Development of a model for the analysis and separation of service and useful traffic in cyber-physical systems
DOI:
https://doi.org/10.15587/1729-4061.2025.341734Keywords:
service traffic, industrial protocols, cyber-physical system, cybersecurity, production pyramid, IoT networksAbstract
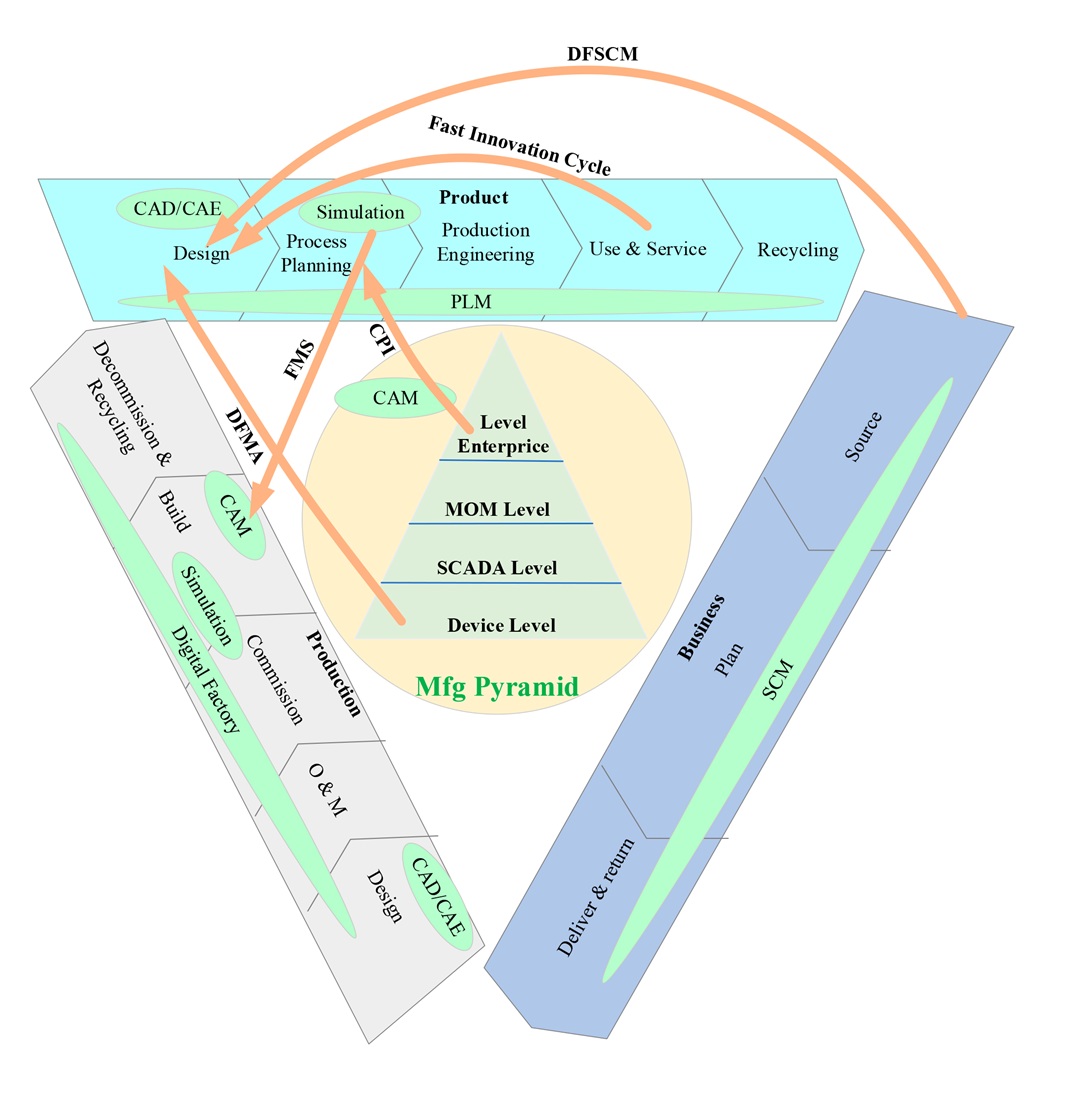
The object of the study is the processes of formation, transmission and processing of service and useful traffic in cyber-physical systems of Smart Manufacturing Ecosystem multi-level architecture type, vulnerable to cyberattacks aimed at compromising control data, authentication and coordination. In modern computer networks, service traffic determines the stability and security of the infrastructure, since any distortion or interception of service traffic can lead to disruption of the system as a whole. In smart systems, industrial Internet of Things and critical infrastructure, the volume of service messages reaches significant scales, because it is they that support the synchronism of thousands of systems in real time.
The paper investigates the problem of protecting service traffic in Smart Manufacturing Ecosystem cyber-physical systems. A mathematical model of service and useful traffic segmentation is proposed, which takes into account the criteria of stability (access segmentation, integrity and authenticity control) and security (probability of compromise, channel criticality, level of trust in the transmission medium). To construct an integral risk indicator, the convolution method is used, which allows combining different types of parameters and determining the feasibility of dividing traffic for target analysis. The study was conducted using industrial protocols Modbus, DNP3, OPC UA, MQTT and HTTP, which are widely used in production networks. It was shown that the use of the model allows reducing the integral risk of attacks on service traffic by an average of 15–20% compared to approaches without segmentation. The developed model forms a scientific basis for creating methods and practical cyber protection solutions that ensure increased resilience of the Smart Manufacturing infrastructure and are able to withstand current and future challenges in the field of cybersecurity
References
- Cybersecurity Statistics. Purplesec. Available at: https://purplesec.us/resources/cybersecurity-statistics/
- ISO/IEC 27032:2023(en). Cybersecurity – Guidelines for Internet security. Available at: https://www.iso.org/obp/ui/#iso:std:iso-iec:27032:ed-2:v1:en
- X.1205 : Overview of cybersecurity (2008). ITU. Available at: https://www.itu.int/rec/t-rec-x.1205-200804-i
- Zakharzhevskyy, A. G., Tolkachov, M. Yu., Dzhenyuk, N. V., Pogasii, S. S., Glukhov, S. I. (2024). The method of protecting information resources based on the semiotic model of cyberspace. Modern Information Security, 57 (1). https://doi.org/10.31673/2409-7292.2024.010007
- Yevseiev, S., Dzheniuk, N., Tolkachov, M., Milov, O., Voitko, T., Prygara, M. et al. (2023). Development of a multi-loop security system of information interactions in socio-cyberphysical systems. Eastern-European Journal of Enterprise Technologies, 5 (9 (125)), 53–74. https://doi.org/10.15587/1729-4061.2023.289467
- Nadhir, A. M., Mounir, B., Abdelkader, L., Hammoudeh, M. (2025). Enhancing Cybersecurity in Healthcare IoT Systems Using Reinforcement Learning. Transportation Research Procedia, 84, 113–120. https://doi.org/10.1016/j.trpro.2025.03.053
- Yin, C., Zhu, Y., Fei, J., He, X. (2017). A Deep Learning Approach for Intrusion Detection Using Recurrent Neural Networks. IEEE Access, 5, 21954–21961. https://doi.org/10.1109/access.2017.2762418
- Lu, Y., Morris, K., Frechette, S. (2016). Current Standards Landscape for Smart Manufacturing Systems. National Institute of Standards and Technology. https://doi.org/10.6028/nist.ir.8107
- Hu, Y., Wendong, W., Xiangyang, G., Liu, C. H., Que, X., Cheng, S. (2014). Control traffic protection in software-defined networks. 2014 IEEE Global Communications Conference, 1878–1883. https://doi.org/10.1109/glocom.2014.7037082
- Barbosa, R. R. R., Sadre, R., Pras, A. (2016). Exploiting traffic periodicity in industrial control networks. International Journal of Critical Infrastructure Protection, 13, 52–62. https://doi.org/10.1016/j.ijcip.2016.02.004
- Kotsiopoulos, T., Radoglou-Grammatikis, P., Lekka, Z., Mladenov, V., Sarigiannidis, P. (2025). Defending industrial internet of things against Modbus/TCP threats: A combined AI-based detection and SDN-based mitigation solution. International Journal of Information Security, 24 (4). https://doi.org/10.1007/s10207-025-01076-2
- Lin, C.-Y., Nadjm-Tehrani, S. (2023). Protocol study and anomaly detection for server-driven traffic in SCADA networks. International Journal of Critical Infrastructure Protection, 42, 100612. https://doi.org/10.1016/j.ijcip.2023.100612
- Anwar, M., Lundberg, L., Borg, A. (2022). Improving anomaly detection in SCADA network communication with attribute extension. Energy Informatics, 5 (1). https://doi.org/10.1186/s42162-022-00252-1
- Griffor, E. R., Greer, C., Wollman, D. A., Burns, M. J. (2017). Framework for cyber-physical systems: volume 1, overview. National Institute of Standards and Technology. https://doi.org/10.6028/nist.sp.1500-201
- Aposemat IoT-23. A labeled dataset with malicious and benign IoT network traffic. Available at: https://www.stratosphereips.org/datasets-iot23
- Kamarei, M., Patooghy, A., Alsharif, A., AlQahtani, A. A. S. (2023). Securing IoT-Based Healthcare Systems Against Malicious and Benign Congestion. IEEE Internet of Things Journal, 10 (14), 12975–12984. https://doi.org/10.1109/jiot.2023.3257543
- Ghadermazi, J., Shah, A., Bastian, N. D. (2025). Towards Real-Time Network Intrusion Detection With Image-Based Sequential Packets Representation. IEEE Transactions on Big Data, 11 (1), 157–173. https://doi.org/10.1109/tbdata.2024.3403394
- Yu, L., Dong, J., Chen, L., Li, M., Xu, B., Li, Z. et al. (2021). PBCNN: Packet Bytes-based Convolutional Neural Network for Network Intrusion Detection. Computer Networks, 194, 108117. https://doi.org/10.1016/j.comnet.2021.108117
- Lazzaro, S., De Angelis, V., Mandalari, A. M., Buccafurri, F. (2024). Is Your Kettle Smarter Than a Hacker? A Scalable Tool for Assessing Replay Attack Vulnerabilities on Consumer IoT Devices. 2024 IEEE International Conference on Pervasive Computing and Communications (PerCom). https://doi.org/10.1109/percom59722.2024.10494466
- IoT Security Risks: Stats and Trends to Know in 2025. JumpCloud. Available at: https://jumpcloud.com/blog/iot-security-risks-stats-and-trends-to-know-in-2025
- Tran, B., Attorney, P. (2025). IoT Security Challenges: Device Vulnerability & Attack Stats. PatentPC. Available at: https://patentpc.com/blog/iot-security-challenges-device-vulnerability-attack-stats
- Censys data reports over 145,000 exposed ICS services worldwide, highlights US vulnerabilities (2024). Industrial Cyber. Available at: https://industrialcyber.co/industrial-cyber-attacks/censys-data-reports-over-145000-exposed-ics-services-worldwide-highlights-us-vulnerabilities/
- Cyberthreats to industrial IoT in the manufacturing sector (2005). PT Security. Available at: https://global.ptsecurity.com/en/research/analytics/cyberthreats-to-industrial-iot/#Navigation-1
- Tolkachov, M., Dzheniuk, N., Yevseiev, S., Lysetskyi, Y., Shulha, V., Grod, I. et al. (2024). Development of a method for protecting information resources in a corporate network by segmenting traffic. Eastern-European Journal of Enterprise Technologies, 5 (9 (131)), 63–78. https://doi.org/10.15587/1729-4061.2024.313158
- Tolkachov, M., Dzheniuk, N., Havrylova, A., Chechui, O., Hapon, A., Tiutiunyk, V. (2025). Cognitive Approach to Cybersecurity: Causality Analysis and Situational Learning. 2025 7th International Congress on Human-Computer Interaction, Optimization and Robotic Applications (ICHORA), 1–4. https://doi.org/10.1109/ichora65333.2025.11017107
- Hrischev, R. (2020). ERP systems and data security. IOP Conference Series: Materials Science and Engineering, 878 (1), 012009. https://doi.org/10.1088/1757-899x/878/1/012009
- Silva, C., Cunha, V. A., Barraca, J. P., Aguiar, R. L. (2023). Analysis of the Cryptographic Algorithms in IoT Communications. Information Systems Frontiers, 26 (4), 1243–1260. https://doi.org/10.1007/s10796-023-10383-9
- Kumar, A., Vishnoi, P., S. L., S. (2019). Smart Grid Security with Cryptographic Chip Integration. EAI Endorsed Transactions on Energy Web, 6 (23), 157037. https://doi.org/10.4108/eai.13-7-2018.157037
- Sudyana, D., Yudha, F., Lin, Y.-D., Lai, C.-H., Lin, P.-C., Hwang, R.-H. (2025). From Flow to Packet: A Unified Machine Learning Approach for Advanced Intrusion Detection. Security and Communication Networks, 2025 (1). https://doi.org/10.1155/sec/5729035
- Zhao, J., Jing, X., Yan, Z., Pedrycz, W. (2021). Network traffic classification for data fusion: A survey. Information Fusion, 72, 22–47. https://doi.org/10.1016/j.inffus.2021.02.009
Downloads
Published
How to Cite
Issue
Section
License
Copyright (c) 2025 Maksym Tolkachov, Nataliia Dzheniuk, Serhii Yevseiev, Yevhen Melenti, Volodymyr Shulha, Serhii Mykus, Ivan Opirskyy, Anton Smirnov, Marharyta Melnyk, Mykhailo Zhyhalov

This work is licensed under a Creative Commons Attribution 4.0 International License.
The consolidation and conditions for the transfer of copyright (identification of authorship) is carried out in the License Agreement. In particular, the authors reserve the right to the authorship of their manuscript and transfer the first publication of this work to the journal under the terms of the Creative Commons CC BY license. At the same time, they have the right to conclude on their own additional agreements concerning the non-exclusive distribution of the work in the form in which it was published by this journal, but provided that the link to the first publication of the article in this journal is preserved.
A license agreement is a document in which the author warrants that he/she owns all copyright for the work (manuscript, article, etc.).
The authors, signing the License Agreement with TECHNOLOGY CENTER PC, have all rights to the further use of their work, provided that they link to our edition in which the work was published.
According to the terms of the License Agreement, the Publisher TECHNOLOGY CENTER PC does not take away your copyrights and receives permission from the authors to use and dissemination of the publication through the world's scientific resources (own electronic resources, scientometric databases, repositories, libraries, etc.).
In the absence of a signed License Agreement or in the absence of this agreement of identifiers allowing to identify the identity of the author, the editors have no right to work with the manuscript.
It is important to remember that there is another type of agreement between authors and publishers – when copyright is transferred from the authors to the publisher. In this case, the authors lose ownership of their work and may not use it in any way.








