahmad Tamerin, A. S., Bakar, N. A. A., Hassan, N. H., Maarop, N. (2023). Counter-Narrative Cyber Security Model to Address the Issues of Cyber Terrorism. Open International Journal of Informatics, 11 (1), 96–113. https://doi.org/10.11113/oiji2023.11n1.30
- Lande, D., Strashnoy, L. (2025). Semantic AI Framework for Prompt Engineering. SSRN Electronic Journal. https://doi.org/10.2139/ssrn.5172867
- Lande, D., Strashnoy, L. (2025). Advanced Semantic Networking based on large language models. Kyiv: Engineering, 264.
- Kingdon, A. (2021). The Meme Is the Method: Examining the Power of the Image Within Extremist Propaganda. Researching Cybercrimes, 301–322. https://doi.org/10.1007/978-3-030-74837-1_15
- Guleria, P. (2024). NLP-based clinical text classification and sentiment analyses of complex medical transcripts using transformer model and machine learning classifiers. Neural Computing and Applications, 37 (1), 341–366. https://doi.org/10.1007/s00521-024-10482-x
- Dhiman, P., Kaur, A., Gupta, D., Juneja, S., Nauman, A., Muhammad, G. (2024). GBERT: A hybrid deep learning model based on GPT-BERT for fake news detection. Heliyon, 10 (16), e35865. https://doi.org/10.1016/j.heliyon.2024.e35865
- Piña-García, C. A. (2025). In-context learning for propaganda detection on Twitter Mexico using large language model meta AI. Telematics and Informatics Reports, 19, 100232. https://doi.org/10.1016/j.teler.2025.100232
- Liu, Z., Zhang, T., Yang, K., Thompson, P., Yu, Z., Ananiadou, S. (2024). Emotion detection for misinformation: A review. Information Fusion, 107, 102300. https://doi.org/10.1016/j.inffus.2024.102300
- Hu, L., Wei, S., Zhao, Z., Wu, B. (2022). Deep learning for fake news detection: A comprehensive survey. AI Open, 3, 133–155. https://doi.org/10.1016/j.aiopen.2022.09.001
- Aïmeur, E., Amri, S., Brassard, G. (2023). Fake news, disinformation and misinformation in social media: a review. Social Network Analysis and Mining, 13 (1). https://doi.org/10.1007/s13278-023-01028-5
- Barabash, O. V., Hryshchuk, R. V., Molodetska-Hrynchuk, K. V. (2018). Identification threats to the state information security in the text content of social networking services. Science-Based Technologies, 38 (2). https://doi.org/10.18372/2310-5461.38.12855
- Lande, D., Hyrda, V. (2024). Use of large language models to identify fake information. Collection “Information Technology and Security,” 12 (2), 236–242. https://doi.org/10.20535/2411-1031.2024.12.2.315743
- Strashnoy, L., Lande, D. (2024). Implementation Of The Concept Of A "Swarm Of Virtual Experts" In The Formation Of Semantic Networks In The Field Of Cybersecurity Based On Large Language Models. https://doi.org/10.2139/ssrn.4978924
- Hryshchuk, R., Molodetska, K., Syerov, Y. (2019). Method of improving the information security of virtual communities in social networking services. CEUR Workshop Proceedings. Available at: https://ceur-ws.org/Vol-2392/paper3.pdf
- Abels, A., Lenaerts, T. (2025). Wisdom from Diversity: Bias Mitigation Through Hybrid Human-LLM Crowds. Proceedings of the Thirty-Fourth International Joint Conference on Artificial Intelligence, 321–329. https://doi.org/10.24963/ijcai.2025/37
Downloads
Published
How to Cite
Issue
Section
License
Copyright (c) 2025 Dmytro Lande, Kostiantyn Yefremov, Artem Soboliev, Ivan Pyshnograiev

This work is licensed under a Creative Commons Attribution 4.0 International License.
The consolidation and conditions for the transfer of copyright (identification of authorship) is carried out in the License Agreement. In particular, the authors reserve the right to the authorship of their manuscript and transfer the first publication of this work to the journal under the terms of the Creative Commons CC BY license. At the same time, they have the right to conclude on their own additional agreements concerning the non-exclusive distribution of the work in the form in which it was published by this journal, but provided that the link to the first publication of the article in this journal is preserved.
A license agreement is a document in which the author warrants that he/she owns all copyright for the work (manuscript, article, etc.).
The authors, signing the License Agreement with TECHNOLOGY CENTER PC, have all rights to the further use of their work, provided that they link to our edition in which the work was published.
According to the terms of the License Agreement, the Publisher TECHNOLOGY CENTER PC does not take away your copyrights and receives permission from the authors to use and dissemination of the publication through the world's scientific resources (own electronic resources, scientometric databases, repositories, libraries, etc.).
In the absence of a signed License Agreement or in the absence of this agreement of identifiers allowing to identify the identity of the author, the editors have no right to work with the manuscript.
It is important to remember that there is another type of agreement between authors and publishers – when copyright is transferred from the authors to the publisher. In this case, the authors lose ownership of their work and may not use it in any way.








