Design of a simulation tool for planning UAV mission success under combat constraints
DOI:
https://doi.org/10.15587/1729-4061.2025.340918Keywords:
UAV network simulation, cyber-physical security, malware, electronic countermeasuresAbstract
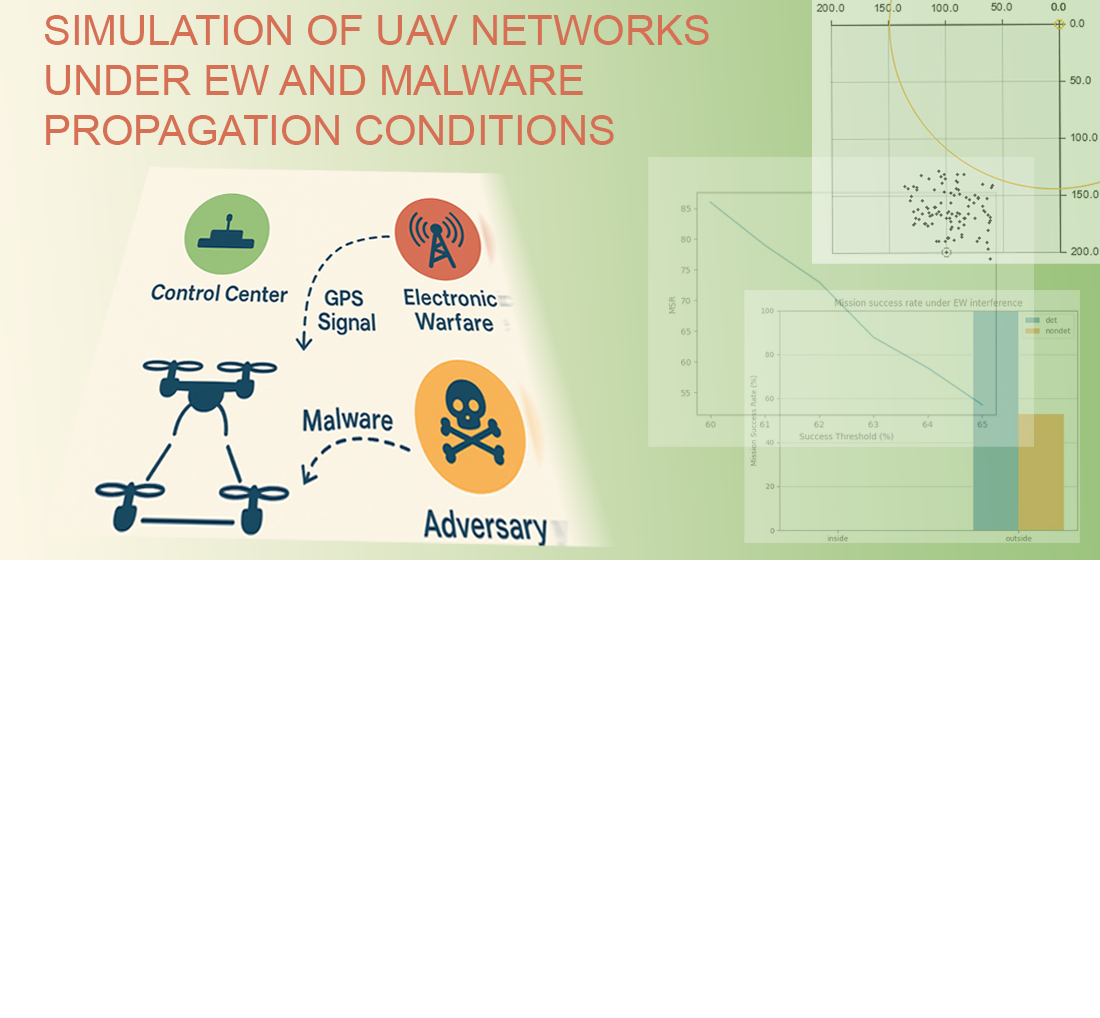
This study investigates unmanned aerial vehicle (UAV) networks operating under the influence of destructive and hostile factors. The study considers, among destructive factors, changes in signal power at the receiver side caused by distance and battery charge limitations. Among the hostile factors, cyber-physical threats have been examined, including those caused by electronic countermeasure (ECM) systems and malware-based attacks.
Algorithmic and software solutions have been developed to simulate the behavior of UAVs under such constraints. A special feature of the proposed model, in contrast to existing approaches, is that it integrates factors such as signal degradation caused by ECM systems and the dynamics of malware propagation within the network.
Scenarios include UAV behavior under jamming, the probabilistic spread of malware, and the switching of operational modes in response to threat exposure. The results were achieved by integrating a wide range of parameters, including device identifier, signal power, transmitter radius, transmission frequency, geolocation, task type, malware sensitivity, message handling queue, propagation delay, as well as movement speed. These features enable the model to realistically reproduce system behavior in uncertain and hostile environments, allowing both defensive and offensive security strategies to be explored. Devising appropriate operational scenarios is also possible.
The proposed software solution is characterized by the high level of detail in the simulation and the use of the Rust programming language, which ensures performance, modularity, and future extensibility. The solution reported here supports visualization of the behavior of up to 100 UAVs and more through both images and animations. It can be used for analyzing attack scenarios, designing robust UAV architectures, and prototyping offensive security tools. The source code is publicly available at GitHub repository, supporting practical usage and further research applications
References
- McNabb, M. (2025). Ukraine’s Trojan Horse Drones: A New Frontier in Cyber Warfare. DroneLife. Available at: https://dronelife.com/2025/04/10/ukraines-trojan-horse-drones-a-new-frontier-in-cyber-warfare/
- Yaacoub, J.-P., Noura, H., Salman, O., Chehab, A. (2020). Security analysis of drones systems: Attacks, limitations, and recommendations. Internet of Things, 11, 100218. https://doi.org/10.1016/j.iot.2020.100218
- Hartmann, K., Giles, K. (2016). UAV Exploitation: A New Domain for Cyber Power. 6 8th International Conference on Cyber Conflict. Tallinn, 205–221. Available at: https://ccdcoe.org/uploads/2018/10/Art-14-Assessing-the-Impact-of-Aviation-Security-on-Cyber-Power.pdf
- Abro, G., Zulkifli, S., Masood, R., Asirvadam, V., Laouiti, A. (2022). Comprehensive Review of UAV Detection, Security, and Communication Advancements to Prevent Threats. Drones, 6 (10), 284. https://doi.org/10.3390/drones6100284
- Riahi Manesh, M., Kaabouch, N. (2019). Cyber-attacks on unmanned aerial system networks: Detection, countermeasure, and future research directions. Computers & Security, 85, 386–401. https://doi.org/10.1016/j.cose.2019.05.003
- Drone Hacking: Exploitation and Vulnerabilities. Available at: https://spadok.org.ua/books/Drone+Hacking-+Exploitation+and+Vulnerabilities.pdf
- Throwback Attack: Keylogging virus infects U.S. drone fleet (2022). Control Engineering. Available at: https://www.controleng.com/throwback-attack-keylogging-virus-infects-u-s-drone-fleet/
- Zakharchenko, I., Tristan, A., Chornogor, N., Berdnik, P., Kalashnyk, G., Timochko, A. et al. (2022). Modeling of Object Monitoring Using 3D Cellular Automata. Problems of the Regional Energetics, 4 (56), 61–73. https://doi.org/10.52254/1857-0070.2022.4-56.06
- Song, Z., Zhang, H., Zhang, X., Zhang, F. (2019). Unmanned Aerial Vehicle Coverage Path Planning Algorithm Based on Cellular Automata. 2019 15th International Conference on Computational Intelligence and Security (CIS), 123–126. https://doi.org/10.1109/cis.2019.00034
- Ioannidis, K., Sirakoulis, G. Ch., Andreadis, I. (2011). A path planning method based on cellular automata for cooperative robots. Applied Artificial Intelligence, 25 (8), 721–745. https://doi.org/10.1080/08839514.2011.606767
- Adamatzky, A. I. (1996). Computation of shortest path in cellular automata. Mathematical and Computer Modelling, 23 (4), 105–113. https://doi.org/10.1016/0895-7177(96)00006-4
- Behring, C., Bracho, M., Castro, M., Moreno, J. A. (2001). An Algorithm for Robot Path Planning with Cellular Automata. Theory and Practical Issues on Cellular Automata, 11–19. https://doi.org/10.1007/978-1-4471-0709-5_2
- Xie, J., Chen, J. (2022). Multiregional Coverage Path Planning for Multiple Energy Constrained UAVs. IEEE Transactions on Intelligent Transportation Systems, 23 (10), 17366–17381. https://doi.org/10.1109/tits.2022.3160402
- Fedorova, A., Beliautsou, V., Zimmermann, A. (2022). Colored Petri Net Modelling and Evaluation of Drone Inspection Methods for Distribution Networks. Sensors, 22 (9), 3418. https://doi.org/10.3390/s22093418
- Xu, D., Borse, P., Altenburg, K., Nygard, K. (2006). A Petri Net Simulator for Self-organizing Systems. Proceedings of the 5th WSEAS Int. Conf. on Artificial Intelligence, Knowledge Engineering and Data Bases. Madrid, 31–35. Available at: https://www.researchgate.net/publication/234805596
- Gonçalves, P., Sobral, J., Ferreira, L. A. (2017). Unmanned aerial vehicle safety assessment modelling through petri Nets. Reliability Engineering & System Safety, 167, 383–393. https://doi.org/10.1016/j.ress.2017.06.021
- Wang, X., Guo, Y., Lu, N., He, P. (2023). UAV Cluster Behavior Modeling Based on Spatial-Temporal Hybrid Petri Net. Applied Sciences, 13 (2), 762. https://doi.org/10.3390/app13020762
- NS-3. Network Simulator. Available at: https://www.nsnam.org/
- OMNeT++. Available at: https://omnetpp.org/
- GAMA Platform. Available at: https://gama-platform.org/
- Nikolaiev, M., Novotarskyi, M. (2024). Comparative Review of Drone Simulators. Information, Computing and Intelligent Systems, 4, 79–98. https://doi.org/10.20535/2786-8729.4.2024.300614
- GPS Jamming, Spoofing and Hacking (2025). NorthStandard. Available at: https://north-standard.com/insights-and-resources/resources/articles/gps-jamming-spoofing-and-hacking
- Stopochkina, I., Novikov, O., Voitsekhovskyi, A., Ilin, M., Ovcharuk, M. (2025). Simulation of UAV networks on the battlefield, taking into account cyber- physical influences that affect availability. Theoretical and Applied Cybersecurity, 6 (2). https://doi.org/10.20535/tacs.2664-29132024.2.318182
- Pro zviazok vid Serhiya Flesh. Available at: https://t.me/s/serhii_flash
- McNabb, M (2024). What Kind of Drones is Ukraine Buying? DroneLife. Available at: https://dronelife.com/2024/11/04/what-kind-of-drones-is-ukraine-buying/
- Code and data for the paper: "Simulation of Unmanned Aerial Vehicles Networks under Electronic Warfare and Malware Propagation Conditions". Available at: https://github.com/KryvavyiPotii/drone-network
Downloads
Published
How to Cite
Issue
Section
License
Copyright (c) 2025 Anton Tyshchenko, Iryna Stopochkina

This work is licensed under a Creative Commons Attribution 4.0 International License.
The consolidation and conditions for the transfer of copyright (identification of authorship) is carried out in the License Agreement. In particular, the authors reserve the right to the authorship of their manuscript and transfer the first publication of this work to the journal under the terms of the Creative Commons CC BY license. At the same time, they have the right to conclude on their own additional agreements concerning the non-exclusive distribution of the work in the form in which it was published by this journal, but provided that the link to the first publication of the article in this journal is preserved.
A license agreement is a document in which the author warrants that he/she owns all copyright for the work (manuscript, article, etc.).
The authors, signing the License Agreement with TECHNOLOGY CENTER PC, have all rights to the further use of their work, provided that they link to our edition in which the work was published.
According to the terms of the License Agreement, the Publisher TECHNOLOGY CENTER PC does not take away your copyrights and receives permission from the authors to use and dissemination of the publication through the world's scientific resources (own electronic resources, scientometric databases, repositories, libraries, etc.).
In the absence of a signed License Agreement or in the absence of this agreement of identifiers allowing to identify the identity of the author, the editors have no right to work with the manuscript.
It is important to remember that there is another type of agreement between authors and publishers – when copyright is transferred from the authors to the publisher. In this case, the authors lose ownership of their work and may not use it in any way.








