Reducing the level of message compromise in information transmission systems to virtual private clouds using Shamir's scheme
DOI:
https://doi.org/10.15587/1729-4061.2025.348570Keywords:
probability of message compromise, Shamir's secret distribution method, virtual private cloudAbstract
This study investigates processes of message transmission via the Internet to a virtual private cloud using Shamir's scheme.
The evolution of the infocommunication infrastructure has led to an increase in the role of cloud services. As a result, the requirements for information protection along the paths of message delivery to the clouds are increasing.
The task addressed is to reduce the probability of compromising messages transmitted by a communication system.
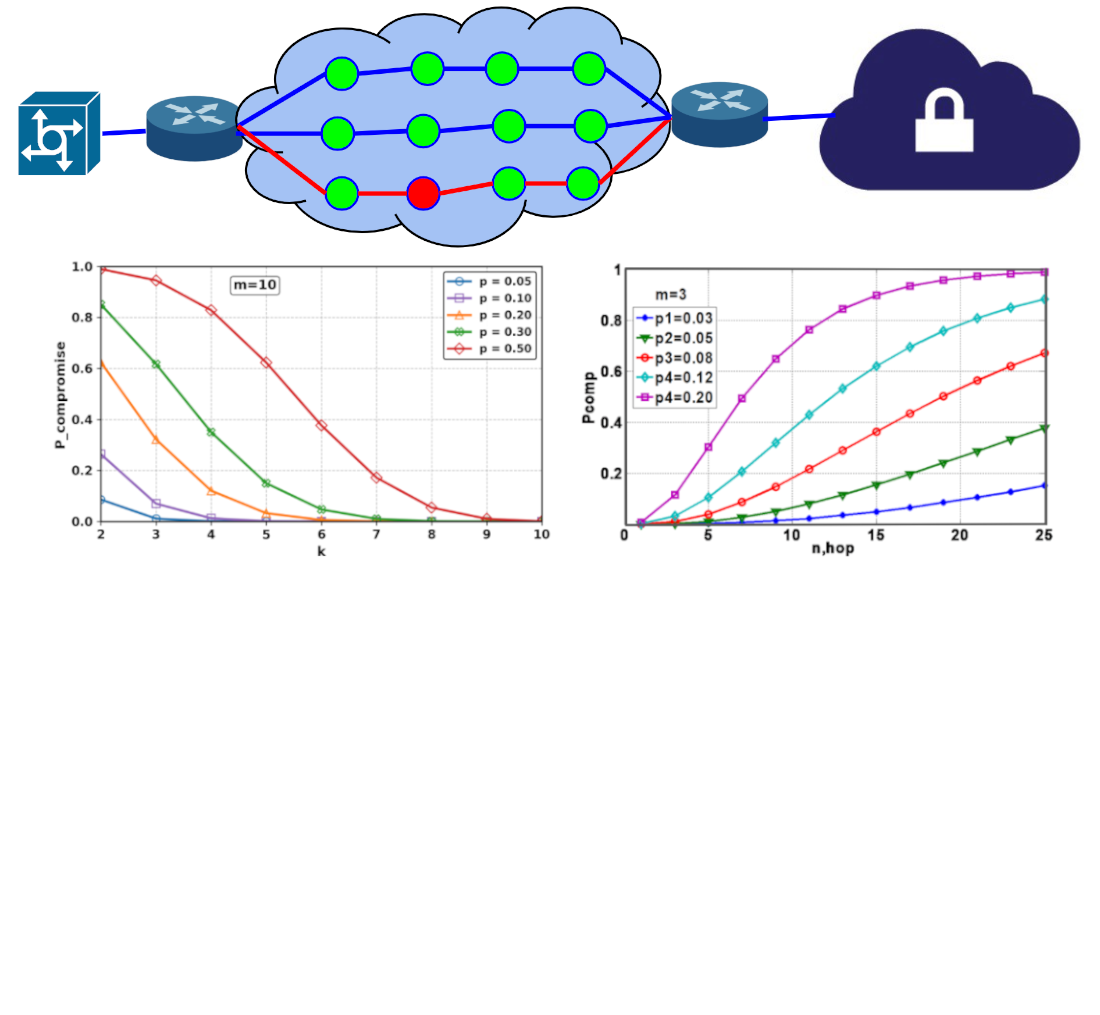
The parameters of the information transmission system that affect the probability of compromise of messages transmitted to the virtual private cloud have been studied. The most vulnerable elements in the communication system were found. To practically implement the Shamir scheme via the Internet, the possibilities of using existing routing technologies were studied.
For information transmission systems with ideal nodes, the overall level of compromise significantly depends on the probability of compromise of one path element, especially for remote clouds. An increase in the probability of compromise on a single hop from 0.03 to 0.1 for 10 hops in a three-path system leads to an increase in the total compromise from 0.02 to 0.28.
Protecting intermediate nodes from attacks is critical for remote clouds. With 10 hops in a three-way communication system, the overall probability of compromise increases fourfold from 0.02 to 0.08 with the same impact of an individual node and hop.
Protecting end nodes for a communication system is of significant importance compared to nodes along the paths. The probability of compromise of end nodes, equal to 0.1, gives an increase in the total level of compromise from 0.03 to 0.21
References
- ISO/IEC 27011:2024. Information security, cybersecurity and privacy protection – Information security controls based on ISO/IEC 27002 for telecommunications organizations. Available at: https://www.iso.org/standard/80584.html
- ISO/IEC 27033-1:2024. Information technology - Security techniques - Network security - Part 1: Overview and concepts. Available at: https://www.evs.ee/en/evs-iso-iec-27033-1-2024
- Shamir, A. (1979). How to share a secret. Communications of the ACM, 22 (11), 612–613. https://doi.org/10.1145/359168.359176
- Lemeshko, O. V., Yeremenko, O. S., Yevdokymenko, M. O., Kovalenko, T. M. (2021). Metodyka rozrakhunku ymovirnosti komprometatsiyi konfidentsiynykh povidomlen pry bezpechniy marshrutyzatsiyi v infokomunikatsiynykh merezhakh z vykorystanniam shliakhiv, yaki peretynaiutsia. Problemy telekomunikatsiy, 2 (29), 15–27. Available at: https://pt.nure.ua/wp-content/uploads/2021/12/212_lemeshko_confidential.pdf
- Lemeshko, O., Yeremenko, O., Yevdokymenko, M., Shapovalova, A., Sleiman, B. (2022). Modeliuvannia ta optymizatsiya protsesiv bezpechnoi ta vidmovostiykoi marshrutyzatsiyi v telekomunikatsiynykh merezhakh. Kharkiv: KhNURE, 198. https://doi.org/10.30837/978-966-659-378-1
- Kato, T., Cheng, S., Yamamoto, R., Ohzahata, S., Suzuki, N. (2018). Proposal and study on implementation of data eavesdropping protection method over Multipath TCP communication using data scrambling and path dispersion. International Journal on Advances in Security, 11 (1&2), 118–126. Available at: https://personales.upv.es/thinkmind/dl/journals/sec/sec_v11_n12_2018/sec_v11_n12_2018_9.pdf
- Dani, V., Nagar, S., Pawar, V. (2022). An Analysis of Multipath TCP for Improving Network Performance. Innovations in Bio-Inspired Computing and Applications, 160–169. https://doi.org/10.1007/978-3-030-96299-9_16
- Popat, K., Kapadia, V. V. (2021). Multipath TCP Security Issues, Challenges and Solutions. Information, Communication and Computing Technology, 18–32. https://doi.org/10.1007/978-3-030-88378-2_2
- Chaturvedi, R. K., Chand, S. (2020). Multipath TCP security over different attacks. Transactions on Emerging Telecommunications Technologies, 31 (9). https://doi.org/10.1002/ett.4081
- Veni, S., Kadhar Nawaz, G. M. (2013). A new Approach to Enhance Security in MPLS network. International Journal of Computer Science and Network Security, 13 (2). Available at: https://scispace.com/pdf/a-new-approach-to-enhance-security-in-mpls-network-3wmckuoafr.pdf
- Alouneh, S., Agarwal, A., En-Nouaary, A. (2009). A novel path protection scheme for MPLS networks using multi-path routing. Computer Networks, 53 (9), 1530–1545. https://doi.org/10.1016/j.comnet.2009.02.001
- Ridwan, M. A., Radzi, N. A. M., Wan Ahmad, W. S. H. M., Abdullah, F., Jamaludin, Md. Z., Zakaria, M. N. (2020). Recent trends in MPLS networks: technologies, applications and challenges. IET Communications, 14 (2), 177–185. https://doi.org/10.1049/iet-com.2018.6129
- Čuřík, P., Ploszek, R., Zajac, P. (2022). Practical Use of Secret Sharing for Enhancing Privacy in Clouds. Electronics, 11 (17), 2758. https://doi.org/10.3390/electronics11172758
- Naz, M., Al-zahrani, F. A., Khalid, R., Javaid, N., Qamar, A. M., Afzal, M. K., Shafiq, M. (2019). A Secure Data Sharing Platform Using Blockchain and Interplanetary File System. Sustainability, 11 (24), 7054. https://doi.org/10.3390/su11247054
- Leon-Garcia, A. (2022). Probability, Statistics, and Random Processes for Electrical Engineering. Pearson, 650. Available at: https://www.goodreads.com/book/show/24331653-probability-statistics-and-random-processes-for-electrical-engineering
- Ross, S. M. (1997). Introduction to Probability Models. Academic Press. 702. https://www-elec.inaoep.mx/~rogerio/IntrodProbabModels.pdf
- Grimmett, G., Stirzaker, D. (2020). Probability and Random Processes. Oxford University Press, 688. Available at: https://global.oup.com/academic/product/probability-and-random-processes-9780198847595?cc=ua&lang=en&
- Types of Static Routes Explained. Available at: https://www.computernetworkingnotes.com/ccna-study-guide/types-of-static-routes-explained.html
- Static Routing vs. Dynamic Routing: What's the Difference? (2025). Available at: https://www.indeed.com/career-advice/career-development/dynamic-routing-vs-static-routing
- MPLS Configuration Guide, Cisco IOS XE 17.x. Available at: https://www.cisco.com/c/en/us/td/docs/routers/ios/config/17-x/mpls/b-mpls/m_mp-te-autotunnel-0.html
- Monge, A. S., Szarkowicz, K. G. (2015). MPLS in the SDN Era. O’RELLY, 920.
- Song L. (2022). Set Up Your Own IPsec VPN, OpenVPN and WireGuard Server (Build Your Own VPN). Amazon, 147. Available at: https://www.amazon.com/IPsec-OpenVPN-WireGuard-Server-Build/dp/B0BQ99KH38
- Bhalerao, V., Sarode, S. (2021). A Review Paper on MPLS L3 VPNs Architecture. International Journal of Scientific and Research Publications (IJSRP), 11 (6), 524–527. https://doi.org/10.29322/ijsrp.11.06.2021.p11469
- Goransson, P., Black, C. (2014), Software Defined Networks. A Comprehensive Approach. Elsevier, 436. https://doi.org/10.1016/c2013-0-00167-3
- ECMP. Available at: https://www.cisco.com/c/en/us/td/docs/security/cdo/cloud-delivered-firewall-management-center-in-cdo/managing-firewall-threat-defense-services-with-cisco-defense-orchestrator/m-routing-ecmp.pdf
- Equal Cost Multipath Load Sharing - Hardware ECMP. Docs Hub. Available at: https://docs.nvidia.com/networking-ethernet-software/cumulus-linux-44/Layer-3/Routing/Equal-Cost-Multipath-Load-Sharing-Hardware-ECMP/
- AWS networking and content delivery. Additional ECMP Paths. Available at: https://000092.awsstudygroup.com/4-transitgatewayandvpn/4.4-ecmppaths/
Downloads
Published
How to Cite
Issue
Section
License
Copyright (c) 2025 Artem Marchuk, Tetiana Kovalenko, Svitlana Shtangey, Olena Linnyk

This work is licensed under a Creative Commons Attribution 4.0 International License.
The consolidation and conditions for the transfer of copyright (identification of authorship) is carried out in the License Agreement. In particular, the authors reserve the right to the authorship of their manuscript and transfer the first publication of this work to the journal under the terms of the Creative Commons CC BY license. At the same time, they have the right to conclude on their own additional agreements concerning the non-exclusive distribution of the work in the form in which it was published by this journal, but provided that the link to the first publication of the article in this journal is preserved.
A license agreement is a document in which the author warrants that he/she owns all copyright for the work (manuscript, article, etc.).
The authors, signing the License Agreement with TECHNOLOGY CENTER PC, have all rights to the further use of their work, provided that they link to our edition in which the work was published.
According to the terms of the License Agreement, the Publisher TECHNOLOGY CENTER PC does not take away your copyrights and receives permission from the authors to use and dissemination of the publication through the world's scientific resources (own electronic resources, scientometric databases, repositories, libraries, etc.).
In the absence of a signed License Agreement or in the absence of this agreement of identifiers allowing to identify the identity of the author, the editors have no right to work with the manuscript.
It is important to remember that there is another type of agreement between authors and publishers – when copyright is transferred from the authors to the publisher. In this case, the authors lose ownership of their work and may not use it in any way.








