Devising a method for integrated dataset formation and selecting a model for recognizing the technical condition of unmanned aerial vehicle
DOI:
https://doi.org/10.15587/1729-4061.2024.312217Keywords:
unmanned aerial vehicle, training dataset, machine learning, jamming effectiveness evaluationAbstract
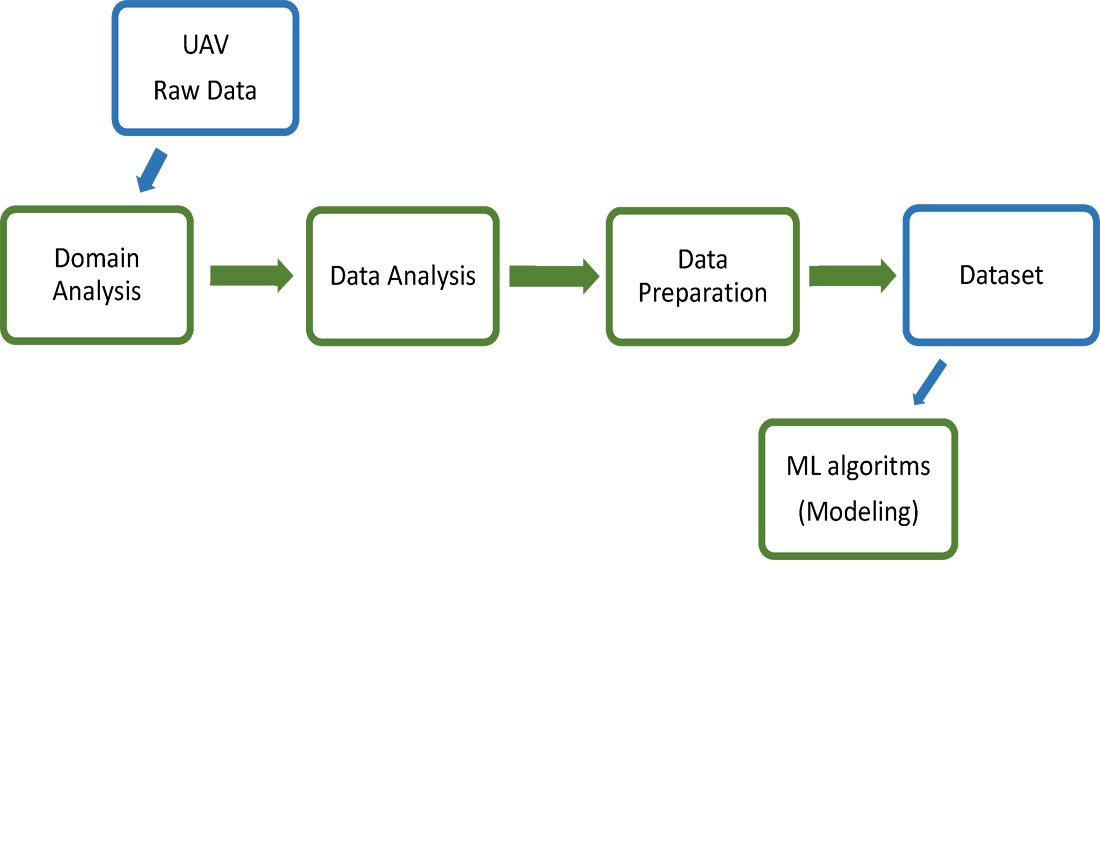
The object of this study is the process of forming a training dataset for diagnosing the technical condition of unmanned aerial vehicles (UAVs) using machine-learning algorithms. UAV flights are extremely important for various aspects of troop deployment. Combat UAV flights are performed under the influence of negative factors that cause flight special cases (FSC), which hinder the execution of combat missions, lead to mission failures, and result in the aircraft damage or loss. The available capabilities of autopilots are not enough for control under complex conditions, and in certain situations, the human operator cannot timely recognize a flight special case, including evaluation of the destructive impact of enemy’s electronic warfare systems on communication channels and operation of UAV. Therefore, the urgent issue is the intellectualization of onboard control systems, particularly towards recognizing the current technical state of UAV using artificial intelligence methods. To design such systems, labeled datasets are required. The procedure for forming datasets that consider the specificity of UAV construction and their combat use under adversarial conditions is not defined, necessitating the development of an appropriate method.
Based on the well-known CRISP-DM methodology, a method for dataset formation has been proposed for subsequent use in artificial intelligence systems that use various machine-learning methods.
This method differs from existing ones by considering the specificity of combat mission execution under adversarial conditions, which allowed for an 8.0 % increase in the accuracy of recognizing special cases in UAV flights by the onboard system. It also enabled timely detection of electronic warfare impacts on UAV and evaluation of the effectiveness of radio signal receivers jamming
References
- Petruk, S. M. (2017). Bezpilotni aviatsiyni kompleksy v zbroinykh konfliktakh ostannikh desiatyrich. Ozbroiennia Ta Viyskova Tekhnika, 13 (1), 44–49. https://doi.org/10.34169/2414-0651.2017.1(13).44-49
- Pavlenko, M., Tikhonov, I., Nikiforov, I. (2021). Recommendations for the efficient use of unmanned aerial vehicles in Joint Forces Operation. Science and Technology of the Air Force of Ukraine, 1 (42), 131–136. https://doi.org/10.30748/nitps.2021.42.17
- Gudla, C., Rana, S., Sung, A. (2018). Defense techniques against cyber attacks on unmanned aerial vehicles. Proceedings of the International Conference on Embedded Systems, Cyber-physical Systems, and Applications (ESCS). The Steering Committee of The World Congress in Computer Science, 110–116. Available at: https://www.researchgate.net/publication/328135272_Defense_Techniques_Against_Cyber_Attacks_on_Unmanned_Aerial_Vehicles
- Javaid, A. Y., Sun, W., Devabhaktuni, V. K., Alam, M. (2012). Cyber security threat analysis and modeling of an unmanned aerial vehicle system. 2012 IEEE Conference on Technologies for Homeland Security (HST). https://doi.org/10.1109/ths.2012.6459914
- Kerns, A. J., Shepard, D. P., Bhatti, J. A., Humphreys, T. E. (2014). Unmanned Aircraft Capture and Control Via GPS Spoofing. Journal of Field Robotics, 31 (4), 617–636. https://doi.org/10.1002/rob.21513
- Sedjelmaci, H., Senouci, S. M., Ansari, N. (2018). A Hierarchical Detection and Response System to Enhance Security Against Lethal Cyber-Attacks in UAV Networks. IEEE Transactions on Systems, Man, and Cybernetics: Systems, 48 (9), 1594–1606. https://doi.org/10.1109/tsmc.2017.2681698
- Mitchell, R., Ing-Ray Chen. (2014). Adaptive Intrusion Detection of Malicious Unmanned Air Vehicles Using Behavior Rule Specifications. IEEE Transactions on Systems, Man, and Cybernetics: Systems, 44 (5), 593–604. https://doi.org/10.1109/tsmc.2013.2265083
- Muniraj, D., Farhood, M. (2017). A framework for detection of sensor attacks on small unmanned aircraft systems. 2017 International Conference on Unmanned Aircraft Systems (ICUAS), 9333, 1189–1198. https://doi.org/10.1109/icuas.2017.7991465
- Zhou, Z., Liu, Y. (2021). A Smart Landing Platform With Data-Driven Analytic Procedures for UAV Preflight Safety Diagnosis. IEEE Access, 9, 154876–154891. https://doi.org/10.1109/access.2021.3128866
- Li, M., Li, G., Zhong, M. (2016). A data driven fault detection and isolation scheme for UAV flight control system. 2016 35th Chinese Control Conference (CCC). https://doi.org/10.1109/chicc.2016.7554425
- Gebrie, M. T. (2022). Digital Twin for UAV Anomaly Detection. The University of Oslo, 74. Available at: https://www.duo.uio.no/bitstream/handle/10852/93934/1/DTAnomally.pdf
- Liang, S., Zhang, S., Huang, Y., Zheng, X., Cheng, J., Wu, S. (2022). Data-driven fault diagnosis of FW-UAVs with consideration of multiple operation conditions. ISA Transactions, 126, 472–485. https://doi.org/10.1016/j.isatra.2021.07.043
- Yousefi, P., Fekriazgomi, H., Demir, M. A., Prevost, J. J., Jamshidi, M. (2018). Data-Driven Fault Detection of Un-Manned Aerial Vehicles Using Supervised Learning Over Cloud Networks. 2018 World Automation Congress (WAC). https://doi.org/10.23919/wac.2018.8430428
- Yang, T., Chen, J., Deng, H., Lu, Y. (2023). UAV Abnormal State Detection Model Based on Timestamp Slice and Multi-Separable CNN. Electronics, 12 (6), 1299. https://doi.org/10.3390/electronics12061299
- Perehuda, O., Rodionov, A., Bobunov, A. (2022). Faceted classification of occasions in flight for class 1 unmanned aerial vehicle. Science and Technology of the Air Force of Ukraine, 1 (46), 85–91. https://doi.org/10.30748/nitps.2022.46.12
- Mohd Selamat, S. A., Prakoonwit, S., Sahandi, R., Khan, W., Ramachandran, M. (2018). Big data analytics – A review of data‐mining models for small and medium enterprises in the transportation sector. WIREs Data Mining and Knowledge Discovery, 8 (3). https://doi.org/10.1002/widm.1238
- Chapman, P., Clinton, J., Kerber, R., Khabaza, T., Reinartz, T., Shearer, C. et al. (2000). CRISP-DM 1.0: Step-by-Step Data Mining Guide. CRISP-DM consortium. SPSS, 78. Available at: https://www.kde.cs.uni-kassel.de/wp-content/uploads/lehre/ws2012-13/kdd/files/CRISPWP-0800.pdf
- Plotnikova, V., Dumas, M., Milani, F. (2021). Adapting the CRISP-DM Data Mining Process: A Case Study in the Financial Services Domain. Research Challenges in Information Science, 55–71. https://doi.org/10.1007/978-3-030-75018-3_4
- Niakšu, O. (2015). CRISP Data Mining Methodology Extension for Medical Domain. Baltic J. Modern Computing. 3 (2), 92–109. Available at: https://www.bjmc.lu.lv/fileadmin/user_upload/lu_portal/projekti/bjmc/Contents/3_2_2_Niaksu.pdf
- Solarte, J. (2002). A proposed data mining methodology and its application to industrial engineering. University of Tennessee, 104. Available at: https://trace.tennessee.edu/cgi/viewcontent.cgi?article=3549&context=utk_gradthes
- Plotnikova, V., Dumas, M., Milani, F. (2020). Adaptations of data mining methodologies: a systematic literature review. PeerJ Computer Science, 6, e267. https://doi.org/10.7717/peerj-cs.267
- Kononova, K. (2020). Mashynne navchannia: metody ta modeli. Kharkiv: KhNU imeni V. N. Karazina, 301. Available at: https://moodle.znu.edu.ua/pluginfile.php/593075/mod_folder/intro/Базовий%20підручник_2%20%28Кононова%20К.%20Ю.%20Машинне%20навчання%20-%20методи%20та%20моделі%29.pdf
- Lykhach, O., Ugryumov, M., Shevchenko, D., Shmatkov, S. (2022). Anomaly detection methods in sample datasets when managing processes in systems by the state. Bulletin of V.N. Karazin Kharkiv National University, Series «Mathematical Modeling. Information Technology. Automated Control Systems», 53, 21–40. https://doi.org/10.26565/2304-6201-2022-53-03
- Subbotin, S. A. (2010). Kompleks harakteristik i kriteriev sravneniya obuchayuschih vyborok dlya resheniya zadach diagnostiki i raspoznavaniya obrazov. Matematicheskie mashiny i sistemy, 1 (1), 25–39. Available at: https://www.researchgate.net/publication/247158465_Kompleks_harakteristik_i_kriteriev_sravnenia_obucausih_vyborok_dla_resenia_zadac_diagnostiki_i_raspoznavania_obrazov
- Kavrin, D. А., Subbotin, S. A. (2018). The methods for quantitative solving the class imbalance problem. Radio Electronics, Computer Science, Control, 1 (44), 83–90. Available at: http://nbuv.gov.ua/UJRN/riu_2018_1_12
- Biloborodova, T., Koverha, M., Petrov, P., Lomakin, S., Krytska, Ya. (2021). Doslidzhennia metodiv vyrishennia problemy nezbalansovanykh danykh. Naukovi visti Dalivskoho universytetu, 21. https://doi.org/10.33216/2222-3428-2021-21-1
- Kovbasyuk, S., Osadchuk, R., Romanchuk, M., Naumchak, L. (2023). An approach to forming a prior dataset of neural network for processing digital aerial photos. Problems of construction, testing, application and operation of complex information systems, 23, 77–88. https://doi.org/10.46972/2076-1546.2022.23.06
- Bondyra, A., Ga̧sior, P., Gardecki, S., Kasiński, A. (2018). Development of the Sensory Network for the Vibration-based Fault Detection and Isolation in the Multirotor UAV Propulsion System. Proceedings of the 15th International Conference on Informatics in Control, Automation and Robotics. https://doi.org/10.5220/0006846801020109
- Sadhu, V., Anjum, K., Pompili, D. (2023). On-Board Deep-Learning-Based Unmanned Aerial Vehicle Fault Cause Detection and Classification via FPGAs. IEEE Transactions on Robotics, 39 (4), 3319–3331. https://doi.org/10.1109/tro.2023.3269380
- Abramov, N., Talalayev, A., Fralenko, V., Khachumov, V., Shishkin, O. (2017). The high–performance neural network system for monitoring of state and behavior of spacecraft subsystems by telemetry data. Program Systems: Theory and Applications, 8 (3), 109–131. https://doi.org/10.25209/2079-3316-2017-8-3-109-131
Downloads
Published
How to Cite
Issue
Section
License
Copyright (c) 2024 Oleksandr Perehuda, Andrii Rodionov, Dmytro Fedorchuk, Serhii Zhuravskyi, Mykola Konvisar, Taras Volynets, Vitalii Datsyk, Mykola Zakalad, Serhii Tsybulia, Taras Trysnyuk

This work is licensed under a Creative Commons Attribution 4.0 International License.
The consolidation and conditions for the transfer of copyright (identification of authorship) is carried out in the License Agreement. In particular, the authors reserve the right to the authorship of their manuscript and transfer the first publication of this work to the journal under the terms of the Creative Commons CC BY license. At the same time, they have the right to conclude on their own additional agreements concerning the non-exclusive distribution of the work in the form in which it was published by this journal, but provided that the link to the first publication of the article in this journal is preserved.
A license agreement is a document in which the author warrants that he/she owns all copyright for the work (manuscript, article, etc.).
The authors, signing the License Agreement with TECHNOLOGY CENTER PC, have all rights to the further use of their work, provided that they link to our edition in which the work was published.
According to the terms of the License Agreement, the Publisher TECHNOLOGY CENTER PC does not take away your copyrights and receives permission from the authors to use and dissemination of the publication through the world's scientific resources (own electronic resources, scientometric databases, repositories, libraries, etc.).
In the absence of a signed License Agreement or in the absence of this agreement of identifiers allowing to identify the identity of the author, the editors have no right to work with the manuscript.
It is important to remember that there is another type of agreement between authors and publishers – when copyright is transferred from the authors to the publisher. In this case, the authors lose ownership of their work and may not use it in any way.








