Розробка методу багатокритеріальної оцінки ієрархічних систем
DOI:
https://doi.org/10.15587/1729-4061.2025.331018Ключові слова:
системи показників, дерево вразливостей, алгоритм зграї пінгвінів, дестабілізуючі фактори, угруповання військ (сил)Анотація
Багатокритеріальна оцінка має беззаперечні переваги перед однокритеріальними методами оцінки. Об’єктом дослідження є ієрархічні системи. Предметом дослідження є процес багатокритеріального оцінювання стану ієрархічних систем. Запропоновано метод багатокритеріальної оцінки ієрархічних систем. Оригінальність методу полягає у використанні додаткових удосконалених процедур, які дозволяють:
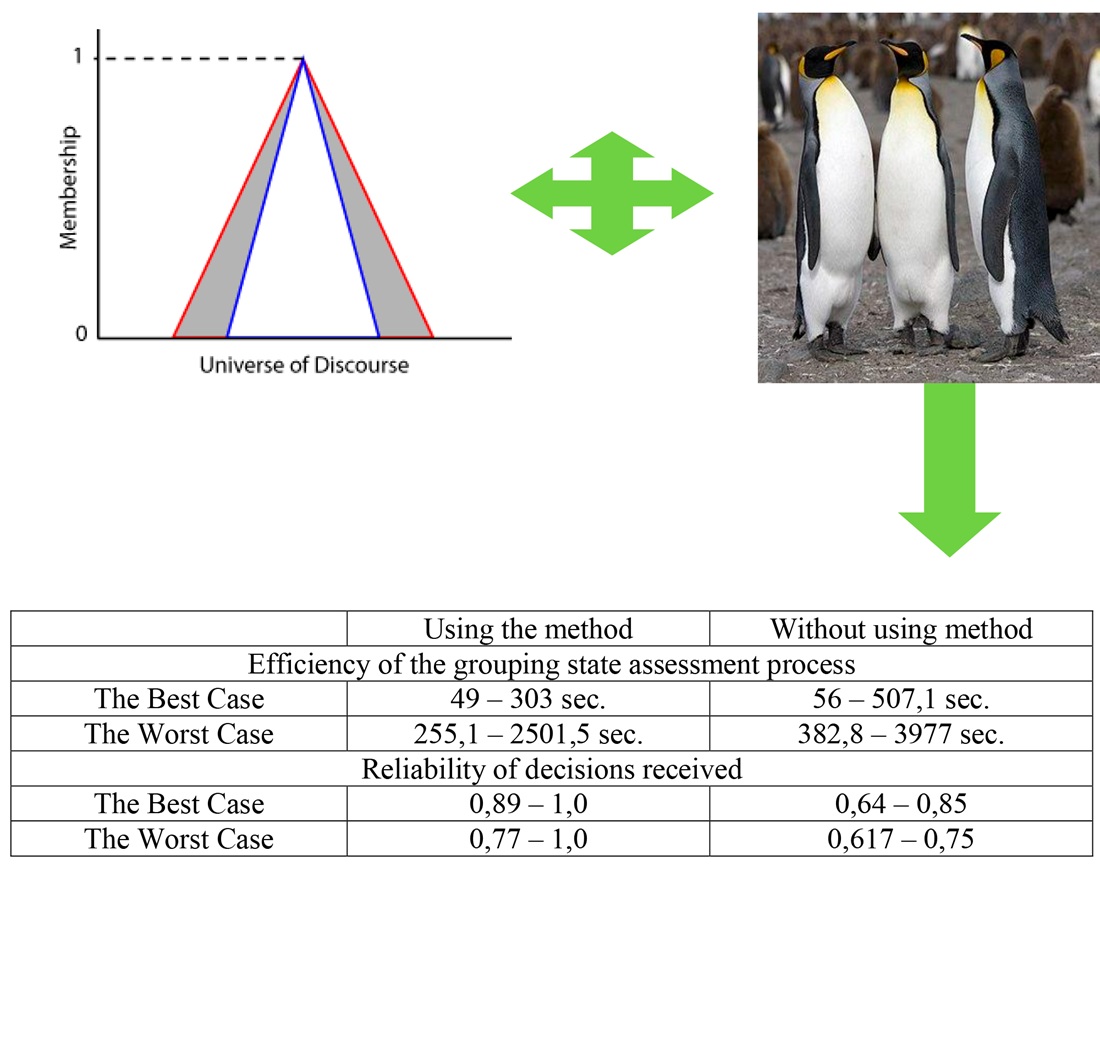
– здійснювати верифікацію введених даних та уточнення зв’язків між елементами ієрархічної системи за допомого удосконаленого алгоритму зграї пінгвінів. Зазначене дозволяє мінімізувати похибку введення не коректних даних для роботи про стан оперативного угруповання військ (сил);
– описати зовнішні та внутрішні фактори які впливають на ієрархічну систему, що підлягає багатокритеріальному оцінюванню за допомогою нечітких когнітивних моделей;
– провести адаптацію під тип ієрархічної системи за рахунок багаторівневої адаптації системи показників та критеріїв оцінювання;
– знизити невизначеність за допомогою інтервальної піфагорійської нечіткої множини, чим досягається підвищення достовірності багатокритеріального оцінювання стану ієрархічних систем;
– визначити найбільш вразливі елементи ієрархічної системи за допомогою дерева відмов;
– адаптувати вид функції належності в залежності від наявних обчислювальних ресурсів системи, чим забезпечується адаптація під наявні обчислювальні ресурси.
Приведений приклад використання запропонованого методу для багатокритеріальної оцінки оперативного угруповання військ (сил). Запропонований метод забезпечує підвищення точності та оперативності в середньому на 35%, при забезпеченні високої збіжності отриманих результатів на рівні 93.17%
Посилання
- Sova, O., Radzivilov, H., Shyshatskyi, A., Shvets, P., Tkachenko, V., Nevhad, S. et al. (2022). Development of a method to improve the reliability of assessing the condition of the monitoring object in special-purpose information systems. Eastern-European Journal of Enterprise Technologies, 2 (3 (116)), 6–14. https://doi.org/10.15587/1729-4061.2022.254122
- Dudnyk, V., Sinenko, Y., Matsyk, M., Demchenko, Y., Zhyvotovskyi, R., Repilo, I. et al. (2020). Development of a method for training artificial neural networks for intelligent decision support systems. Eastern-European Journal of Enterprise Technologies, 3 (2 (105)), 37–47. https://doi.org/10.15587/1729-4061.2020.203301
- Sova, O., Shyshatskyi, A., Salnikova, O., Zhuk, O., Trotsko, O., Hrokholskyi, Y. (2021). Development of a method for assessment and forecasting of the radio electronic environment. EUREKA: Physics and Engineering, 4, 30–40. https://doi.org/10.21303/2461-4262.2021.001940
- Pievtsov, H., Turinskyi, O., Zhyvotovskyi, R., Sova, O., Zvieriev, O., Lanetskii, B., Shyshatskyi, A. (2020). Development of an advanced method of finding solutions for neuro-fuzzy expert systems of analysis of the radioelectronic situation. EUREKA: Physics and Engineering, 4, 78–89. https://doi.org/10.21303/2461-4262.2020.001353
- Zuiev, P., Zhyvotovskyi, R., Zvieriev, O., Hatsenko, S., Kuprii, V., Nakonechnyi, O. et al. (2020). Development of complex methodology of processing heterogeneous data in intelligent decision support systems. Eastern-European Journal of Enterprise Technologies, 4 (9 (106)), 14–23. https://doi.org/10.15587/1729-4061.2020.208554
- Wang, J., Neil, M., Fenton, N. (2020). A Bayesian network approach for cybersecurity risk assessment implementing and extending the FAIR model. Computers & Security, 89, 101659. https://doi.org/10.1016/j.cose.2019.101659
- Matheu-García, S. N., Hernández-Ramos, J. L., Skarmeta, A. F., Baldini, G. (2019). Risk-based automated assessment and testing for the cybersecurity certification and labelling of IoT devices. Computer Standards & Interfaces, 62, 64–83. https://doi.org/10.1016/j.csi.2018.08.003
- Henriques de Gusmão, A. P., Mendonça Silva, M., Poleto, T., Camara e Silva, L., Cabral Seixas Costa, A. P. (2018). Cybersecurity risk analysis model using fault tree analysis and fuzzy decision theory. International Journal of Information Management, 43, 248–260. https://doi.org/10.1016/j.ijinfomgt.2018.08.008
- Folorunso, O., Mustapha, O. A. (2015). A fuzzy expert system to Trust-Based Access Control in crowdsourcing environments. Applied Computing and Informatics, 11 (2), 116–129. https://doi.org/10.1016/j.aci.2014.07.001
- Mohammad, A. (2020). Development of the concept of electronic government construction in the conditions of synergetic threats. Technology Audit and Production Reserves, 3 (2 (53)), 42–46. https://doi.org/10.15587/2706-5448.2020.207066
- Bodin, L. D., Gordon, L. A., Loeb, M. P., Wang, A. (2018). Cybersecurity insurance and risk-sharing. Journal of Accounting and Public Policy, 37 (6), 527–544. https://doi.org/10.1016/j.jaccpubpol.2018.10.004
- Cormier, A., Ng, C. (2020). Integrating cybersecurity in hazard and risk analyses. Journal of Loss Prevention in the Process Industries, 64, 104044. https://doi.org/10.1016/j.jlp.2020.104044
- Hoffmann, R., Napiórkowski, J., Protasowicki, T., Stanik, J. (2020). Risk based approach in scope of cybersecurity threats and requirements. Procedia Manufacturing, 44, 655–662. https://doi.org/10.1016/j.promfg.2020.02.243
- Perrine, K. A., Levin, M. W., Yahia, C. N., Duell, M., Boyles, S. D. (2019). Implications of traffic signal cybersecurity on potential deliberate traffic disruptions. Transportation Research Part A: Policy and Practice, 120, 58–70. https://doi.org/10.1016/j.tra.2018.12.009
- Promyslov, V. G., Semenkov, K. V., Shumov, A. S. (2019). A Clustering Method of Asset Cybersecurity Classification. IFAC-PapersOnLine, 52 (13), 928–933. https://doi.org/10.1016/j.ifacol.2019.11.313
- Zarreh, A., Saygin, C., Wan, H., Lee, Y., Bracho, A. (2018). A game theory based cybersecurity assessment model for advanced manufacturing systems. Procedia Manufacturing, 26, 1255–1264. https://doi.org/10.1016/j.promfg.2018.07.162
- Kosko, B. (1986). Fuzzy cognitive maps. International Journal of Man-Machine Studies, 24 (1), 65–75. https://doi.org/10.1016/s0020-7373(86)80040-2
- Koval, M., Sova, O., Shyshatskyi, A., Artabaiev, Y., Garashchuk, N., Yivzhenko, Y. et al. (2022). Improving the method for increasing the efficiency of decision-making based on bio-inspired algorithms. Eastern-European Journal of Enterprise Technologies, 6 (4 (120)), 6–13. https://doi.org/10.15587/1729-4061.2022.268621
- Maccarone, A. D., Brzorad, J. N., Stone, H. M. (2008). Characteristics And Energetics Of Great Egret And Snowy Egret Foraging Flights. Waterbirds, 31 (4), 541–549. https://doi.org/10.1675/1524-4695-31.4.541
- Litvinenko, O., Kashkevich, S., Shyshatskyi, A., Dmytriieva, O., Neronov, S., Plekhova, G. et al.; Shyshatskyi, A. (Ed.) (2024). Information and control systems: modelling and optimizations. Kharkiv: TECHNOLOGY CENTER PC, 180. https://doi.org/10.15587/978-617-8360-04-7
##submission.downloads##
Опубліковано
Як цитувати
Номер
Розділ
Ліцензія
Авторське право (c) 2025 Oleg Sova, Oleksandr Stanovskyi, Taras Hurskyi, Valentyn Olshanskyi, Oleksandr Volkov, Serhii Shostak, Vitalii Bezuhlyi, Hryhorii Tikhonov, Olena Chaikovska, Leonid Razarionov

Ця робота ліцензується відповідно до Creative Commons Attribution 4.0 International License.
Закріплення та умови передачі авторських прав (ідентифікація авторства) здійснюється у Ліцензійному договорі. Зокрема, автори залишають за собою право на авторство свого рукопису та передають журналу право першої публікації цієї роботи на умовах ліцензії Creative Commons CC BY. При цьому вони мають право укладати самостійно додаткові угоди, що стосуються неексклюзивного поширення роботи у тому вигляді, в якому вона була опублікована цим журналом, але за умови збереження посилання на першу публікацію статті в цьому журналі.
Ліцензійний договір – це документ, в якому автор гарантує, що володіє усіма авторськими правами на твір (рукопис, статтю, тощо).
Автори, підписуючи Ліцензійний договір з ПП «ТЕХНОЛОГІЧНИЙ ЦЕНТР», мають усі права на подальше використання свого твору за умови посилання на наше видання, в якому твір опублікований. Відповідно до умов Ліцензійного договору, Видавець ПП «ТЕХНОЛОГІЧНИЙ ЦЕНТР» не забирає ваші авторські права та отримує від авторів дозвіл на використання та розповсюдження публікації через світові наукові ресурси (власні електронні ресурси, наукометричні бази даних, репозитарії, бібліотеки тощо).
За відсутності підписаного Ліцензійного договору або за відсутністю вказаних в цьому договорі ідентифікаторів, що дають змогу ідентифікувати особу автора, редакція не має права працювати з рукописом.
Важливо пам’ятати, що існує і інший тип угоди між авторами та видавцями – коли авторські права передаються від авторів до видавця. В такому разі автори втрачають права власності на свій твір та не можуть його використовувати в будь-який спосіб.









