Розробка алгоритму квантового обчислення технології моніторингу результатів навчання
DOI:
https://doi.org/10.15587/1729-4061.2024.306968Ключові слова:
квантовий алгоритм, кубіт, заплутаність, технологія розпізнавання обличь, прокторінг, освітнє середовищеАнотація
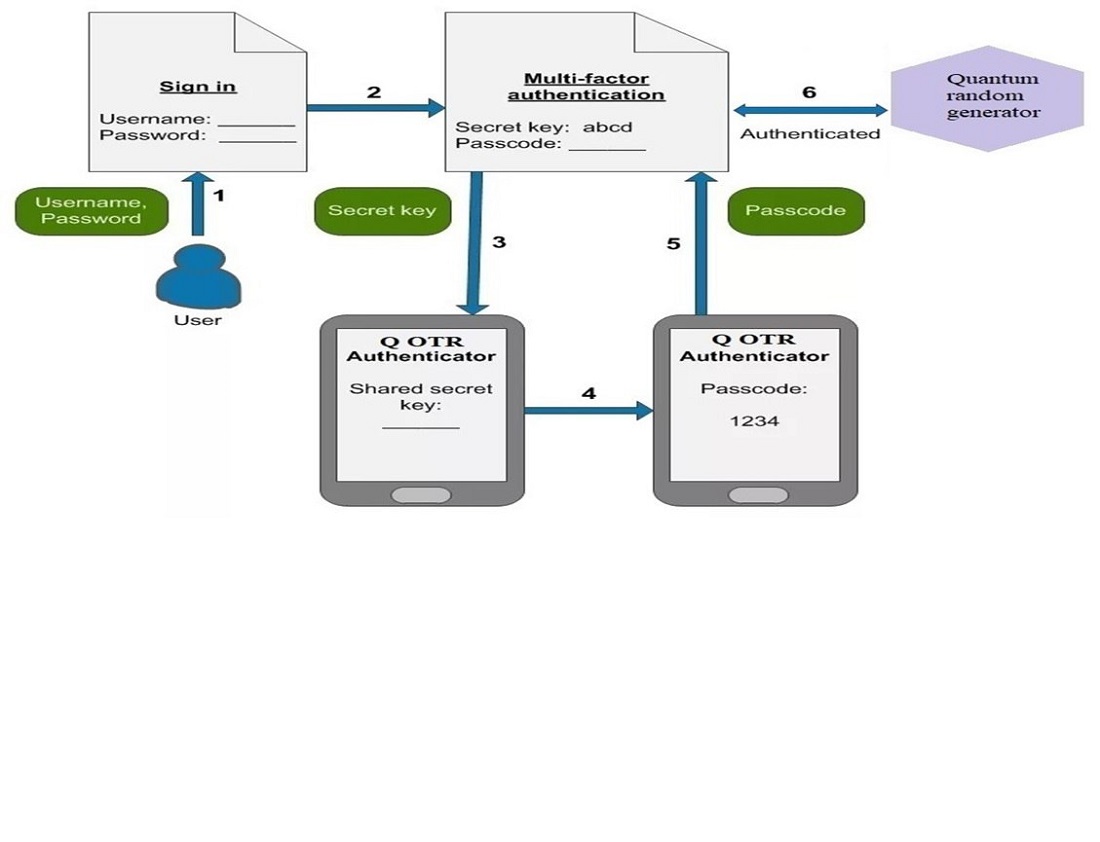
У даній публікації розглядається впровадження системи онлайн контролю з можливістю використання методів і моделей розпізнавання образів з використанням алгоритмічних квантових обчислень для проведення онлайн іспитів. Об’єктом дослідження є метод захисту в системі захисту інфраструктури в освіті. Дослідження спрямоване на створення системи безпеки для захисту технологічної інфраструктури в освіті. У статті запропоновано альтернативний підхід до побудови систем захисту з ефективною моделлю розпізнавання з використанням алгоритмічних квантових обчислень у прокторінгових платформах. У цьому дослідженні розглядаються ці проблеми та пропонується новий підхід до генерації випадкового криптографічного ключа за допомогою мультимодальної біометричної технології. Представлений метод квантового алгоритму для комп’ютерного моделювання квантових принципів обробки даних дозволяє вивчити та проаналізувати, як працює створена модель перетворення класичного зображення у квантовий стан. Цей метод також показує можливості квантової теорії інформації в інтерпретації класичних проблем або як їх оптимізувати, беручи до уваги розробку методів функціонування моделей і алгоритмів для квантових обчислень, захисту даних і безпеки онлайн-відеозмов у прокторингу системи в освітньому середовищі. Новизна даного дослідження виражається, насамперед, у постійному оновленні та доповненні систем аутентифікації з використанням квантових обчислень у різних аспектах, включаючи систему прокторінгу в освітньому середовищі. Також наукова новизна пов’язана з недостатньою кількістю подібних досліджень в інформаційному просторі. Практична значущість обумовлена необхідністю в поточній ситуації привернути увагу до існуючих проблем у структуруванні інфраструктури системи моніторингу в рамках планування та координації захисту, тим самим покращуючи результати навчання шляхом усунення недоліків безпеки за допомогою квантового обчислювального алгоритму для розпізнавання образів
Посилання
- Tajane, K., Gomsale, A., Gomsale, A., Yadav, A., Walzade, S. (2023). Online Exam Proctoring System. International Journal of Advanced Research in Science, Communication and Technology, 3 (1), 202–207. https://doi.org/10.48175/ijarsct-9027
- Ganar, E. S., Mohammad, S., Zohair, K., Shaikh, R. (2023). Online Exam Proctoring System. International Journal of Advanced Research in Science, Communication and Technology, 3 (5), 138–142. https://doi.org/10.48175/ijarsct-9334
- Felsinger, D. N., Halloluwa, T., Fonseka, C. L. I. (2023). Experiences of conducting online exam proctoring in low-resource settings: a Sri Lankan case study. Information Technologies and Learning Tools, 93 (1), 163–177. https://doi.org/10.33407/itlt.v93i1.5094
- Sharma, P. (2023). Proctoring and Monitoring-Based Examination System. International Journal for Research in Applied Science and Engineering Technology, 11 (6), 73–79. https://doi.org/10.22214/ijraset.2023.51899
- Page, M. J., McKenzie, J. E., Bossuyt, P. M., Boutron, I., Hoffmann, T. C., Mulrow, C. D. et al. (2021). The PRISMA 2020 statement: an updated guideline for reporting systematic reviews. Systematic Reviews, 10 (1). https://doi.org/10.1186/s13643-021-01626-4
- Kitchenham, B., Brereton, P. (2013). A systematic review of systematic review process research in software engineering. Information and Software Technology, 55 (12), 2049–2075. https://doi.org/10.1016/j.infsof.2013.07.010
- Barrio, F. (2022). Legal and Pedagogical Issues with Online Exam Proctoring. European Journal of Law and Technology, 13 (1). Available at: https://ejlt.org/index.php/ejlt/article/view/886
- Baso, Y. S. (2022). Proctoring and Non-proctoring Systems. International Journal of Advanced Computer Science and Applications, 13 (6). https://doi.org/10.14569/ijacsa.2022.0130610
- Hussein, M. J., Yusuf, J., Deb, A. S., Fong, L., Naidu, S. (2020). An Evaluation of Online Proctoring Tools. Open Praxis, 12 (4), 509. https://doi.org/10.5944/openpraxis.12.4.1113
- Alessio, H. M., Malay, N. J., Maurer, K., Bailer, A. J., Rubin, B. (2017). Examining the Effect of Proctoring on Online Test Scores. Online Learning, 21 (1). https://doi.org/10.24059/olj.v21i1.885
- Kolski, T., Weible, J. L. (2019). Do Community College Students Demonstrate Different Behaviors from Four-Year University Students on Virtual Proctored Exams? Community College Journal of Research and Practice, 43 (10-11), 690–701. https://doi.org/10.1080/10668926.2019.1600615
- Conijn, R., Kleingeld, A., Matzat, U., Snijders, C. (2022). The fear of big brother: The potential negative side‐effects of proctored exams. Journal of Computer Assisted Learning, 38 (6), 1521–1534. https://doi.org/10.1111/jcal.12651
- Han, S., Nikou, S., Yilma Ayele, W. (2023). Digital proctoring in higher education: a systematic literature review. International Journal of Educational Management, 38 (1), 265–285. https://doi.org/10.1108/ijem-12-2022-0522
- Nurpeisova, A., Shaushenova, A., Mutalova, Z., Ongarbayeva, M., Niyazbekova, S., Bekenova, A. et al. (2023). Research on the Development of a Proctoring System for Conducting Online Exams in Kazakhstan. Computation, 11 (6), 120. https://doi.org/10.3390/computation11060120
- Hernandez-de-Menendez, M., Morales-Menendez, R., Escobar, C. A., Arinez, J. (2021). Biometric applications in education. International Journal on Interactive Design and Manufacturing (IJIDeM), 15 (2-3), 365–380. https://doi.org/10.1007/s12008-021-00760-6
- A model of training in information security technologies in the context of globalization (2022). Certificate of entry of information into the State register of rights to objects protected by copyright of the Republic of Kazakhstan, No. 29025.
- Deutsch, D. (1985). Quantum theory, the Church-Turing principle and the universal quantum computer. Proceedings of the Royal Society of London. A. Mathematical and Physical Sciences, 400 (1818), 97–117. https://doi.org/10.1098/rspa.1985.0070
- Nielsen, M. A., Chuang, I. L. (2010). Quantum Computation and Quantum Information. Cambridge: Cambridge University Press. https://doi.org/10.1017/cbo9780511976667
- Shor, P. W. (1994). Algorithms for quantum computation: discrete logarithms and factoring. Proceedings 35th Annual Symposium on Foundations of Computer Science. https://doi.org/10.1109/sfcs.1994.365700
- Easttom, W. (2021). Quantum Computing and Cryptography. Modern Cryptography, 385–390. https://doi.org/10.1007/978-3-030-63115-4_19
- Bennett, C. H. (1992). Quantum cryptography using any two nonorthogonal states. Physical Review Letters, 68 (21), 3121–3124. https://doi.org/10.1103/physrevlett.68.3121
- Bennink, R. S., Bentley, S. J., Boyd, R. W., Howell, J. C. (2004). Quantum and Classical Coincidence Imaging. Physical Review Letters, 92 (3). https://doi.org/10.1103/physrevlett.92.033601
- Al-Khalid, R. I., Al-Dallah, R. A., Al-Anani, A. M., Barham, R. M., Hajir, S. I. (2017). A Secure Visual Cryptography Scheme Using Private Key with Invariant Share Sizes. Journal of Software Engineering and Applications, 10 (01), 1–10. https://doi.org/10.4236/jsea.2017.101001
- Cao, Y., Li, J., Chakraborty, C., Qin, L., Tao, L., Shao, X. (2023). Temporal Segment Neural Networks-Enabled Dynamic Hand-Gesture Recognition for Industrial Cyber-Physical Authentication Systems. IEEE Systems Journal, 17 (4), 5315–5326. https://doi.org/10.1109/jsyst.2023.3306380
- Li, M., Yang, X., Zhu, H., Wang, F., Li, Q. (2020). Efficient and privacy-preserving online face authentication scheme. Tongxin Xuebao Journal on Communications, 41 (5), 205–214. https://doi.org/10.11959/j.issn.1000-436x.2020087
- Zhang, X., Gonnot, T., Saniie, J. (2017). Real-Time Face Detection and Recognition in Complex Background. Journal of Signal and Information Processing, 08 (02), 99–112. https://doi.org/10.4236/jsip.2017.82007
- Easttom, C., Ibrahim, A., Chefranov, A., Alsmadi, I., Hansen, R. (2020). Towards A Deeper NTRU Analysis: A Multi Modal Analysis. International Journal on Cryptography and Information Security, 10 (2), 11–22. https://doi.org/10.5121/ijcis.2020.10202
- Shaller, A., Zamir, L., Nojoumian, M. (2023). Roadmap of post-quantum cryptography standardization: Side-channel attacks and countermeasures. Information and Computation, 295, 105112. https://doi.org/10.1016/j.ic.2023.105112
- ISO/IEC 19989-2:2020. Information security – Criteria and methodology for security evaluation of biometric systems. Part 2: Biometric recognition performance. Available at: https://www.iso.org/standard/72403.html
- Kim, B. G., Wong, D., Yang, Y. S. (2023). Quantum-Secure Hybrid Blockchain System for DID-Based Verifiable Random Function with NTRU Linkable Ring Signature. International Journal on Cryptography and Information Security, 13 (4), 01–25. https://doi.org/10.5121/ijcis.2023.13401
##submission.downloads##
Опубліковано
Як цитувати
Номер
Розділ
Ліцензія
Авторське право (c) 2024 Galiya Yesmagambetova, Alimbubi Aktayeva, Akky Kubigenova, Aigerim Ismukanova, Tatyana Fomichyova, Seilkhan Zhartanov, Aidyn Daurenova

Ця робота ліцензується відповідно до Creative Commons Attribution 4.0 International License.
Закріплення та умови передачі авторських прав (ідентифікація авторства) здійснюється у Ліцензійному договорі. Зокрема, автори залишають за собою право на авторство свого рукопису та передають журналу право першої публікації цієї роботи на умовах ліцензії Creative Commons CC BY. При цьому вони мають право укладати самостійно додаткові угоди, що стосуються неексклюзивного поширення роботи у тому вигляді, в якому вона була опублікована цим журналом, але за умови збереження посилання на першу публікацію статті в цьому журналі.
Ліцензійний договір – це документ, в якому автор гарантує, що володіє усіма авторськими правами на твір (рукопис, статтю, тощо).
Автори, підписуючи Ліцензійний договір з ПП «ТЕХНОЛОГІЧНИЙ ЦЕНТР», мають усі права на подальше використання свого твору за умови посилання на наше видання, в якому твір опублікований. Відповідно до умов Ліцензійного договору, Видавець ПП «ТЕХНОЛОГІЧНИЙ ЦЕНТР» не забирає ваші авторські права та отримує від авторів дозвіл на використання та розповсюдження публікації через світові наукові ресурси (власні електронні ресурси, наукометричні бази даних, репозитарії, бібліотеки тощо).
За відсутності підписаного Ліцензійного договору або за відсутністю вказаних в цьому договорі ідентифікаторів, що дають змогу ідентифікувати особу автора, редакція не має права працювати з рукописом.
Важливо пам’ятати, що існує і інший тип угоди між авторами та видавцями – коли авторські права передаються від авторів до видавця. В такому разі автори втрачають права власності на свій твір та не можуть його використовувати в будь-який спосіб.









