Development of a model of the useful effect of the system at different levels of subsystem interchangeability in the problem of optimizing the allocation of a limited resource
DOI:
https://doi.org/10.15587/1729-4061.2025.342299Keywords:
scalar convolution, resource optimization, utility effect, optimal solution trajectories, cybersecurity, information systemsAbstract
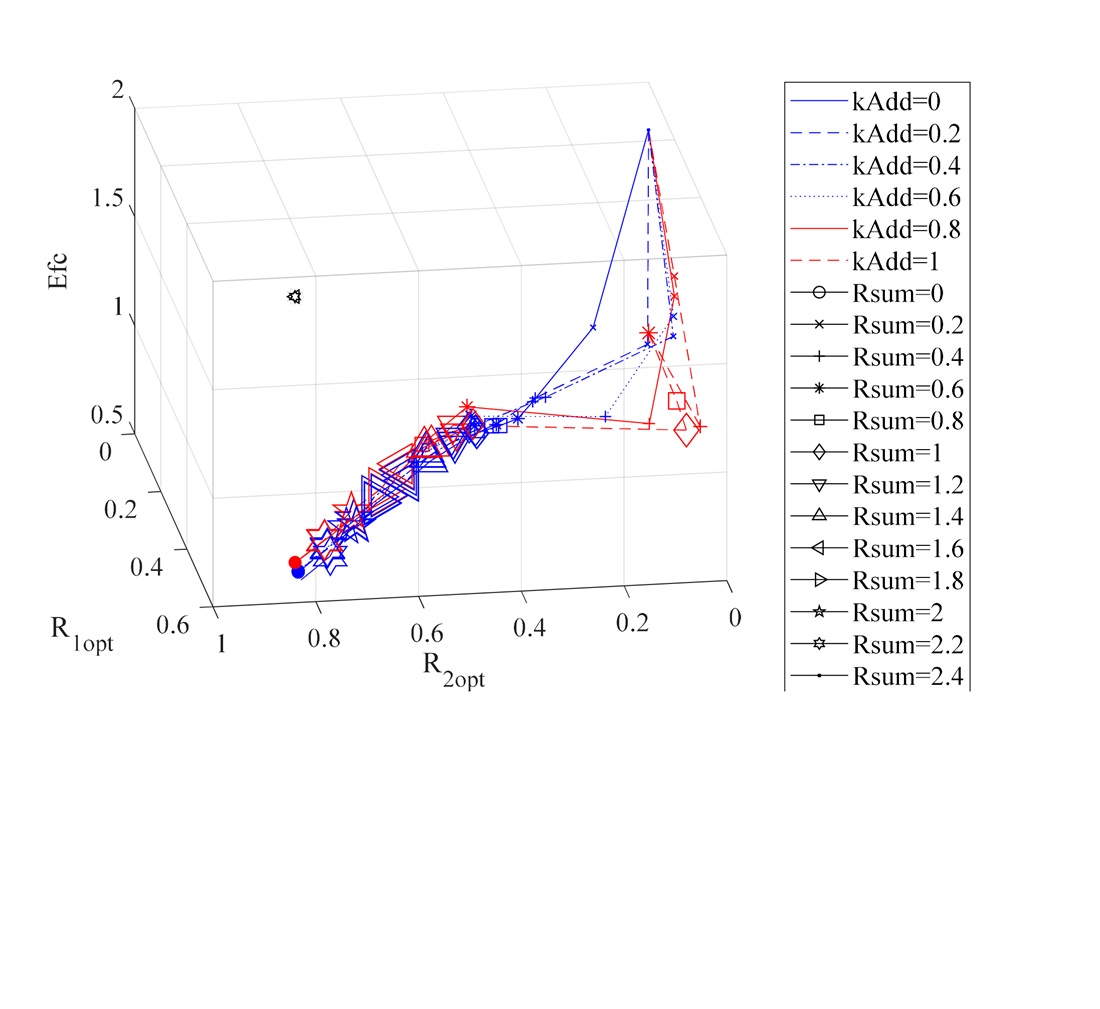
The object of this study is the process of optimizing the allocation of limited resources among the subsystems of a large complex system. The problem addressed lies in the insufficient adequacy of existing utility models, which fail to account for the degree of subsystem interchangeability and therefore cannot accurately predict optimal resource distribution. The core result is the development of a universal utility model based on logistic dependencies and a flexible scalar convolution constructed using a modified marginal Kolmogorov-Gabor polynomial with the coefficient kAdd, which governs interchangeability. Complete trajectories of optimal solutions were obtained for various values of total resources and interchangeability levels. It was found that variations in these parameters alter the optimal effect by 25–35% under conditions of significant resource scarcity. The problem was resolved by combining the universality of logistic models with the flexibility of the new convolution, which generalizes additive, multiplicative, and minimizing forms and enables continuous adjustment of the model to reflect subsystem interaction characteristics. The observed patterns indicate that at low interchangeability, resources are distributed more evenly, while at high interchangeability, they are concentrated in the most efficient subsystem, significantly enhancing the overall effect under resource deficit conditions. The results are applicable to the design and management of large complex systems – such as IT security, crisis management, and organizational design – where informed decisions are required regarding the allocation of limited resources while considering structural flexibility. This approach is particularly suitable when statistical data are available for calibrating the logistic parameters of subsystems and assessing their interchangeability
References
- Bova, Y., Ismahilov, A., Syvachenko, I. (2024). Models and methods of assessing software information security in conditions of limited computing resources. Transactions of Kremenchuk Mykhailo Ostrohradskyi National University, 146 (3), 79–85. https://doi.org/10.32782/1995-0519.2024.3.11
- Zhebka, V., Tkachenko, O., Zhebka, V. (2020). Factor analysis of the effectiveness of regional production development processes. International scientific journal «Danish Scientific Journal», 35 (4), 17–21. Available at: https://www.danish-journal.com/wp-content/uploads/2024/03/DSJ_35_4.pdf
- Khmelevskoy, R., Laptiev, S., Laptievа, T. (2021). Improving the Method of Assessing the Information Security of Computer Systems from Malicious Software. International Journal of Science and Engineering Investigations (IJSEI), 10 (113), 43–48. Available at: https://www.ijsei.com/papers/ijsei-1011321-07.pdf
- Bychkov, A. S., Navotna, V., Shevchenko, V. I., Shevchenko, A. V. (2019). Improvement of the Model of Computer Epidemics Based on Expanding the Set of Possible States of the Information Systems Objects. Journal of Automation and Information Sciences, 51 (11), 34–49. https://doi.org/10.1615/jautomatinfscien.v51.i11.40
- Bychkov, A. S., Dimitrov, G. P., Shevchenko, V. L., Shevchenko, A. V. (2020). Perfection of Computer Epidemic Model by Estimation of Functional Stability of the Information System. Journal of Automation and Information Sciences, 52 (1), 29–40. https://doi.org/10.1615/jautomatinfscien.v52.i1.40
- Shevchenko, V. L., Nesterenko, O. V., Netesin, I. Ye., Shevchenko, A. V. (2019). Prohnostychne modeliuvannia kompiuternykh virusnykh epidemiy. Kyiv: UkrNTs RIT, 152. Available at: http://e.ieu.edu.ua/handle/123456789/647
- Syvytsky, Y., Shevchenko, V. (2024). Computer Simulation Model of the Organization at the Stage of Transformation for the Purpose of Adaptation to New Projects. 14th International Scientific and Practical Conference from Programming UkrPROG’2024, 421–433. Available at: https://ceur-ws.org/Vol-3806/S_61_Shevchenko_Syvytskyi.pdf
- Sobchuk, V., Laptiev, S., Laptievа, T., Barabash, O., Drobyk, O., Sobchuk, A. (2024). A modified method of spectral analysis of radio signals using the operator approach for the fourier transform. Informatyka, Automatyka, Pomiary w Gospodarce i Ochronie Środowiska, 14 (2), 56–61. https://doi.org/10.35784/iapgos.5783
- Datta, S., Kapoor, R., Mehta, P. (2023). A multi-objective optimization model for outpatient care delivery with service fairness. Business Process Management Journal, 29 (3), 630–652. https://doi.org/10.1108/bpmj-07-2022-0335
- Fedushko, S., Molodetska, K., Syerov, Y. (2023). Analytical method to improve the decision-making criteria approach in managing digital social channels. Heliyon, 9 (6), e16828. https://doi.org/10.1016/j.heliyon.2023.e16828
- Yevseiev, S., Ponomarenko, V., Laptiev, O., Milov, O., Korol, O., Milevskyi, S., Pohasii, S. et al. (2021). Synergy of building cybersecurity systems. Kharkiv: TECHNOLOGY CENTER PC. https://doi.org/10.15587/978-617-7319-31-2
- Bakaiev, O., Syvachenko, I., Shevchenko, V. (2024). Scalarization of the vector criterion of information system survivability based on information security indicators. Proceedings of the Cybersecurity Providing in Information and Telecommunication Systems II (CPITS-II 2024), 294–300. Available at: https://ceur-ws.org/Vol-3826/short20.pdf
- Shevchenko, V. L. (2011). Optymizatsiyne modeliuvannia v stratehichnomu planuvanni. Kyiv: TsVSD NUOU, 283.
- Ivakhnenko, A. G. (1971). Polynomial Theory of Complex Systems. IEEE Transactions on Systems, Man, and Cybernetics, SMC-1 (4), 364–378. https://doi.org/10.1109/tsmc.1971.4308320
- Qian, N., Gao, J., Li, Z., Yan, Z., Feng, Y., Yan, Z., Yang, L. (2024). Bridging the Terrestrial Water Storage Anomalies between the GRACE/GRACE-FO Gap Using BEAST + GMDH Algorithm. Remote Sensing, 16 (19), 3693. https://doi.org/10.3390/rs16193693
- Achite, M., Katipoğlu, O. M., Kartal, V., Sarıgöl, M., Jehanzaib, M., Gül, E. (2025). Advanced Soft Computing Techniques for Monthly Streamflow Prediction in Seasonal Rivers. Atmosphere, 16 (1), 106. https://doi.org/10.3390/atmos16010106
- Guide to the Project Management Body of Knowledge (PMBOK® Guide)–Sixth Edition (2017). Project Management Institute.
- A Guide to the Project Management Body of Knowledge PMBOK, 7-th edition (2021). Project Management Institute, Inc., 370. Available at: https://tegnum.edu.pe/wp-content/uploads/2023/09/Project-Management-Institute-A-Guide-to-the-Project-Management-Body-of-Knowledge-PMBOK-R-Guide-PMBOK%C2%AE%EF%B8%8F-Guide-Project-Management-Institute-2021.pdf
- Antunes, M., Maximiano, M., Gomes, R., Pinto, D. (2021). Information Security and Cybersecurity Management: A Case Study with SMEs in Portugal. Journal of Cybersecurity and Privacy, 1 (2), 219–238. https://doi.org/10.3390/jcp1020012
- Handri, E. Y., Putro, P. A. W., Sensuse, D. I. (2023). Evaluating the People, Process, and Technology Priorities for NIST Cybersecurity Framework Implementation in E-Government. 2023 IEEE International Conference on Cryptography, Informatics, and Cybersecurity (ICoCICs), 82–87. https://doi.org/10.1109/icocics58778.2023.10277024
- Fedoriienko, V. (2021). Model of the special software development and modification based on account factors of complexity, workability, qualification of programmers and resource limitations. Political Science and Security Studies Journal. Przeworsk, 2 (2), 94–104. https://doi.org/10.5281/zenodo.5544382
- Rabchun, D. I. (2015). Otsinka efektyvnosti informatsiynoi bezpeky z urakhuvanniam ekonomichnykh pokaznykiv. Suchasnyi zakhyst informatsiyi, 4, 91–96. Available at: https://journals.dut.edu.ua/index.php/dataprotect/article/view/429/397
- Shevchenko, V., Shevchenko, A., Fedorenko, R., Shmorhun, Y., Hrebennikov, A. (2019). Designing of Functionally Stable Information Systems Optimal for a Minimum of Losses. 2019 IEEE 15th International Conference on the Experience of Designing and Application of CAD Systems (CADSM), 1–5. https://doi.org/10.1109/cadsm.2019.8779299
- Sridhar, S. Exhaustive Searching and Combinatorial Optimization Problems. Available at: https://ebooks.inflibnet.ac.in/csp5/chapter/exhaustive-searching-and-combinatorial-optimization-problems/
- Svynchuk, O., Barabash, O., Nikodem, J., Kochan, R., Laptiev, O. (2021). Image Compression Using Fractal Functions. Fractal and Fractional, 5 (2), 31. https://doi.org/10.3390/fractalfract5020031
Downloads
Published
How to Cite
Issue
Section
License
Copyright (c) 2025 Viktor Shevchenko, Yuriy Syvytsky, Yevhen Derevianko, Oleh Bakaiev, Olha Korol, Serhii Pohasii, Serhiy Laptiev, Tetyana Laptieva, Khazail Rzayev, Oleksii Komar

This work is licensed under a Creative Commons Attribution 4.0 International License.
The consolidation and conditions for the transfer of copyright (identification of authorship) is carried out in the License Agreement. In particular, the authors reserve the right to the authorship of their manuscript and transfer the first publication of this work to the journal under the terms of the Creative Commons CC BY license. At the same time, they have the right to conclude on their own additional agreements concerning the non-exclusive distribution of the work in the form in which it was published by this journal, but provided that the link to the first publication of the article in this journal is preserved.
A license agreement is a document in which the author warrants that he/she owns all copyright for the work (manuscript, article, etc.).
The authors, signing the License Agreement with TECHNOLOGY CENTER PC, have all rights to the further use of their work, provided that they link to our edition in which the work was published.
According to the terms of the License Agreement, the Publisher TECHNOLOGY CENTER PC does not take away your copyrights and receives permission from the authors to use and dissemination of the publication through the world's scientific resources (own electronic resources, scientometric databases, repositories, libraries, etc.).
In the absence of a signed License Agreement or in the absence of this agreement of identifiers allowing to identify the identity of the author, the editors have no right to work with the manuscript.
It is important to remember that there is another type of agreement between authors and publishers – when copyright is transferred from the authors to the publisher. In this case, the authors lose ownership of their work and may not use it in any way.








